Is Cloud Storage Safe From Ransomware?

Is Cloud Storage Safe From Ransomware? With the extensive cloud adoption over the recent years, ransomware actors discovered new opportunities for how to conduct more sophisticated ransomware attacks. Obviously, clouds are not immune to this kind of threat.
As many businesses move their data to the cloud, many questions regarding ransomware protection arise. Some of the most frequently asked ones are:
- Is cloud storage safe from ransomware?
- Is the cloud safe from hackers?
- How does cloud backup help protect against ransomware?
You can read more about what is ransomware in our previous blog posts. This article delves into the intricate landscape of cloud storage security, exploring the prevalent threat of ransomware and unveiling variants targeting cloud environments.
Is Cloud Storage Safe From Ransomware: Cloud Trends and Figures
The global trend for cloud adoption and the recent cloud security statistics of businesses moving their data to cloud give an understanding why hackers would target cloud environments with ransomware variants. According to Tales 2023 Global Security Study which surveyed 3000 respondents in 18 countries cloud security challenges have become a critical element in modern digital infrastructure and services. The following figures show the tremendous growth and cloud adoption trend.
- More than three-quarters (79%) have more than one cloud provider which supports the current trend for hybrid and multi-cloud environments.
- 75% of respondents report that a stunning 40% or more of their data in the cloud is sensitive.
- The reported mean use of SaaS applications has expanded to 97 applications, increasing the attack surface for criminals.
- In addition to this, the number of those who think securing data in
the cloud has become more complex increased to 55% from 46% for just two years.
Accompanied by the rising cloud and multi-cloud adoption trend, there is also an increasing tendency for threats to cloud security, particularly ransomware. For example, ransomware attacks have risen from 37% to more than 66% in the past three years. And this number is expected to further increase.
The cloud is undoubtedly where most business-critical data will be stored in years to come. It makes sense then that the bad guys are taking notice of the trends in enterprise data storage and developing malware, including ransomware, that will target your cloud environments.
Why Cloud Storage is Not Safe from Ransomware
No cloud environment is immune to ransomware. Let’s see how ransomware affects cloud storage and why it may occur:
First, modern enterprises utilize a multitude of cloud-based applications, introducing a myriad of new user identities into their systems which are hard to detect and identify. Despite cloud vendors implementing their identity and access management controls, vulnerabilities persist. Research in cloud security indicates that SaaS apps garnered the most votes as the leading targets for attackers, securing the top spot with 38% of cloud security experts ranking it first. Following closely, cloud-based storage emerged as another prime target, holding the first position according to 36% of respondents. This proliferation creates extensive opportunities for delivering ransomware via malicious apps and extensions.
Second, Ransomware can easily affect files stored in cloud environments due to file synchronization processes that most cloud storages utilize to keep files in sync. When files change locally, these are synchronized to cloud storage. Changes in the files trigger a synchronization action. When ransomware that has infected a local copy of the file starts encrypting the files locally, this action is viewed as a change in the files and triggers synchronization. In this way, a single end-user that is infected with ransomware can inadvertently synchronize encrypted files to cloud storage that may be shared with everyone in the company. As a result, files are encrypted for everyone.
Third, cloud security is a shared responsibility between user organizations and cloud service providers, fostering collaborative security efforts. However, this collaborative approach can sometimes result in security gaps and risk management failures. Misconfigurations are prevalent, leading to inadvertent exposure of sensitive assets to external access or unintentional weakening of controls making data and systems more susceptible to ransomware attacks..
Another challenge involves excessive permissions, where certain identities possess privileges surpassing their actual requirements. Additionally, security professionals grapple with inadequate access key management, emphasizing the necessity for regular changes to thwart potential hackers. Many organizations also face issues in utilizing cloud provider controls effectively, as each vendor operates its own identity and access management system, which might not always align seamlessly with the organization’s IAM systems.
Famous Ransomware Variants Targeting Clouds
Ransomware is one of the biggest cloud security threats. With the accelerating movement of businesses storing critical data in the cloud, almost all ransomware variants consider cloud their main target Let’s take a look at current ransomware variants that have shown they can attack your data in the cloud and utilize cloud-based technologies.
Jigsaw ransomware
Can ransomware infect OneDrive, one may ask? A particular variant of ransomware that has come onto the scene that encrypts local drives, network drives, and cloud storage is the Jigsaw ransomware. Jigsaw ransomware specifically looks for OneDrive storage and encrypts files that are locally synced with OneDrive storage.
