Google Workspace Enterprise Security Guide

In this guide, we will introduce the best practices and tools to enable your Google Workspace Enterprise Security. Learn how to secure the organization against data leaks, data loss, unauthorized access, and potential insider threats.
Google Workspace Enterprise Security with API-based CASB
Organizations today consider CASB implementations to be a crucial aspect of their security posture with their public cloud infrastructure. They rely on API-based CASB to perform many of the following important functions:
- Many company employees may have personal public cloud accounts that are accessible from company networks. CASBs can help prevent any data sharing between approved company public cloud resources and personal public cloud resources.
- Prevent upload and download functions.
- Monitor privileged account usage and prevent any unauthorized access using those accounts.
- Set a policy for end-users accessing public cloud resources. This policy should be based on the device or user account being used.
- Enforcement of encryption policy – both in-flight and at-rest data encryption.
- An application audit will be performed to assess approved applications. The audit will assess potentially unwanted applications. These applications may have access to or be linked to company-approved public cloud resources.
- Confidential information detection and scrubbing – CASBs can detect and remediate sensitive or confidential information. This can be credit card numbers or social security numbers – being shared to unauthorized people.
- Malware/Ransomware detection and protection against threats – Generic malware and especially Ransomware are huge concerns for organizations today and these concerns now extend to cloud resources such as cloud storage. CASB implementations must be able to protect against these threats.
- Proactive security alerting that actively alerts when certain events are triggered, including sensitive data detection.
The most powerful and modern approach to instantiating a CASB is to use an API-based CASB platform.
A great example of seamless API-based CASB integration with the public cloud is SpinOne for Google Workspace (G Suite) . SpinOne API integration offers powerful features to monitor, prevents data leakage, and protects cloud resources from malware/ransomware threats.
The features are integrated tightly, no matter what device or network is used to access the data. This means there is no need for end-users to configure anything. Additionally, the security and policies cannot be bypassed.
SpinOne can be configured for Google Workspace. This sets the security policies and templates. The changes are implemented in the cloud through API integration. They are not configured based on a proxy setting.
The dashboard integration with Google Workspace provides a single pane of glass and very much feels like a native part of the Google Workspace (G Suite) public cloud.
Try SpinOne for free
Ensure Data Loss Prevention (DLP) for Google Workspace
Let’s take a look at the objectives of each of these types of data loss protection, and how each can play a powerful role in protecting organizational data from unexpected loss.
Effective Cloud to Cloud Backups
One of the most effective means of cybersecurity that often is overlooked is backups. Backups in themselves are a security mechanism. This can protect against accidental damage to data. In fact, over 50% of data loss issues are the result of end-user mistakes.
Backups also protect against intentional damage to data caused by a disgruntled employee or an attacker. Some organizations first entering public cloud environments often mistakenly assume that public cloud vendors have robust backups of your data built into their storage plans.
Automated Daily Backups
Organizations looking to move to the Google Cloud Platform need to utilize a solution for backing their data securely and automatically. Organizations can have a secure and customizable approach to backing up data in the public cloud by implementing a Google Workspace backup solution that allows fine-grained control over backed-up files. Encrypting backed-up data further enhances the security of the backup solution.
Back up Google Workspace Data During Migration
During migration to Google Workspace public cloud services, organizations are at risk of data loss if backups are not happening immediately. As soon as business-critical data lands in the Google Workspace public cloud environment, it needs to be protected.
Make sure to have a solution in place before moving business-critical data. Have a solution designed to begin backing up data once the Google Workspace data migration begins. This way, data is protected from both sides – both on-premise and in the Google Workspace public cloud.
Google Workspace Data Deletion Control
Organizations want to choose a solution to be able to monitor the deletion of files/folders across their Google Workspace environment. Often, disasters with data loss can happen because administrators are unaware of the damage that has already taken place, as they have no visibility to data that has been deleted. Deleted data can then rotate off the retention policy of backups and become unrecoverable.
SpinOne allows organizations to move to Google enterprise cloud environments with confidence. Data loss in the public cloud should be one of the major security concerns for Google Workspace (G Suite) administrators. Losing business-critical data can lead to a disaster for brand reputation and customer confidence.
Having a true Data Loss Prevention (DLP) solution such as SpinOne provides cloud-to-cloud backup. It is also an effective protection and remediation solution in the event of ransomware infections that affect data stored in the Google Workspace public cloud. Equally alarming security concern for Google Workspace administrators involves data leaks.
Try SpinOne for free
Risky Third-Party Apps Control
There is a wide range of third-party applications that can integrate nicely with a Google Workspace organization and extend functionality and features. Despite the efforts of Google and other cloud services vendors in screening applications to make sure they are safe, risky applications exist in the marketplace. Also alarming is the ability of risky third-party applications to be easily integrated by end-users into an unmonitored or uncontrolled (third-party apps) Google Workspace environment.
