4 Cybersecurity Lessons Learned from the Facebook Data Leak

When we stop and think about our data as it exists online, it can contain personal information that we would not want to have exposed. Social media and data privacy has become a very heated subject, especially with the recent Facebook data leak scandal that has been topping news headlines for the past few days. It helps to shed light on an increasingly difficult “fine line” that tech giants and large corporations are treading with our personal data.
Data privacy today is becoming increasingly complex and elusive. It seems in today’s world, everyone has an online presence. This includes various social media accounts, online banking accounts, membership accounts, utility company accounts, service accounts, and the list goes on and on. Even normal everyday users who do only a few things online will have a dozen or more accounts they can call to mind.
What was involved with the Facebook scandal? What can be learned about personal data and how it is shared in ways that we may not realize? How can organizations learn from the Facebook scandal and be proactive about protecting personal information and data leak in general?
Data Leak and Data Loss Meltdown 2018
Both data leak and data loss prove to be extremely costly. While focusing on the Facebook scandal, let’s recap some very notable, high-profile recent data loss and data leak events, happening in the past few days, that show just how costly, disruptive, and destructive data leak and data loss can be.
- Facebook scandal – Recent reports have indicated that Facebook has lost some $50 billion in market cap due to the scandal, with some reports topping $70 billion.
- Boeing – Last Wednesday (3/28) Boeing said it had been hit with a ransomware cyberattack that had rendered an “all hands on deck” situation with the company frantically trying to prevent the spread of the ransomware to production systems and airline software
- Panera Bread – Late breaking as of (4/3), Panera Bread has been leaking customer data on its website for months now. Customer data available in plain text and includes records for customers who signed up to order food via the Panera Bread website (names, emails, addresses, last 4 digits of the credit card used
- City of Atlanta, GA, USA – March 22, 2018 – Hit with a ransomware variant that crippled the entire city of Atlanta and rendered systems across the city useless.
All of the above-mentioned data loss and data leak events have caused tremendous disruption in the flow of normal business operations for these very high-profile organizations. Data loss and data leak can certainly hit any business large or small. The results can be the same – damaged business reputation, lost business, stock plunge, and potentially legal action.
Facebook Scandal – Leaked Member Data – How it Happened
Due to many high-profile security events such as the Facebook scandal, we are entering a new age of awareness concerning data privacy. The Facebook scandal has drawn attention to the subject that most may not want to think about. Who has access to my data? The scandal itself involved a political firm researcher working for Cambridge Analytica who was able to gain access to personal data of 50 million Facebook users.
The political firm developed a quiz app that harvested the data from the users as well as profiles of Facebook friends the users were connected with. The exposure of Facebook user’s data by the quiz app made clear that third-party developers have had access to Facebook user data and could use it in ways that Facebook had no control over.
All of this is in lieu of a comment that Facebook CEO Mark Zuckerberg made some 9 months ago that people share on Facebook because “they know their data is going to be protected”. However, those claims seem to be unfounded with the recent Facebook data leak revelation.
While the data leak was the direct result of a third-party app and the leaking of this data by Cambridge Analytica, Facebook has reaped the bulk of scrutiny over this exposure of user data. The scrutiny comes from the failure of Facebook privacy settings in protecting its users from this type of data exposure.
After the recent data leak from Facebook, Zuckerberg has released several posts detailing Facebook’s commitment to improving data privacy for its users. A late breaking announcement as of 4/3/2018, reveals Facebook has launched a bulk app removal tool to clean up your privacy settings including integrated third-party applications that may have access to your account data.
Facebook Data Leak Scandal: 4 Lessons Learned
There are definitely positive results that can come from today’s data loss and data leak disasters, including the Facebook scandal. These types of events serve to increase the overall awareness of the importance of data privacy and help to develop and strengthen the measures used to protect end user data. Weaknesses are discovered and potential threats to cybersecurity are identified, helping to bolster overall security and privacy.