It capitalizes on the way cloud storage works by encrypting the local OneDrive storage location, so the encrypted files are synchronized to the cloud. Then, the encrypted files that have been synced to the cloud are then synchronized back down to all nodes connected to the shared OneDrive location.
This is perhaps one of the most dangerous aspects of how cloud storage works is its “Achilles heel.” Although synchronizing files to the cloud from on-premises is a good thing to protect your locally stored data, it provides an easy means to quickly get ransomware from one computer throughout your entire organization via a shared cloud storage location.
CL0P Ransomware
Emerging in 2019 and originating from the CryptoMix ransomware strain, CL0P transformed into a Ransomware as a Service (RaaS). It played a key role in extensive spear-phishing initiatives, employing a verified and digitally signed binary to circumvent system defenses. CL0P is known for employing the ‘double extortion’ strategy, involving the theft and encryption of victim data. It would withhold restoring access to victims and publicly disclose the exfiltrated data.
In late January 2023, the CL0P ransomware group initiated a campaign to target Forta’s GoAnywhere MFT platform. The group asserted that they successfully exfiltrated data from the GoAnywhere MFT platform, affecting around 130 victims within a 10-day period. Altogether, over 100 entities experienced assaults on susceptible GoAnywhere MFT servers, encompassing Procter & Gamble, the City of Toronto, and Community Health Systems, a major healthcare provider in the United States.
In June, the same Clop group targeted another managed file transfer tool — Progress Software’s MOVEit Transfer. This ransomware attack was one of the 2023 largest incidents of the year as it affected numerous organizations, including Shell, the New York City Department of Education, the BBC media corporation, many other companies worldwide.
ALPHV BlackCat
ALPHV Blackcat exploits advanced social engineering techniques and open-source research on a company to gain initial access. Actors pose as company IT and/or helpdesk staff and use phishing, vishing, or SMSishing techniques to obtain credentials from employees to access the target network]. Blackcat affiliates employ URLs to engage in live chats with victims, conveying demands and initiating processes to restore the encrypted files of the victims. Following unauthorized access to a victim’s network, ALPHV Blackcat affiliates utilize remote access software like AnyDesk, Mega Sync, and Splashtop as part of the preparation for data exfiltration.
In its two years of operation, BlackCat successfully infiltrated over a thousand organizations sought over $500 million in ransom from victims, and collected approximately $300 million in ransom payments. At the end of 2023, a collaborative effort involving the FBI, the U.S. Department of Justice, Europol, and law enforcement agencies from multiple European countries dismantled the BlackCat group’s control over its infrastructure.
Petya ransomware
The Petya ransomware made use of cloud infrastructure using Dropbox to propagate the ransomware. Petya ransomware uses Dropbox as a cloud injection tool. Starting out as a phishing email that masquerades as an applicant seeking a job, the email has a link to a Dropbox location that is supposed to contain the resume. However, instead of a resume, it is linked to a self-extracting executable that loads the ransomware onto the unsuspecting end user’s system. The most infamous case of Petya ransomware attacks occurred in June 2017, when a major global cyberattack began against Ukraine, France, Germany, Italy, Poland, the United Kingdom, and the United States. The majority of infections targeted Ukraine, where more than 80 companies were attacked, including the National Bank of Ukraine.
Ransomcloud
A new type of cloud-specific ransomware coined by famous “black hat” hacker turned “white hat” hacker Kevin Mitnick is something he coined as “Ransomcloud”.
In the Ransomcloud attack, hackers can encrypt online email accounts stored in the likes of Office 365 and Google Workspace (G Suite) in real-time. It appears that again, phishing emails are the means that hackers are using to trick end users into clicking infected attachments and links which in turn, start encrypting the cloud inbox of the end-user.
Why Traditional Detection is Not Effective
Cloud data security is based, among other things, on early threat detection. There are various ways that different solutions are used to detect ransomware. These generally fall into one of the following three categories:
- Signature Detection
- Abnormal Traffic Detection
- Abnormal File Behavior Detection
Let’s see briefly how each of these detection mechanisms works.
Signature Detection
One of the oldest ways of detecting malicious files is by using signatures. Traditional antivirus solutions typically leverage this type of detection mechanism.
In simple terms, signature-based detection makes use of a signature for known ransomware and other malware and then can recognize and stop ransomware that matches that signature. You can think of it as a fingerprint of sorts. Once an identification is made based on that signature, the malware is verified and blocked.