Many organizations mistakenly think that providing secure, reliable backups of data in the public cloud is the public cloud vendor’s responsibility. This same mistake can also be made with securing data in the public cloud. Organizations might assume that public cloud vendors might hold some responsibility for ensuring public cloud data is secure.
When considering third-party app integration, vendors of these apps may be held responsible for the security of the organization’s data. They have been entrusted with this data, so it is assumed that they will take appropriate measures to protect it.
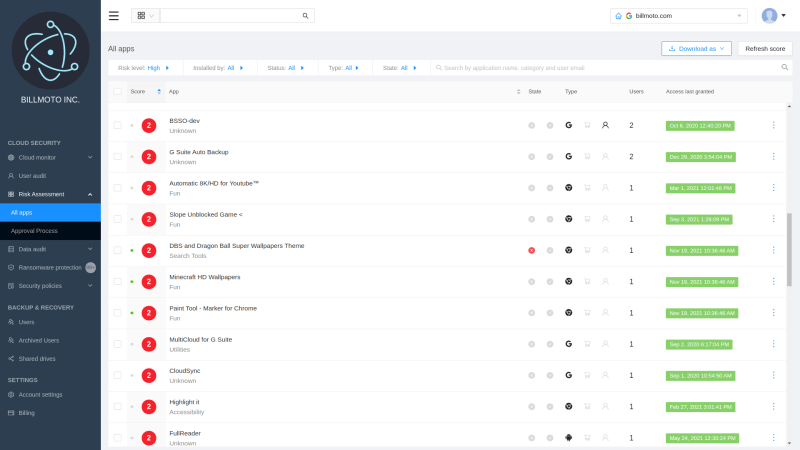
Much of the power of the SpinOne Risky Third-party Apps Control comes from the built-in Incident Response Plan. The incident response plan includes manual and automated actions that prevent data loss and data leakage. The Incident Response Plan allows Google Workspace administrators to be proactive by allowing them to:
- Quickly revoke access to third-party apps that are deemed risky and have corporate data access
- Use powerful machine learning to revoke access based on “abnormal behavior”
- Proactively send alerts to Google Workspace administrators notifying them of the event
- Automatically blocking the download of data that is abnormal
- Automatically blocking abnormal cloud data migration.
Sensitive Data Control
On July 29, 2017, arguably the most shocking breach of PII (personally identifiable information) was discovered by Equifax. Over 143 million people and their most sensitive data were exposed by attackers. This was the holy grail of sensitive data leakage as it contained all the personal information for each individual in one place – name, age, address, social security number, etc.
It underscores in a large way how much we value protecting sensitive data especially when it relates to our personal information. Of tremendous importance for Google Workspace administrators thinking about securing Google Workspace (G Suite) environments is moderating and controlling sensitive data in the Google Workspace environment to prevent data leaks.
Google Workspace security requires a multifaceted approach that includes important measures such as cloud backups, ransomware protection, and risky third-party apps control.
Sensitive data can include a wide range of information that is not to be disclosed to any unauthorized recipient. In general, it includes the following types of personally identifiable information (PII) as well as other information which may include the following:
- Social security numbers or SSNs, phone numbers, addresses, etc.
- HIPAA (Health Insurance Portability and Accountability Act) information such as patient diagnoses, treatments, and other protected health information
- Financial or payment information – This can include the common credit/debit card numbers, bank accounts, or other financial or payment information
- Miscellaneous sensitive information – This can be any information that is deemed sensitive by an organization such as financial records, source code, or company secrets.
Google DLP or Data Loss Prevention is an automated mechanism used to monitor both Google Gmail and Google Drive for certain content configured by a Google Workspace administrator that protects data meeting those configured parameters from data leak.
SpinOne bolsters the native DLP functions of Google Workspace services and also distinguishes itself from Google DLP in key areas:
- Google DLP only protects while SpinOne provides additional powerful monitoring that gives full visibility to Google Workspace administrators
- It provides proactive alerting that gives Google Workspace administrators real-time visibility to defined events related to data loss prevention and data leak
- It is an autonomous system separate from Google services that help to bolster the native Google DLP functions.
By utilizing both the power of built-in Google DLP functions along with the extended functionality provided by SpinOne data loss protection and data leak protection, organizations are equipped to meet the overwhelming security challenge presented by Google Workspace (G Suite) environments and sensitive data control. With SpinOne Sensitive Data Control, data and email messages containing sensitive data can be flagged. They are clearly noted in the Dashboard under the Data Audit section. Alerts are also sent out to Google Workspace administrators.
Try SpinOne for free
SpinOne DLP: Insider Threats Control Overview
Best practices for Google Workspace (G Suite) administrators providing recommended security to the Google Workspace public cloud environment includes:
- Appropriate Security Policies and training in place
- Assign users with the least privileged access
- Have strict password and account management policies and practices
- Have appropriate logging, monitoring, and auditing of employee actions
- Monitoring suspicious employee behavior
- Providing backups of business-critical Google Workspace (G Suite) data
- Implementing threat controls to remediate threats
SpinOne provides the powerful DLP tools that allow Google Workspace administrators to have visibility to insider threats coming from end-user activity within the Google Workspace environment. Part of the “single pane of glass” view that SpinOne gives to Google Workspace administrators includes cybersecurity tools including the Domain Audit dashboard. Using this view, Google Workspace administrators can see a global overview of all user actions in real-time as well as an automated risk assessment evaluated by SpinOne.
