6 Google Workspace Admin Roles and Responsibilities

As a Google Workspace Admin, you have multiple important responsibilities, all aimed at one key goal: protecting your company’s data. keeping your company’s data secure.
As a data protection company, we strive to make the work routines of business owners and IT administrators seamless with our products and expertise. This article will help you grasp the main Google Workspace admin roles and responsibilities and provide you with some tips to make these tasks easier.
Administrative Roles and Privileges in Google Workspace
In the Google Workspace environment, administrators, as well as users, can have different levels of permissions and authority. The level of this authority determines what access and management rights you have in this ecosystem. The more responsibility you have as an administrator, the more rights you will require.
There are two types of Google Apps admin roles:
1. Default (pre-built) roles. These are the template roles that have prebuilt sets of functions and permissions. There are 10 pre-built administrative roles you can choose from. The most commonly used are:
- Super Admin. This role has the “ultimate” access and managing rights in your organization’s Google Workspace account and can manage everything. We don’t recommend assigning this role to just one person.
It’s better to choose one board member and one staff member to share this responsibility. This role should be protected by all available security measures. - User Management Admin. This role involves managing every aspect of ‘users’ (but not ‘admins’) accounts, this includes tasks such as changing usernames or passwords, adjusting security settings, and managing account deletions when necessary.
2. Custom roles. If you aren’t satisfied with the default roles, you can create the roles that will meet your needs. You can do that by choosing the roles and privileges from the same default settings and sorting them as you want to.
This is useful when you have a task that requires specific permissions. You can assign a non-administrative user without granting them the full set of privileges.
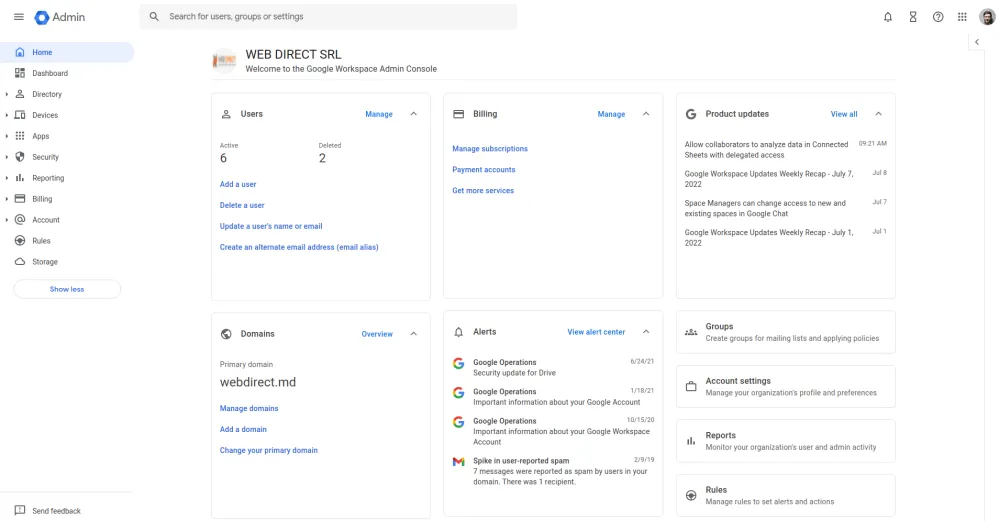
6 Key Google Workspace Admin Tasks and Responsibilities
You, as an admin, handle a significant amount of vital information daily. Correct data management will help you save your time and get a complete understanding of your company’s data. Use the Google Admin Dashboard (Admin Console) to monitor every aspect of the Google Workspace domain. This includes usage, user status, storage, security, and file sharing.
The Admin Console for Google Workspace is an extremely useful tool for corporate data management. The Google Admin Console allows accessing and managing information about various aspects of Google Workspace.. The features Admin Console gives access to are Apps, Billing, Users, Security, and more.
A must-have for a perfect Google Workspace admin is understanding interactions between users/apps and the Business account. The admin console will help you to get regular reports on these interactions.
Using the information provided in the Admin Console, you can monitor every aspect of the Google Workspace domain. The console’s report offers metrics such as:
- Usage
- User status
- Storage
- Security
- File sharing
For example, if you want to monitor user behavior, you should click on Users in the Google Workspace admin panel. Moreover, Google has important security features for admins. To learn more on how to use them, check out this article. Now, let’s see what are the main tasks a Google Workspace admin should do to secure company data.
1. Backup Google Workspace data
Over 50% of data loss issues are due to end-user mistakes. So, if someone accidentally or maliciously wipes out an important shared folder a whole department relies on, Google Workspace won’t be able to help you restore it. Similarly, if ransomware corrupts all your company’s files, Google Workspace won’t be able to assist in restoring them.
Doesn’t Google backup my data if I use their apps, you may ask?
The answer is, no, it doesn’t. They provide you with the infrastructure to manage your data in their Starter and Standard subscriptions.
Certainly!
For $18/month per user with the Plus plan, you can access certain data via the Google Admin Console through Google Vault. This access is useful for potential legal proceedings.
