How to Remove Ransomware If Your Files Got Corrupted

Facing ransomware can be a nightmare scenario for anyone. Whether you’ve experienced encrypted files or a locked screen, the prospect of paying to retrieve access may seem daunting. However, despite the frustration, there are actionable steps you can take to tackle the situation head-on.
As a SaaS data protection company, we help companies restore their data corrupted by ransomware every day. However, simply restoring your data without eliminating the source leaves you vulnerable to future attacks.
That’s why we’ve put together this comprehensive guide to help you not only regain access to your files but also eliminate the malware responsible for the encryption. Within this article, you’ll discover various ransomware removal tools, along with valuable tips and tricks. By reading through to the end, you’ll not only learn how to remove the ransomware virus but also gain insights into essential preventive measures to safeguard against future attacks.
How to Remove Ransomware Depending on the Type
Before diving into the steps for ransomware removal, it’s crucial to identify the specific type of ransomware affecting your system. If you’re already aware of the ransomware variant, feel free to skip this section and proceed directly to the solutions outlined below.
It’s clear from the heading that there are two types of ransomware: blockers and cryptors. They operate differently and require different methods to get rid of them. While some of them can be removed within a few hours, others can take days; in some cases, they can’t be removed at all.
Let’s distinguish which type of ransomware you have and guide your next steps according to that.
Screen Locker Ransomware (Blockers)
Screen Locker ransomware is a malicious program that denies access to your computer, browser, or keyboard, demanding payment for restoration of access. It often masquerades as a message from law enforcement, claiming your device has been locked due to legal violations such as viewing pornography or illegally downloading content. Threats of arrest accompany demands for ransom payment within a specified timeframe. Your device remains inaccessible until the ransom is paid or the malware is removed.
Only a restricted number of functions are available – those that let you pay the ransom. Locker ransomware affects Windows users and often (but not always) leaves the underlying system unharmed. This is why this type of ransomware is considered a medium-risk type.
How to remove Screen Locker ransomware
There are a lot of ransomware removal services and tools, depending on the particular ransomware strain. We recommend using the Kaspersky free removal tool in case your antivirus program can’t detect or delete a screen locker. It suits Windows users.
All the following instructions on how to unlock your device and remove the malware you can find here.
Crypto Ransomware (Encryptors)
Crypto ransomware poses the most significant threat among ransomware types. It encrypts files across various devices such as computers, mobiles, servers, or cloud to extort money for decryption. The files are the hostages in this situation, which are under the threat of being deleted unless you pay a ransom in time.
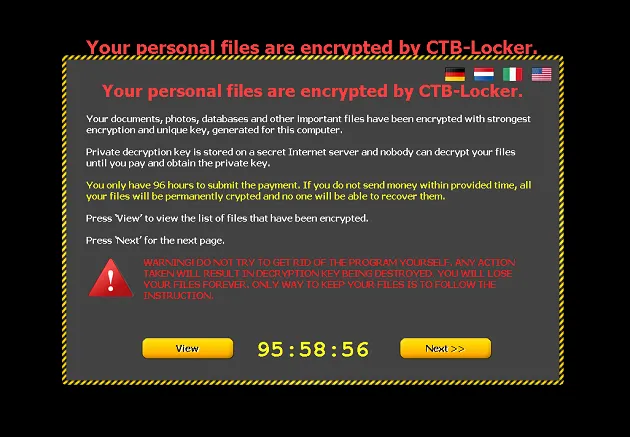
The example of Crypto Ransomware
When your device gets infected and your files are encrypted, you will see a message with the demand and instructions. The payment is always in Bitcoin or another digital cryptocurrency that is hard/impossible to track.
New ransomware forms can even seep into your backup and encrypt it, leaving you with no options rather than to pay. This is why this type of ransomware infection is considered a high-risk type.
How to remove Crypto Ransomware
The steps you need to take to remove this type of ransomware depend on whether or not you backed up files before encryption. Also, there are new types of ransomware that can seep into your backup and encrypt it, making it useless.
Ransomware removal with backup
Before you begin to remove files, you have to make sure the malware itself is neutralized. Otherwise, it will keep encrypting files.
The procedure is the same as with previous types of ransomware. You need to find a program that removes your type of ransomware, download it, scan your computer, and delete the malware.
You can try one of those free tools to scan your computer and delete malware:
When you are sure that malware is deleted, you can start the document recovery process. If you have a backup, you only need to press a few buttons; the time of the restoration usually depends on the amount of data and the internet connection.
Ransomware removal without backup
If you don’t have a backup, the process will take more time.
Step 1. Identify the type of ransomware that has encrypted your files. These tools will help with that:
- Crypto Sheriff from NoMoreRansomware. Just download the infected file and type the email, bitcoin, or website address you see in the ransomware message. They will check it for the matches in their database and come up with an answer.
- ID Ransomware. This tool works pretty much the same as the previous one. But here, if they won’t find matches in the system, they will transfer your request to their analytics.
Step 2. Remove the malware from the device, following all the steps we described earlier with Scareware and Locker ransomware.