The problem and limitation with a signature-based approach is that attackers can change the “signature” of the ransomware by changing the malicious file in such a way that it does not match the “known” signature that would be blocked. This allows hackers to circumvent the signature-based approach to bypass the security measures in place. At this point, using signatures is a traditional and antiquated approach to protecting your data against ransomware.
Abnormal Traffic Detection
Another widely used approach in detecting and blocking ransomware is abnormal traffic detection. Abnormal traffic detection attempts to detect malicious traffic by examining traffic patterns and detecting those patterns that look like ransomware. The weak point of abnormal traffic detection is that it can result in high rates of false positives.
A false positive happens when your cloud storage security solution detects traffic patterns that may appear to be ransomware traffic but are actually legitimate. However, this is not an exact science and can result in legitimate network traffic being blocked that is not truly malware or, specifically, ransomware.
Abnormal File Behavior Detection
Solutions today that can effectively detect and stop advanced ransomware need to use more advanced techniques than traditional signature and traffic detection. Abnormal file behavior detection looks at the file behavior for different types of anomalies to match that behavior with a particular type of malware.
Solutions leveraging machine learning engines that can intelligently differentiate between benign behavior and malicious behavior provide powerful capabilities to businesses looking at stopping ransomware before it destroys significant amounts of business-critical data.
SpinRDR End-to-End Cloud Ransomware Protection
Leveraging automatic, versioned backups of your cloud environments, SpinRDR shows a 99% detection rate and 0 file loss rate. SpinRDR provides a unique approach that combines the best of both cybersecurity and data protection in a single solution if you are looking for cloud ransomware protection.
First, it offers robust cloud backup ransomware protection capabilities. How does cloud backup protect against ransomware? It ensures that your critical data is regularly backed up and protected from ransomware attacks.
Second, SpinRDR leverages ML-based abnormal file behavior detection. Using machine learning, SpinRDR looks at abnormal file behavior to detect ransomware activity in your cloud environment. Once malicious ransomware activity is determined, SpinRDR finds the source of the attack and then revokes access to the attack’s origin.
Finally, SpinRDR still allows the user account access to the environment. In other words, an employee whose user account has been victimized will still have access to their Google Workspace or Office 365 account. Using the machine learning approach that powers the ability to detect abnormal file behavior, SpinRDR can detect and effectively remediate ransomware attacks from even new or zero-day ransomware that begins attacking your environment.
SpinRDR Automated Ransomware File Restoration
With SpinRDR Ransomware Detection & Recovery, you not only get a cybersecurity solution that effectively stops a ransomware attack and blocks the source of the attack but a solution that can restore any data that has been affected. Compared to other solutions that, at best, detect and alert to an attack, SpinRDR takes the following steps to protect and remediate any files that have been encrypted proactively.
With SpinRDR Ransomware Protection, ransomware attacks trigger SpinRDR automated ransomware file restoration, where only files that have been affected by ransomware are restored. This provides a granular, automated approach that proactively protects your environment. SpinRDR’s unique end-to-end solution stands out when compared to other solutions aiming to defend your Software-as-a-Service (SaaS) environments like Google Workspace and Microsoft Office 365.