When analyzing the data leak that resulted from the Facebook scandal and other recent data breaches, there are quite a few lessons that organizations can learn from. It helps to identify key areas that can help companies today bolster data loss and data leak protection. They include the following:
1. Data loss and data leak disasters are extremely costly
As shown with the Facebook scandal, data leak disasters can cost organizations millions or even billions of dollars, ruined reputation, and damaged brand image.
2. Stake holders, consumers, customers, members, and subscribers hold the owner of their data responsible when data is leaked
Even though Cambridge Analytica was ultimately responsible for the actual leak of data from Facebook, the responsibility in the eyes of stakeholders and end users is assumed by the data holder.
3. Third-party apps integrated into cloud-based applications can be risky, or even dangerous
Organizations must scrutinize third-party applications closely and analyze data integrations with company data, and their implications on security.
4. Ransomware is extremely dangerous
It can result in total paralysis of business operations due to compromised systems being inoperable.
There isn’t a single more important possession of organizations today than their data. It underscores the importance of data privacy and the true value on data privacy as well as the importance of protecting against data loss. The notion that our data online is private and only those we choose to share it with have access to it is proving to be a façade.
Along with data leak protection and cybersecurity measures, data protection is necessary. It is extremely likely for most organizations to experience some sort of cybersecurity event in the course of their operation. Making sure data is protected is extremely important.
Data leak and data loss protection as well as cybersecurity are extremely important not only on premise but in the public cloud. Monitoring and managing third-party applications that are integrated into cloud environments is also crucially important as is brought to light by the Facebook scandal. How can organizations protect themselves against these very real threats?
Data Loss, Data Leak, and Cybersecurity for Public Cloud
The recent data loss, data leak, and cybersecurity events that have made headlines as of late all emphasize the need for organizations today being proactive rather than reactive in acting on data loss, data leak, and cybersecurity.
All too often companies find themselves in the news for not taking threats seriously, not addressing vulnerabilities when they were made aware, or not designing systems that ensure data privacy. In fact, one of the key initiatives the new General Data Protection Regulation (GDPR), taking effect in May 2018, will enforce is the “privacy by design” initiative.
This important part of GDPR compliance calls for the “inclusion of data protection from the onset of the designing of systems, rather than an addition”. Privacy, data protection, and security are no longer simply recommended best practice initiatives. They will be required for organizations who want to effectively do business in the coming years in today’s technology-advancing world. How do organizations today take a proactive approach to protecting against data loss, data leak, and ensuring powerful cybersecurity measures in the public cloud?
Spinbackup provides a powerful three-fold approach to help organizations protect against data loss, data leak, and cybersecurity events such as the ones making headlines recently. Spinbackup provides a state-of-the-art, full-on solution to these very complex issues in the Google G Suite public cloud.
In looking at the Facebook scandal, a third-party application integrated with the Facebook environment was responsible for leaking information for some 50 million Facebook users. As mentioned, risky third-party applications integrated into public cloud environments must be viewed as a real threat vector for organizations doing business today. Third-party apps need to be viewed with scrutiny, even if they are distributed by seemingly reputable publishers or sources. Any anomaly in third-party app activity can represent a compromise of company data.
Spinbackup provides a unique and effective approach to controlling risky-third party applications. Let’s highlight the benefits to organizations who utilize Spinbackup to secure their Google G Suite environment.
