SaaS Security for Mission-Critical SaaS Apps
Enhance cyber resilience, security operations, and cost efficiency with an all-in-one SaaS security platform that protects your SaaS data from loss, ransomware, risky apps, misconfigurations, and non-compliance
Trusted by over 1,500 organizations across 100+ countries
All-in-one SaaS Security Platform
SpinOne provides SaaS security posture management, SaaS DLP, SaaS ransomware protection and SaaS backup to protect data for Google Workspace, Microsoft 365, Salesforce, and Slack.
Improve your Security Posture Management and reduce the risk of Shadow IT
Get visibility into and control over unsanctioned apps and browser extensions that have access to your mission-critical SaaS data with SpinOne SSPM.

Find out today how many unsanctioned Apps and Browser Extensions have access to your Google Workspace or Microsoft 365 environment with our
Automated AI-driven Risk Assessment.
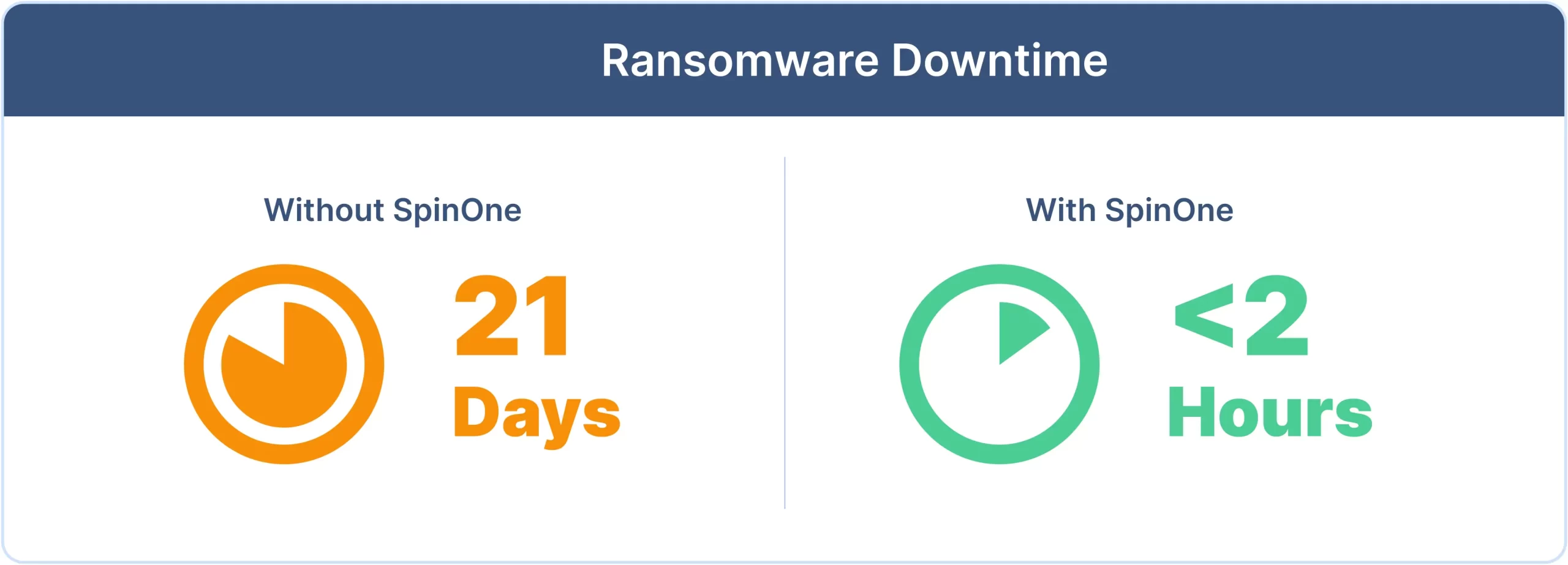
Reduce downtime and recovery costs from ransomware attacks
Slash downtime from months to minutes or hours and reduce recovery costs by up to 90% with SpinOne Ransomware Detection and Response.
Stress test your Google Workspace or Microsoft 365 environment with our Risk-free Ransomware Simulator.
Start the Ransomware Simulator test
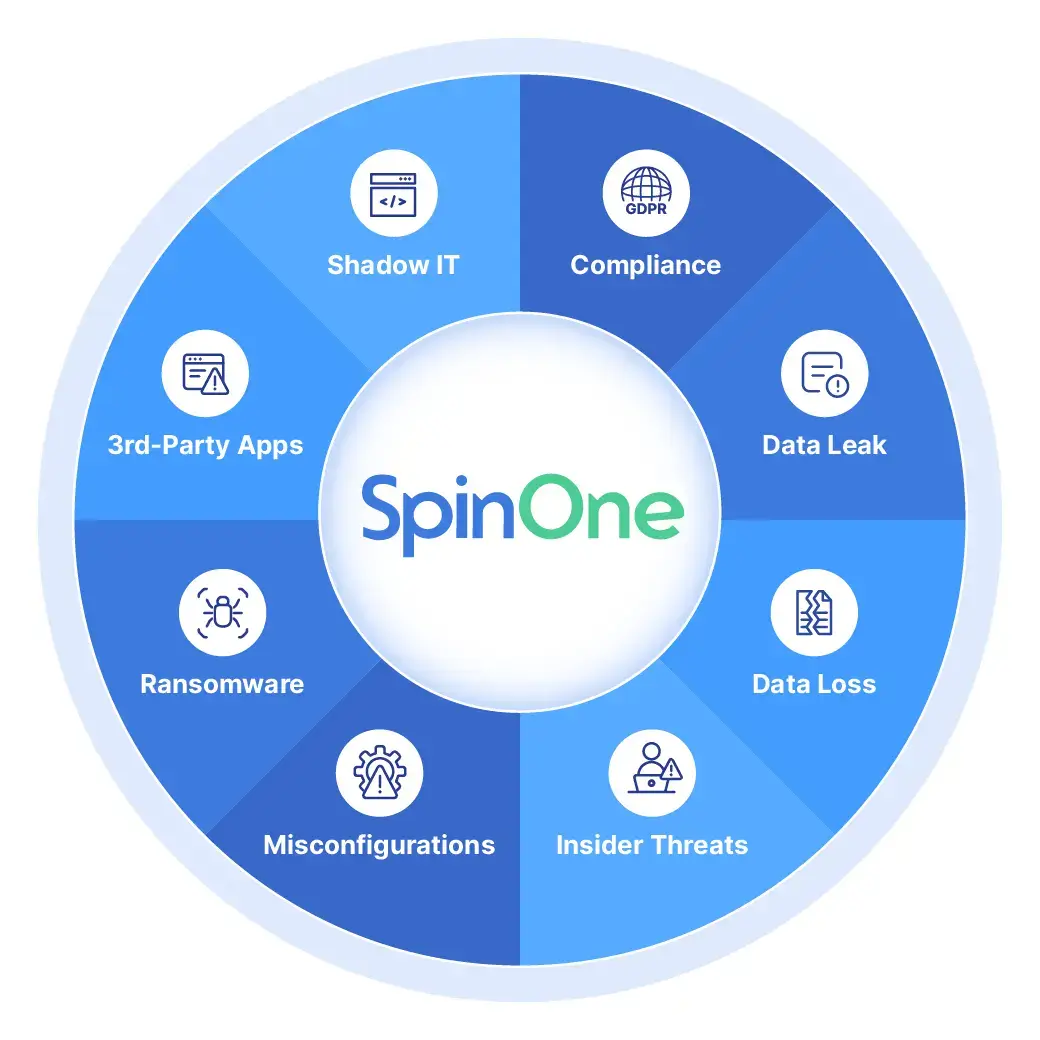
Reduce security incidents from data leak or loss, and improve compliance
Reduce your number of security incidents, and recover lost SaaS data in minutes, not months.

