Cybersecurity Threats: Types, Detection & Prevention

Cyber-attacks continue to pose significant threats to businesses of all sizes. Data breaches have surged to alarming rates, with a staggering 46 data records being stolen every second. As cyber security threat detection is essential for the digital health of any organization, you need to identify the risk sources: external or internal.
Most companies focus on reducing the threats from outside the business. However, threats originating from within the organization may be a bigger threat than most people realize. In fact, one of the main causes of data breaches is an unintentional leak due to a careless employee.
What are the cybersecurity threats?
A cybersecurity threat is an event or software that can exploit a cyber vulnerability in the information system and bring damage to an organization. It bears multiple risks and may or may not result in a cyber incident.
Types of cyber threats
Cybersecurity threats can be categorized in various ways, including by their source:
- Physical damage. This includes threats such as natural disasters that can destroy a company’s hardware infrastructure, leading to data loss and disruption of operations.
- Social engineering. This involves tactics where cybercriminals manipulate individuals, typically employees, into divulging sensitive information such as Personally Identifiable Information (PII) or login credentials. For instance, a cybercriminal might deceive an employee into providing the personal information of a CEO through phishing emails or pretexting schemes. Cyberattack. For example, a successful hacker attack on a network results in the leak of sensitive information.
- Malware. Malicious software designed to infiltrate and compromise computer systems.
- Software error. Bugs or vulnerabilities within applications can lead to data corruption or system instability. For example, a bug in an application corrupts the data and the team has to begin the project from scratch.
- Hardware malfunction. Failures in physical equipment such as internet routers can disrupt operations. For instance, if an internet router malfunctions it causes downtime in the work of an entire office.
By objective:
- Intentional cyber security threats occur as a result of the ill will of a cybercriminal.
- Malware, social engineering, and cyber attacks.
- Unintentional cyber threats are caused by a mistake or occur by chance.
- Physical damage, software errors, and hardware malfunction.
The outcomes of both intentional and unintentional threats can be equally damaging for an organization. That’s why a company’s cybersecurity experts should treat them in the same manner and never overlook the second type.
By target:
- Individuals. For example, a phishing scam email aims to obtain the credit card data of a person to steal money.
- Organization. For example, a DDoS attack on a server intrudes in an esports match.
- State. For example, cyber espionage undermines the economy of a country.
By the type of vulnerability they exploit:
- Procedural threat relates to how business processes using information systems are organized in a company.
- The architectural threat takes advantage of the weakness in components of the information system.
- Human threat exploits the errors that employees make.
Top cyber threats
- Social engineering attacks
- Ransomware
- Shadow IT
- Fileless attacks
- Insider threats: human errors and man-in-the-middle attacks
- Exploit of the internet of things
Cybersecurity threats and preventive measures
On the national level, threats can be controlled by:
- Adopting respective laws;
- Monitoring cybercrime;
- Raising awareness on cyber threats;
- Arresting cybercriminals.
The protection measures for a company include:
- Building strong cybersecurity;
- Educating their staff;
- Monitoring cyber threats;
- Looking for vulnerabilities in their information systems to remove them;
- Reporting cyber incidents to the state in case of occurrence.
Cyber threats vs. Vulnerabilities and Risks
Vulnerabilities, threats, and risks are sometimes used interchangeably. However, cybersecurity experts emphasize that they’re different terms.
Check out the table that will explain the difference between them:
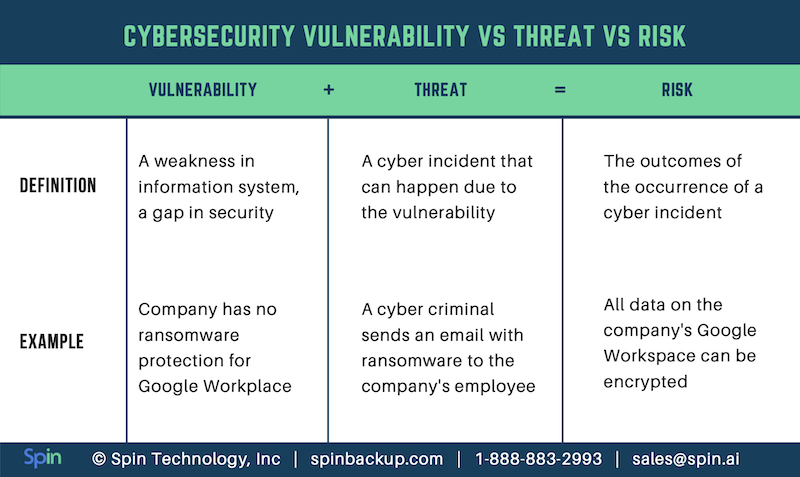
A cyber incident and related risks will only occur in case the vulnerability and the threat that can exploit it concur in time and space.
Outsider Threats
Threats from outside the organization may include hackers, cybercriminals, competitors, or any malicious person who is not affiliated with the company.
These external attacks are often financially motivated such as ransomware attacks, in which malware is installed on devices containing company data. This data is then encrypted and can not be accessed until a substantial amount of money has been paid to the attacker.