Spinbackup Risky Third-Party Apps Control
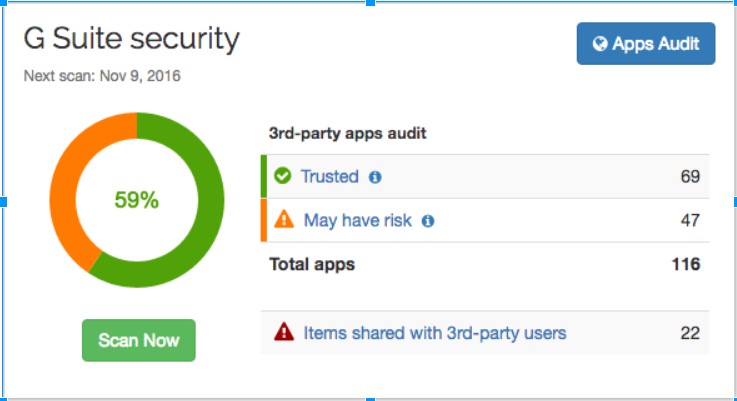
The Third-Party High Risk Apps Control provided by Spinbackup provides a 24/7 automated scanning and monitoring solution that analyzes all third-party applications integrated with the Google G Suite environment. It identifies all third-party apps that have access to data stored in the G Suite cloud. Importantly, it uses cutting-edge machine learning and artificial intelligence to correctly identify and isolate third-party applications that are accessing corporate data in a way that is malicious or are otherwise leaking data outside the organization.
This information is presented in an obvious and efficient way in the Spinbackup dashboard for administrators to have total visibility and control over remediating access for those risky third-party apps. The automated scan and threat intelligence that is baked into the Third-Party Apps Control provides the following benefits:
- Identifies all third-party applications integrated into the G Suite environment
- Determine the type, description, and other information about the app
- Uses Machine Learning algorithms to determine the risk level of the application and its intent
- Identifies the permission levels granted to the third-party app and which user granted those permissions
- Determines the devices from which the third-party application is access the G Suite environment
- Allows configuring a “blacklist” of disallowed third-party applications
Organizations who improperly handle or provide slow responses to data loss, data leak, or cybersecurity events generally suffer the worst outcomes in relation to damaged reputation, customer confidence, and even legal action. Providing quick responses to these types of events is essential for a proactive stance.
Spinbackup’s High Risk Apps Control includes a powerful “Incidents Response Plan” that allows both manual and automated actions to control any attempted data loss or data leak from a third-party app. The Incidence Response Plan features the following capabilities:
-
- Machine Learning profiling of all third-party apps integrated into the G Suite environment
- The ML algorithms are able to identify anomalies in third-party app “behavior”
- Easy access to review and revoke third-party apps that display risky “behavior” with company data
- G Suite administrators receive proactive alerts of any abnormal activities in the G Suite environment, including those from risky third-party apps
- Third-party apps that attempt to automatically download data inappropriately are automatically blocked
- Third-party apps are blocked from migrating data between unapproved public clouds, such as moving the data from the G Suite public cloud to another public cloud provider
The Machine Learning engine that powers Spinbackup data loss, data leak, and cybersecurity is able to accomplish tasks that G Suite administrator would simply not be able to accomplish manually. The 24/7, automated intelligence that Spinbackup provides never sleeps, takes a break, or misses events. It is always on, always watching, and always protecting the G Suite environment from third-party apps and other cybersecurity risks.
Spinbackup G Suite DLP (Data Leak Prevention)
The data leak prevention provided by Spinbackup includes the powerful High Risk Apps Control described above. Also, it includes Sensitive Data Control and Insider Threats Control. These two additional features of Spinbackup DLP (Data Leak Prevention) and G Suite security features help to round out the total defense of the G Suite environment.
Spinbackup Sensitive Data Protection
With the Sensitive Data Protection features, Spinbackup allows organizations to prevent the leakage of any data that is deemed to be sensitive. This includes Credit Card Numbers and other patterns that organizations can create to match custom definitions. It also includes any “personally identifiable information” or PII. This is especially important with GDPR compliance.
Organizations must keep a tight handle on any customer information that is being processes as well as who has access to this data and making sure that data does not leave the organization inappropriately. The Sensitive Data Control allows organizations to control:
-
-
- Which information is shared in the G Suite organization?
- Who owns the data that is shared?