Get full visibility and control over sensitive SaaS data being shared
outside/inside of your organization, abnormal data transfer, downloads and deletion.
Why Spin.AI?
400+
Partners Worldwide
1,500+
Customers Worldwide
300K+
Apps Discovered by our AI Algorithms
1,000,000+
SaaS Business Users
Spin.AI Partner Program
Manage and expand your business, and advance the SaaS cybersecurity needs of your customers, with an all-in-one solution for protecting SaaS data in mission critical SaaS applications. Join the 400+ partners in our program.
Enterprise security for SaaS data






Company Achievements
Business Intelligence Group Award for Business 2023
- Dmitry Dontov Named Small Business Executive of the Year
- Next Gen SaaS Security
- Hot Company in App Sec
- Hot Company in DLP
- Cutting Edge Ransomware Protection

2023 Cyber Top Innovation Award
- Presented by Enterprise Security Tech

Top 10 SaaS Solution Providers
- According to GRC Outlook Magazine

Top Cloud Security Solutions Provider
- According to Enterprise Security Magazine

2021 Cloud Computing Security Excellence Award
- Presented by Cloud Computing Magazine

2023-24 DCIG Top 5
- Top SaaS Backup Solution for Microsoft 365







Jake Kilian
Technology Support ManagerTed Do
IT ManagerLouis Burdulis
Executive Vice PresidentVal Pashchenko
Information Technology ManagerGeorg Israel
General ManagerMichael Svedeman
Senior Manager, Project DevelopmentGeet Jacobs
Director, Digital OpsRoland Chan
Chief Information Security OfficerJoshua Goss
Senior Director of ITStephan Matter
Technical Operations Manager