DLP tools are also effective in preventing data breaches by detecting and blocking attempts to exfiltrate sensitive data.
Benefits of using SpinOne DLP for Insider Threats Control
The powerful Insider Threats Audit provided by SpinOne integrates seamlessly with the entire suite of data loss protection and data leak prevention provided. In fact, it is but one of the many tools provided to organizations looking to protect business-critical data with cloud to cloud backups, ransomware protection, risky third-party apps control, and sensitive data control.
SpinOne offers all the mentioned tools in one product, providing Google Workspace administrators with visibility to insider threats and the ability to moderate and remediate risky user activity. This makes SpinOne unique in its ability to provide a comprehensive solution for Google Workspace (G Suite) security.
Try SpinOne for free
Google Workspace Ransomware Protection
With the dangers mentioned above, businesses must be proactive about protecting their data in the public cloud from ransomware infections. SpinOne provides a powerful solution to both detect and counteract the effects of ransomware attempting to encrypt data stored in the Google Workspace environment. It provides the following mechanisms for ransomware protection:
- Ransomware Detection within Google Workspace (G Suite) Domain
- Automated Blocking of ransomware encryption processes
- Identification and Automated Restore of Encrypted Files
- Effective Versioning System
- Google Workspace Administrator Alerts
Rather than being separate, disjointed mechanisms for providing ransomware protection, the above processes provided by SpinOne work together to fluidly provide a streamlined and orchestrated protection mechanism for Google Workspace data. These features effectively detect, stop, and remediate ransomware damage to Google Workspace data.
Try SpinOne for free
Control Your Domain with Automated Google Workspace Security Policies
SpinOne moves forward with the SaaS industry, with cybersecurity remaining as a core competency. SpinOne introduced Custom Policies as a new feature for SpinOne’s Cybersecurity functionality. This feature allows Google Workspace administrators to set the specific scope of rules, exceptions, and notification settings in order to implement greater control over their public cloud environments and to enforce and orchestrate complex security policies across SaaS applications.
Data Audit Policies allow the Google Workspace administrator to disable the sharing of specific files to certain domains and specific users. The Ransomware Protection custom policy enables automatic actions to be taken when Ransomware encryption or synchronization is detected. Sensitive Data Detection policy notifies the Google Workspace Administrator about messages containing sensitive information such as credit card numbers, while Restore Filtration prevents restoring emails that are marked with predefined subjects, sender email addresses, and domain names.
Domain Audit Policies include Abnormal Download Detection and Abnormal Login Detection. Abnormal Download Detection notifies Google Workspace administrators when a user downloads a specified number of files in bulk, or when an unauthorized application is used for cloud-to-cloud synchronization. Abnormal Login Detection notifies the Google Workspace Administrator when a brute force login attack has been detected.
Try SpinOne for free
SpinOne GDPR Compliance
Recognizing the importance of GDPR compliance, SpinOne applies best practices, international standards, and follows legal requirements when building an Information Security Management System (ISMS) within the company. We incorporate the highest standards into every phase of SpinOne’s software development process, from the outset to completion.
SpinOne employs the highest security and privacy controls, audited regularly in our SOC 2 reports. SpinOne’s cutting-edge services are driven by a collaborative effort with leading cloud service providers such as Amazon, Google, and Microsoft, whose reliability is globally recognized. SpinOne follows the recommendations provided by ISO/IEC 27002 to ensure that the data protection controls are implemented in SpinOne.
Try SpinOne for free and explore new Google Workspace security features!
Was this helpful?
- Google Workspace Enterprise Security with API-based CASB
- Ensure Data Loss Prevention (DLP) for Google Workspace
- Risky Third-Party Apps Control
- Sensitive Data Control
- SpinOne DLP: Insider Threats Control Overview
- Google Workspace Ransomware Protection
- Control Your Domain with Automated Google Workspace Security Policies
- SpinOne GDPR Compliance
How Can You Maximize SaaS Security Benefits?
Let's get started with a live demo
Latest blog posts
Reducing Browser Extension Risk with Spin.AI Risk Assessment + Perc...
April 24, 2024Spin.AI is collaborating with Perception Point: integrating the Spin.AI Browser Extension Risk Assessment within the... Read more
How to Restore A Backup From Google Drive: A Step-by-Step Guide
April 10, 2024Backing up your Google Drive is like making a safety net for the digital part... Read more
Protecting Partner Margins: An Inside Look at the New Spin.AI Partn...
April 2, 2024Google recently announced a 40% reduction in the partner margin for Google Workspace renewals –... Read more