- What outside resources have access to the data
- Exactly which information is shared
- Credit Card Numbers, PII, and other information that should be filtered
-
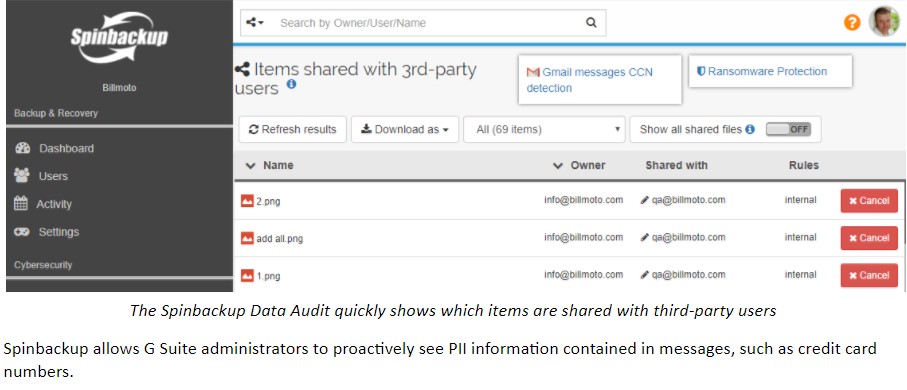
Spinbackup allows G Suite administrators to proactively see PII information contained in messages, such as credit card numbers.
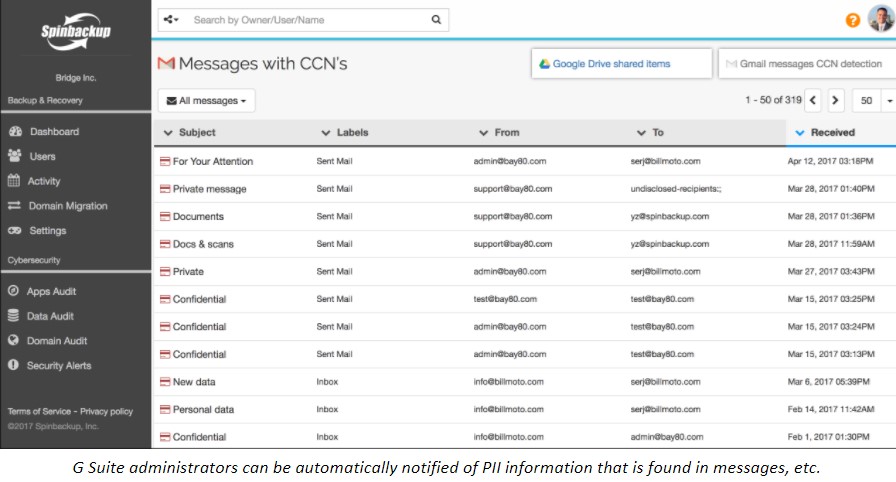
Spinbackup Insider Threats Audit for G Suite
Determining insider threats to company security is extremely important. This threat vector is almost always overlooked with organizations concentrating on threats from the outside. With the Insider Threats Control, Spinbackup provides organizations with the tools they need to gain visibility to possible intentional unscrupulous employee activity, or accidental employee actions that may present a data leak or security threat.
