45 Main Cyber Security Terms Everyone Must Know

Cybersecurity is an everyday growing industry, which inevitably infiltrates the day-to-day life of each of us. There are numerous tools, technologies, methods, and attacks in the cybersecurity field. Due to the abundance of these things, the cybersecurity field is one of the hardest to grasp and keep up with.
To help you to understand it a little bit better, we wrote this shortlist of basic cybersecurity terminology and definitions.
Let’s dive in!
Cyber Security Vocabulary: Must-Know List
This cybersecurity terms dictionary will bring some clarity to those words you encountered but couldn’t grasp. Also, this list will make you more aware of the threats that lie in wait for you around every internet corner.
Security

Antivirus – software that scans a device or a network to detect security threats, alert you, and neutralize malicious code.
Authenticator – a method of how a user can prove his/her identity to a system. It can be a password, a fingerprint, a face scan.
Blacklist – a list of emails or other service providers that spread spam messages. Blacklists help users and companies to prevent the flood of unwanted messages.
Backup – a copy of physical or virtual data. In case important data is deleted or lost user could easily recover it. Works as a part of a data loss prevention plan. Learn more about backup.
Closed Source – a proprietary technology whose copyright hides its source code and forbids its distribution or modification. Examples of closed source commercial software are Skype, Java, Opera.
Cloud – computing recourses that make it available to access your files and services through the internet from any point in the world. It is possible thanks to a network of computers that provide storage and computing capabilities by the request.
Data Loss Prevention (DLP) – the complex of security measures, related to detecting and preventing data loss and cyberattacks. DLP is included in the organization’s policy. Individuals need to follow this strategy to keep all business and personal data safe from ransomware or malware attacks.
Data encryption – a way to secure private information by encoding it so no third parties could watch or access it. To read the encoded (encrypted) file, you must decode it by using a decryption key.
Data protection – a set of methods aimed to safeguard private information from getting into the wrong hands.
Exploit – a weak spot in a computer system, which can be used to attack this system.
Firewall – a network security system that filters unsanctioned incoming and outgoing traffic.
Group Authenticator – an application used to allow access to specific data or functions. These may be shared by all members of a particular group.
Honeypot – a technique that is aimed to distract hackers with a fake target (a computer or data) and make them pursue it instead of the real one. It helps to secure a high-value target and observe hackers’ main techniques to learn from them.
IP Address – an address that identifies the connection between your computer and the network provider. Your computer can have multiple IP addresses depending on the number of networks it connects to.
Multiple computers can have one IP address. This can happen if they are connected to the same provider in the same area, like in cafes or at home.
Identity check – a set of actions (a password, a fingerprint, or a face scan) designed for verification of someone’s identity.
Incident response plan – a complex of measures to be taken in case of a cyberattack to reduce damages from the attack. It’s a part of incident response management.
Insider threat – a threat to the company’s data integrity that is coming from someone within the organization. This is usually an employee or another insider.
Open Source – a type of software whose source code is made freely available to anyone to study, modify, and distribute. This means that the code can be viewed and altered by anyone, and the resulting software is often distributed for free. Examples of open-source code are Bitcoin, Mozilla Firefox, Joomla, and WordPress.
Patch – a regular system update that is designed to cover security blunders that have been discovered.
ReCAPTCHA – a system invented by Google that helps determine if a website user is a human or a robot. It is used by websites to prevent bots from spamming.