(Here’s more on how to save up to 64% on Google Workspace licenses→)
Backup is the only way to restore your lost or modified data, particularly when dealing with high volumes of operational data.
2. Secure user authentication
Preventing unauthorized access to the system is among the key admin responsibilities. Insufficient security measures may lead to a data breach, where a company’s data is compromised or or stolen by hackers leading to potential significant reputational and financial damage..
Enabling Google 2-Step Verification is a good security practice. With 2-step verification, an account is protected using both password and a mobile phone, providing an extra layer of security.
Why is the 2-Step Verification effective? It’s quite simple. A password is required to log in. When you activate Google 2-Step Verification, you must also enter the security code sent to your phone via SMS.So even if your password is compromised, your account is still under your control.
To ensure robust access control, administrators should enforce 2-step verification for all employees. Accessing the account through a 2-step verification assures that there will be no unauthorized access to data and information.
Moreover, reinforced access increases the level of authentication. You can verify security processes through the Users link in the admin panel. Reports from the admin console display specific users who have not used a 2-step verification. Through this report, you can ensure that everybody in your organization is going through a 2-step verification process when accessing their corporate accounts.
3. Check Third-Party Apps
Additionally, it’s essential to scrutinize third-party apps accessing corporate data as they may introduce vulnerabilitiesFor example, your sensitive data might be stolen or altered.
The sad truth is that many apps have embedded Trojan codes within. Giving a malicious app access to your data may result in a major data breach.
A good admin understands these possible risks and takes measures.
A Google Workspace admin should regularly audit all third-party apps installed by users and allow or deny their access. The audit ensures transparency of the apps and allows you to mitigate or avoid risks permanently. You can perform the audit through the Security, Apps , and Device management links in the admin console. However, a manual audit is time-consuming.
SpinOne 3rd-party apps audit offers full visibility and risk assessment.. This security feature provides an administrator with a set of tools to monitor and detect risky applications. Additionally, it helps prevent corporate data from leaks caused by suspicious or dangerous software.
5. Create an Incident Response Plan
There are many potential Google Workspace security incidents. Data leakages, phishing attacks, ransomware infections, to name a few. In fact, they can happen anytime. Usually, the damage becomes more serious with time.
That’s why it is a good practice to create an Incident Response Plan. This plan will allow you to act quickly in time of a security incident to minimize the damage and prevent the whole system from collapsing.
A response plan consists of three major elements: detection, prevention, and control.
Prevention is a set of actions aimed at making the chance of a cyber attack as low as possible. Perhaps, the most important prevention action is ensuring a 2-Step Verification is used consistently.
Detection is the foremost defense. You must be able to distinguish unwanted incidents such as viruses, hacks, and other malicious attacks. Your Google Workspace admin’s response plan should include the ability to detect almost all suspicious activities before they take place.
The significant suspicious activity is access to unauthorized data, instigated by third-party apps, malicious codes, and even hackers – including employees.
You need to use control measures when access to unauthorized data occurs. For a compromised account, you can use the following measures of the response plan:
- Changing the access password immediately
- Neutralizing the attack or mitigating cyber risks
- Updating the system.
The main goal of these actions is to fix the consequences of an incident. Sometimes, the control operations include a whole set of actions to restore the system to its initial capacity. The control measures can help even if an admin account itself was targeted.
6. Instill Proper Process for Onboarding and Offboarding Employees
. The more new employees gain access to the corporate network, the more potentially vulnerable endpoints appear. An admin has to prevent and avoid a security breach both from within and from outgoing entities.
The solution you need is the implementation of an insider security policy. The policy will ensure that the system activities of your employees can be monitored at all times. Moreover, it will raise the cybersecurity awareness of the staff. More security awareness = fewer potential threats.
A Google Workspace admin should also make sure that employees follow the company’s Bring Your Own Device (BYOD) policy put in place. Many security attacks arise from breaches, which take place on employees’ external devices such as USBs, hard drives, or even smartphones and laptops. In fact, fresh employees are often unaware that a USB flash drive they bring in may be infected with malware.
If employees leave the company, they should be denied further permission to access the company’s data and information. An admin should provide a secure employee exit.
Here you can find a step-by-step guide on secure exit with Google Workspace.
In conclusion, mastering these Google Workspace administrator fundamentals is essential for safeguarding organizational data and preventing data breaches. Implementation of these best practices ensures the success and security of your organization’s data assets.
Was this helpful?
How Can You Maximize SaaS Security Benefits?
Let's get started with a live demo
Latest blog posts
Reducing Browser Extension Risk with Spin.AI Risk Assessment + Perc...
April 24, 2024Spin.AI is collaborating with Perception Point: integrating the Spin.AI Browser Extension Risk Assessment within the... Read more
How to Restore A Backup From Google Drive: A Step-by-Step Guide
April 10, 2024Backing up your Google Drive is like making a safety net for the digital part... Read more
Protecting Partner Margins: An Inside Look at the New Spin.AI Partn...
April 2, 2024Google recently announced a 40% reduction in the partner margin for Google Workspace renewals –... Read more