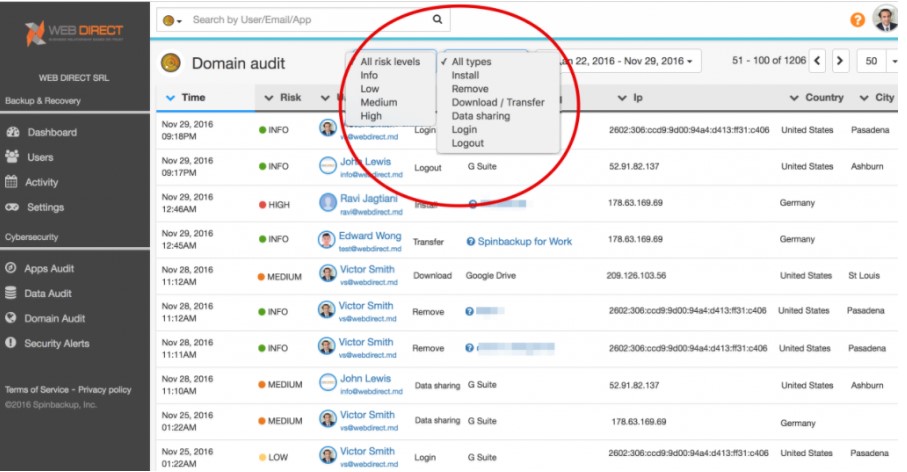
Under the Domain Audit Dashboard, G Suite administrators can see various risk levels and employee actions that can result in data leak or other cybersecurity compromise. These include:
-
- Installing/Removing third-party apps
- Downloading/Transferring data
- Sharing Data
- Credit Card events
- Sending data to the Trash Bin
- Deleting Data completely
- Abnormal logins
- Ransomware Protection events
Spinbackup G Suite Ransomware Protection
Many of the recent events making headlines with large corporations as of late, have been related to ransomware. Ransomware can totally and completely bring normal business operations to a halt, effectively rendering systems inoperable. Having control over ransomware infection, especially in the public cloud is no easy feat with native public cloud tools.
Spinbackup provides organizations with the tools needed to combat the plague of ransomware so they do not find themselves in the headlines for disrupted business-critical systems and/or leaked customer data. Spinbackup’s G Suite Ransomware Protection features:
-
- Machine Learning enabled ransomware detection and remediation
- Automatic blocking of ransomware processes and the applications responsible
- Automated file restoration of any data encrypted by ransomware processes
- Automated G Suite administrator notification of ransomware activity
Again, Spinbackup API-based CASB allows organizations to have machine learning algorithms working at protecting their environments around the clock as well as automated, proactive responses that simply are not possible with manual human interaction.
Takeaways
The recent Facebook data leak scandal has been eye-opening for many. It should be a wakeup call for businesses today to understand the major responsibility they have in protecting customer data as well as ensuring data privacy. The stakes are high as seen with the market cap losses suffered by Facebook with the recent data leak scandal. Organizations can no longer view data privacy and data leak prevention as recommended – it is required.
The Facebook scandal also underscores just how important it is to control third-party application integrations with public cloud environments. All third-party apps need to be viewed with scrutiny, regardless of the publisher. By using the powerful machine learning algorithms provided by Spinbackup API-based CASB, organizations can effectively analyze all activity inside their Google G Suite environments and determine any anomalies in the way data is accessed by either third-party applications or end users.
Was this helpful?
- Data Leak and Data Loss Meltdown 2018
- Facebook Scandal – Leaked Member Data – How it Happened
- Facebook Data Leak Scandal: 4 Lessons Learned
- Data Loss, Data Leak, and Cybersecurity for Public Cloud
- Spinbackup Risky Third-Party Apps Control
- Spinbackup G Suite DLP (Data Leak Prevention)
- Spinbackup Sensitive Data Protection
- Spinbackup Insider Threats Audit for G Suite
- Spinbackup G Suite Ransomware Protection
- Takeaways
How Can You Maximize SaaS Security Benefits?
Let's get started with a live demo
Latest blog posts
Importance of Backing Up Google Workspace Data Daily
January 23, 2024Many organizations today are heavily relying on cloud Software-as-a-Service offerings for business productivity, communication, and... Read more
Google Workspace in 2024: Key Updates and Features
December 14, 2023Google Workspace is constantly improving to bring new productivity features for businesses. In this article,... Read more
How to Implement Data Leak Prevention in Google Workspace
October 27, 2023Data leaks in Google Workspace can have severe legal, financial, and reputational implications for the... Read more