Shadow IT denotes any IT systems that have been deployed in the organization without the authorization of the IT department. Unauthorized hardware and software can become an entry point for cyber attacks. Cloud applications are one of the most insecure types of shadow IT.
Virtual Private Network (VPN) – technology that extends a private network and all its encryption, security, and functionality across a public network. With it, users can send and receive messages as if they were connected to a private network.
Malware and Ransomware
Adware – Software that automatically displays or downloads material when a user is offline.
DDoS (denial-of-service attack or distributed denial of service) – a type of cyber attack that makes the site user wants to visit unusable by flooding it with malicious traffic.
Keylogger – software that secretly monitors and captures keystrokes user makes. Usually designed to steal credentials and sensitive data. It can also be used for relatively harmless goals like supervising employees’ activities or watching children.
Malware (malicious software) – malicious code that is designed to harm computers and systems. There are many types of malware programs with different goals: to steal or delete user’s information, to steal computing capacities, to spy or to destroy a program.
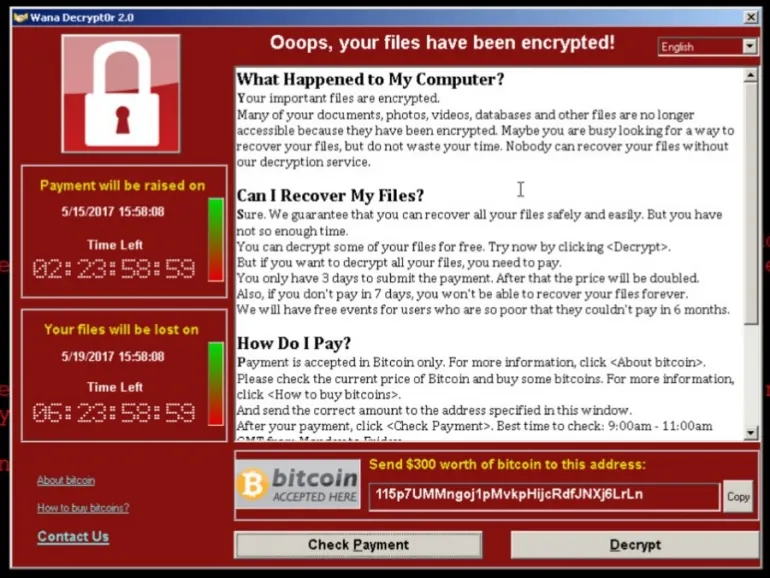
Ransomware – a type of malicious program (malware) that encrypts data so the victim can’t access it without the decryption key. To get one, the victim must pay a ransom, usually within a designated period. You can see how ransomware looks below.
Ransomcloud – a special type of ransomware, designed to encrypt cloud emails and attachments.
Rootkit – a type of malware that is used to seep into the system and steal company information. It can be very thicky to detect because the malware gains control over the operating system and disguises itself. Some companies detect data leaks after months or even years.
Spyware – malware that spies on the computer to collect information about a product, a company, a person. The goals can be different – to sell this information to those who may benefit from it, like the advertisers, competitors, data companies; to obtain the banking information and passwords, and so on. The most widespread spyware are keyloggers and trojans.
Trojan – A form of malicious code that looks like a legitimate file, program, or application, but actually is designed to control the user’s computer and data. It is usually hard to detect until the damages and losses are significant. It can delete, spy, and ask for money for seemingly rightful reasons.
Virus – a type of malware that is aimed to infect and harm a file, a system, or a network. The virus program is usually attached to a harmlessly looking file or app, which eliminates the suspicion by making it look valid and safe. Some viruses can replicate themselves.
Worm – a type of self-replicating malware. When infecting a computer, a worm is aimed to spread across the network to infect others.
A worm can multiply itself to “eat” a computer’s resources, or be sharpened to steal and delete user’s data. It can also provoke general havoc in the system. Worms arrive through system vulnerabilities or clicking on malicious attachments.
Hacking and Social Engineering
Attack vector – a specific method used by a hacker to accomplish his malicious goal.
Advanced Persistent Threats – masterfully executed network intrusion during which a hacker stays undetected while they are stealing data.
Account Hijacking – a type of identity theft, when a hacker hacks and steals someone’s account to perform malicious actions.
Bot – a program that can automatically perform some simple repeated task to reach a pursued goal. Some of the bots are malicious, while others can be beneficial.
Brute force attack – a method for cracking an account password. This is when a hacker uses a cracking machine that can try multiple passwords until it gets the right one.
Crypojacking – when a hacker unauthorisedly uses someone’s computing power to mine cryptocurrency.
Catfishing – when someone uses a social network to create an account with a fake identity to deceit a concrete person.
Cracker – a person, who attacks a specific computer system. Often to steal or corrupt sensitive information or data about a company or a product.
Hacker:
– White Hat Hacker is a cybersecurity expert who tests a system by running mock cyberattacks to discover potential security vulnerabilities.
– Black Hat Hacker is a person who tries to break into a computer system by exploiting cybersecurity vulnerabilities.
Phishing – a wide range of scams when someone impersonates themselves as trustworthy entities in an attempt to obtain information. For example, a user can receive an email from “Google”. The email may ask the user to click on a link. The link may require the user to provide their login, password, or credit card information in the empty fields.
Password Sniffing – a method that used to find out a password by monitoring traffic on a network to pull out information.
Social Engineering – a set of means intended to trick people into giving out sensitive information. This can be banking and credit card details, or personal information. Criminals impersonate themselves as someone trustworthy and use the seemingly legitimate pretext to make a user share data.

*We highlighted in red all warning signs used to identify a phishing email.
You did it! Now you are way more advanced in cybersecurity vocabulary, so you are much less likely to fall for cybercriminals’ bait!
Frequently Asked Questions
What are the 5 functions of cyber security?
The 5 core functions of cybersecurity are identify, protect, detect, respond, and recover. These functions are defined by the NIST Cybersecurity Framework as a widely recognized and adopted set of guidelines for organizations to manage and improve their cybersecurity practices.
What are the 7 areas of cyber security?
Cybersecurity encompasses a wide range of practices and strategies to protect computer systems, networks, and data from various threats. One can distinguish the 7 key areas of focus that organizations typically address:
- Network Security
- Information Security
- Endpoint Security
- Application Security
- Cloud Security
- Identity and Access Management (IAM)
- Security Awareness and Training
Was this helpful?
How Can You Maximize SaaS Security Benefits?
Let's get started with a live demo
Latest blog posts
Protecting Partner Margins: An Inside Look at the New Spin.AI Partn...
April 2, 2024Google recently announced a 40% reduction in the partner margin for Google Workspace renewals –... Read more
Top 10 Salesforce Security Best Practices and Tips
February 28, 2024In the ever-evolving threat landscape, safeguarding sensitive data is paramount. Salesforce, a leading customer relationship... Read more
Microsoft 365 Security Best Practices and Recommendations 2024
February 9, 2024Micorosft 365 is a business-critical cloud environment that contains terabytes of sensitive information. Protecting this... Read more