Step 3. Find a ransomware decryptor. There are several decrypting keys available for free for certain types of ransomware. Now, when you know your type, you need to look for the key that decrypts your files. Here are the ransomware decrypt tools that have a list of keys you can choose from:
- NoMoreRansomware decryption tools. The list of ransomware types that have a key is put in alphabetical order.
- HowToRemoveGuide. Scroll a bit down to see the number of keys available with a short instruction.
You can also type the name of your ransomware + “decrypt” directly in the search.
Step 4. Decrypt your files with a key. This step is possible only in case you found your key. Don’t count on a quick result; decryption usually takes time.
If you didn’t find a key, you have two options:
- Put your data “on hold” and wait for the security experts to find a solution for your ransomware type. There is a high possibility that if you contact security specialists on the mentioned earlier sites, they will take your case to work.
- Pay the ransom. If the encrypted data is vital for you, you may consider paying the ransom. We don’t advise you to do that unless you are desperate to get your data back. Let’s consider how to do that in the most proper way.
Paying the Ransom: Tips and Tricks
Alongside other cybersecurity experts, we don’t support this idea for many reasons. And yet, sometimes you are pressed against the wall: to pay, or to lose data forever and pay X times more.
Let’s face it: most companies simply aren’t prepared to survive a ransomware attack. They have neither regular backup nor ransomware protection measures in place. This is why the ransomware attacks put around 60% of small-to-medium companies out of business within six months after the attack.
If you don’t have a backup and can’t afford to experience downtime, or the value of the encrypted files is very high, you may consider paying to get them back.
If after weighing all pros and cons you’ve decided to take a risk and pay the ransom, here are the things to keep in mind:
- You need to make sure hackers actually can decrypt your files.
It is often the case that cybercriminals claim to have the decryption key when, in reality, they don’t. In this case, you can get ripped off and still have your data inaccessible.
To check if the cybercriminals really can decrypt your files, demand them to decrypt a small portion of the data – a few documents, for example. If they refuse, this is an outright sign they are unable to decrypt your data and they’re just lying. Don’t fall for this bait.
- Don’t be afraid to negotiate the price.
Not many people are aware of that, but there is always a chance to pay less than the demanded price. To do that, you should contact criminals via the contacts they left (usually an email address) and negotiate the ransom price.
We recommend you to do that for a few reasons:
- In many cases, hackers agree to drop the price because getting at least something is better than getting nothing at all. The result – you get your data cheaper.
- There is always a chance that criminals won’t send you a key, or that key won’t work. If you negotiate a lower price, at least you will lose less money.
- Criminals tend to demand more money when they see your willingness to pay the initial price. By negotiating, you show that it won’t work with you.
Note: this technique may work for individuals or small businesses. For enterprise companies or organizations in the public sector like government or healthcare, the stakes are much higher. As a result, cybercriminals are less likely to lower the ransom price in such cases.
How to Protect Your Data From Ransomware
You’ve probably heard that having a backup is a key part of your data loss strategy. Unfortunately, this is not an all-covering solution anymore in terms of ransomware threats.
Unless you keep your backup copy offline and fully detached from the primary data, it is at risk of getting infected. Using backup solutions with inbuilt ransomware protection is another effective measure to prevent infection through secondary means.
Given the new tendencies, using only one method is insufficient. To get closer to maximal security, you must include a whole arsenal of your data protection strategy methods.
What you can do to protect from ransomware:
- Back up your data as frequently as possible. That determines how much data you can potentially lose during a ransomware attack. If you back up data every day, it means you can lose one day’s worth of data.
- Use automated ransomware protection services. This is a new type of protection that was rolled out as a response to the automation trend in the cybersecurity field. It detects a ransomware attack in progress and stops it before it can damage your primary data and backup.
- Educate yourself and the end-users. Read how do you get ransomware in the first place and how to protect against ransomware both if you are an individual or an organization.
- Implement a two-step authentication policy. It is a proven fact that passwords are the weakest point in the organization’s defense mechanism.
- Keep your OS and software updated. Always.
- Make antivirus/antimalware software utilization an obligatory part of your organization’s cybersecurity policy.
If managing each threat vector individually seems overwhelming or if you’re short on time and resources, consider trying our comprehensive SaaS data protection platform, SpinOne, for free. SpinOne offers an all-in-one solution that monitors, secures, and backs up your Google Workspace and Microsoft 365 data. By enhancing compliance measures and reducing IT costs, SpinOne provides peace of mind in safeguarding your valuable SaaS data.
Was this helpful?
How Can You Maximize SaaS Security Benefits?
Let's get started with a live demo
Latest blog posts
The History and Evolution of Ransomware
January 25, 2024Ransomware has become an efficient tool for illegal money extortion and achieving political goals worldwide.... Read more
Types of Cyber Security Threats in 2024 and How to Prevent Them
December 21, 2023Over the past decade, businesses have become extremely dependent on the IT environment for their... Read more
Ransomware in the Cloud: Challenges and Best Practices
December 13, 2023The rise of SaaS ransomware is quickly becoming a prevalent issue in cybersecurity as it... Read more