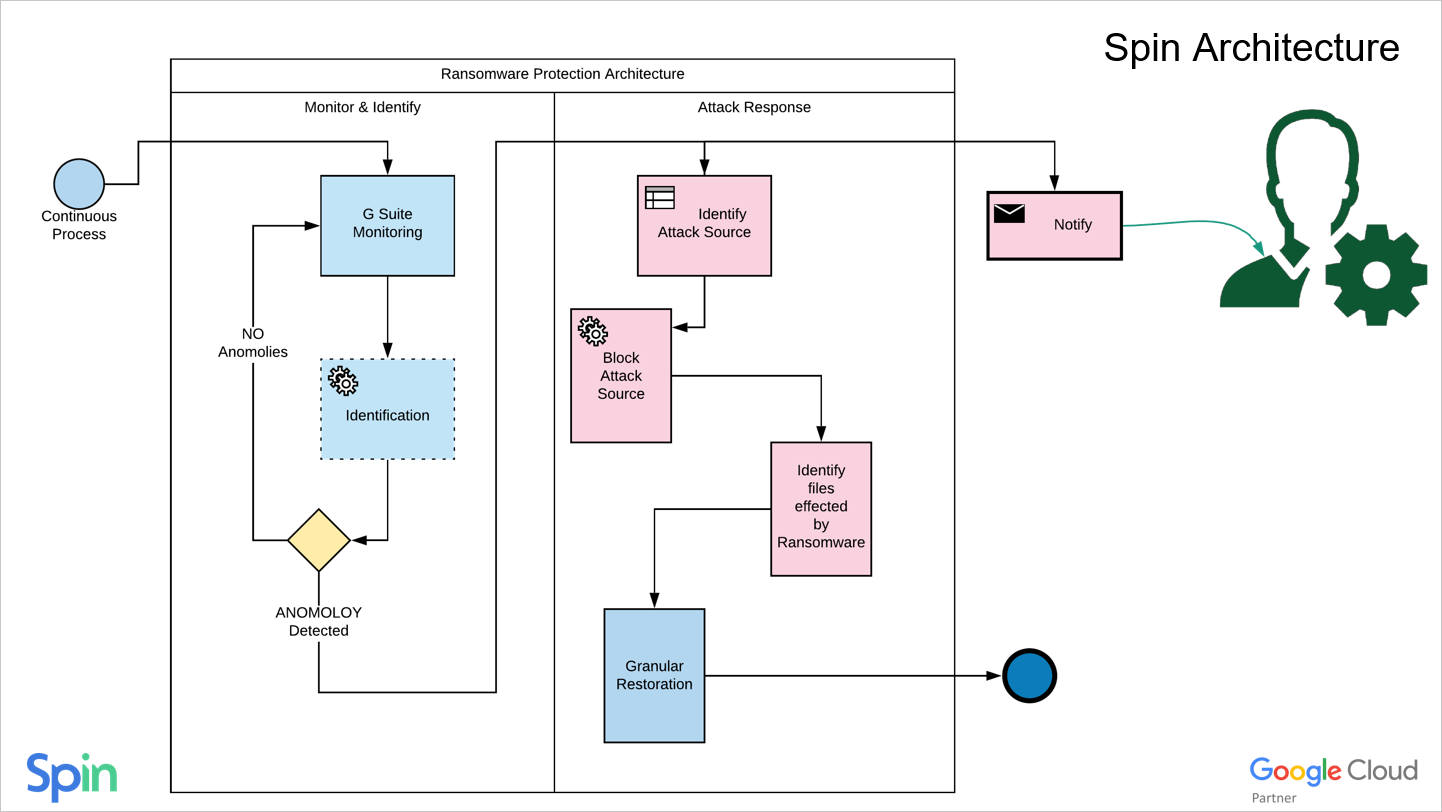
SpinRDR provides the following additional benefits to securing and protecting your cloud environments:
- Automatic, versioned backups
- Third-party apps control
- Intrusion Detection
- Easy Cloud Data migration
- User Behavior Analysis
- Data download analysis and protection
Cloud Storage Security: Wrapping Up
Ransomware continues to be at the top of the list of security concerns for organizations around the world. Protecting your data assets requires that you protect your environments from ransomware at all costs. As shown, ransomware affects not only on-premises environments but also your cloud data storage as well.
SpinRDR is a solution that provides end-to-end protection against ransomware in the cloud by both proactively protecting your cloud environments and automatically remediating any damage as a result of a ransomware process.
Sign up for a fully-featured trial of SpinRDR and check out SpinRDR’s next-generation ransomware protection for the cloud.
Was this helpful?
- Is Cloud Storage Safe From Ransomware: Cloud Trends and Figures
- Why Cloud Storage is Not Safe from Ransomware
- Famous Ransomware Variants Targeting Clouds
- Jigsaw ransomware
- CL0P Ransomware
- ALPHV BlackCat
- Why Traditional Detection is Not Effective
- Abnormal Traffic Detection
- SpinRDR End-to-End Cloud Ransomware Protection
- Cloud Storage Security: Wrapping Up
How Can You Maximize SaaS Security Benefits?
Let's get started with a live demo
Latest blog posts
Microsoft 365 Security Best Practices and Recommendations 2024
February 9, 2024Micorosft 365 is a business-critical cloud environment that contains terabytes of sensitive information. Protecting this... Read more
Importance of Backing Up Google Workspace Data Daily
January 23, 2024Many organizations today are heavily relying on cloud Software-as-a-Service offerings for business productivity, communication, and... Read more
What data can be backed up from Microsoft 365?
January 5, 2024Microsoft 365 services contain business-critical data. However, none of the services has an in-built backup... Read more