However, the aim of every cybercriminal is not necessarily to make money. Data can also be very valuable for various reasons and it is often the case that an attack occurs in order to access sensitive data. In these situations, the company may not even realize the data breach has occurred until well after the event.
Methods of Cyber Attacks
There are various methods an external attacker can use to gain access to internal systems and data:
- Social engineering and phishing attacks in which passwords or other sensitive and personal information can be guessed or obtained via employees for example, by an outsider posing as someone else inside the company.
- Hacking, where malicious individuals gain access via security loopholes in code and authentication systems.
- Ransomware and malware, a computer program hosting malicious code that may allow backdoor access for a hacker, or delete or change existing data. These programs are usually installed by mistake as they are often posing as genuine files or software.
- Denial of Service attacks (DoS) are a type of attack that makes websites and other online services inaccessible to users by flooding the server with requests.
- Physical theft, usually of mobile devices may allow unauthorized users access to sensitive data.
- Malicious USB drops are another way that hackers can get malware onto a system by leaving USB pen drives loaded with malicious software in a place they know they will be picked up and accessed out of curiosity.
- 3rd-party apps are a new method that hackers are using to infect systems with malware such as Gooligan.
Malicious attacks from outside the organization are more common than internal attacks. To illustrate this, in a survey into Cybercrime issued by the Ponemon Institute, every single company surveyed had experienced a virus, worm, or trojan attack at some point, and 97% had been affected by malware.
Insider Threats
Insider threats include attacks by current or past employees, contractors who have been given access to internal systems, and other business partners who may be privy to restricted data. A data breach may also occur not as the result of a malicious attack, but because an employee has inadvertently given an outsider access to his or her account through carelessness or ignorance about proper security procedures.
The motivations behind insider attacks are often the same as with external attacks – financial motives may be behind the attack, or it may be the case of a disgruntled employee trying to get revenge on his or her employer by leaking sensitive data. Employees may also be influenced by outsiders such as competitors, using them to gain access to company systems.
It’s also worth noting that the majority of insider threats are not malicious attacks, but rather caused by employees’ curiosity or carelessness with standard security procedures. Shadow IT, in which employees install software that has not been vetted by the IT department and so may be a security risk, is also a huge problem for many modern businesses.
Shadow IT continues to rise, fueled by the proliferation of mobile devices and the adoption of Bring Your Own Device (BYOD) policies within companies.Third-party apps are often installed by employees to help increase their productivity but these apps often connect with SaaS applications and can introduce new security risks. For this reason it’s important that third-party apps are audited on an ongoing basis in order to be aware of any potential security risks.
- Many companies possess a significant amount of sensitive data, the exposure of which could potentially result in severe damage to the company’s reputation. This sensitive data may include: Trade secrets and intellectual property
- Regulated data
- Sensitive data
- Information about products and internal research
- Financial and personal staff information
- Source code
- Business plans and other sensitive corporate information.
Methods of Attack
It is generally easier for internal employees to gain access to this kind of data and so internal attacks can be difficult to protect against. The best method of defense is to invest in an internal cyber security threat monitoring and detection system that will monitor the online behavior of employees and report anything suspicious before a data breach occurs.
Common types of internal or potential attacks include:
- Social engineering, in which an employee is manipulated into giving up passwords or other confidential information.
- Data sharing with 3rd-party people or public sharing.
- Unauthorized downloading of data onto a personal USB drive or another storage medium.
- Unauthorized data transfer to personal cloud storage accounts.
- Abuse of employee privileges to access confidential corporate data for personal gain.
- Physical theft of company equipment such as computers or mobile devices.
Internal attacks, although less prevalent than external ones, still pose a significant threat. Despite their lower frequency, internal attacks can incur substantially higher costs compared to external ones. Attacks originating from malicious insiders resulted in an average annual business cost of $18.33 million.
Learn other cybersecurity terms!
Which is the Biggest Threat?
It’s clear that any business fighting cybercrime must put equal measures against both internal and external attacks into place, as both pose a serious threat to business data and finances.
Most cloud data breaches actually involve a combination of both internal and outsider threats, so it is vital to protect data from any possible type of attack.
Sensitive data can be secured via secure encryption, restriction of access both physically and by user account. However, securing data can only go so far towards protecting it. Staff security training is also essential to ensure data is not put at risk unnecessarily. Monitoring systems for irregular activity from both within the company and from external access by individuals, and via third-party apps, may be the best way to block attacks before they cause serious damage.
Explore Spin.AI’s best practices for Cyber Risk Management and keep your valuable data protected!
Was this helpful?
How Can You Maximize SaaS Security Benefits?
Let's get started with a live demo
Latest blog posts
Reducing Browser Extension Risk with Spin.AI Risk Assessment + Perc...
April 24, 2024Spin.AI is collaborating with Perception Point: integrating the Spin.AI Browser Extension Risk Assessment within the... Read more
How to Restore A Backup From Google Drive: A Step-by-Step Guide
April 10, 2024Backing up your Google Drive is like making a safety net for the digital part... Read more
Protecting Partner Margins: An Inside Look at the New Spin.AI Partn...
April 2, 2024Google recently announced a 40% reduction in the partner margin for Google Workspace renewals –... Read more


