Machine Learning-powered Cyber Threat Intelligence

In the previous post, we looked at Machine Learning (ML) and Artificial Intelligence (AI) in general terms. In this post, we’ll review how these technologies can be applied in cyber threat intelligence. Machine learning and artificial intelligence are both extremely powerful technology buzzwords these days. They play a crucial role in efficiently parsing and processing the vast amounts of available data in modern systems. Machine learning is a specialized form of AI that allows computers the ability to “learn” from data automatically.
They do this by using advanced algorithms to intelligently filter through data and find patterns and anomalies that are present therein. This allows computers to make decisions based on this type of data analysis for which they were not explicitly programmed. Artificial intelligence allows computers to perform unsupervised learning which amounts to being able to “teach” itself the ability to identify complex patterns or anomalies and make decisions based on these “self-learned” skills.
We looked at an introduction to how machine learning is being utilized in network and cybersecurity by looking at a great example of applied machine learning in SpinOne. In this post, we will look in more detail at how SpinOne utilizes machine learning in each of the cybersecurity feature sets. Our focus will be on providing automated analysis and remediation of cybersecurity events.
Utilizing Machine Learning for Cyber Threat Intelligence
Cybersecurity efforts today must make use of machine learning to be relevant and effective in today’s hybrid cloud environments. There is simply too much data at play and coming from multiple sources in a way that human detection of cybersecurity events would be extremely difficult, if not impossible.
SpinOne’s entire G Suite security solution is built around the power of machine learning and it is evident in SpinOne’s implementation of its cybersecurity modules. Let’s take a more detailed look at the following cybersecurity components of SpinOne’s solution and highlight the advantages of the way it puts machine learning into practice
High-Risk Third-party Apps Control
Allows SpinOne to detect malicious or dangerous third-party applications installed into the G Suite environment that result in a compromise of data.
Ransomware Protection
Powerful detection and remediation of ransomware infections affecting the G Suite environment.
Data Leak Detection
Detects unusual data patterns that may represent a leak of unauthorized G Suite data.
Sensitive Data Control
Enables SpinOne to detect sensitive data that exists inside of emails or documents and act upon that sensitive data accordingly.
Each of the above represents a powerful tool for organizations making use of Google’s G Suite environment and who are making use of a hybrid cloud environment spanning on-premise networks up to the Google public cloud.
High-Risk Third-Party Apps Control
Third-party applications found in the Google G Suite marketplace can add tremendous functionality and real business value to a corporate G Suite environment. Organizations can extend the default tools, utilities, functionality, features, and many other aspects by installing legitimate third-party applications providing those resources. However, the Google marketplace can potentially contain G Suite security risks to organization data. Today, with corporate employees making use of various devices, including corporate issue electronics and also BYOD devices, the need to stay vigilant in regards to cybersecurity is urgent.
Employees can easily, and often unwittingly, grant permissions to risky third-party applications. By just clicking “allow” on a message dialog, they can give these apps access to read data, contacts, location, SMS data, sensors, calendars, and many other types of sensitive information. Without even thinking, a single third-party application install can lead to a tremendous cybersecurity event where corporate data is leaked, stolen, or otherwise compromised. The above example underscores the need for organizations to be vigilant when it comes to third-party application installs that have access to G Suite data.
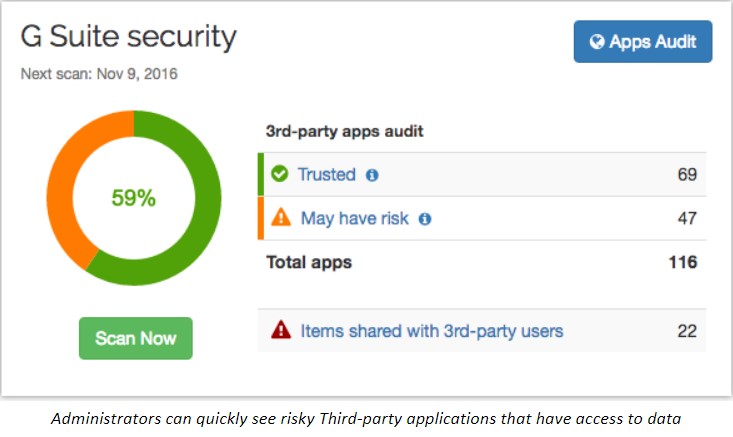
SpinOne’s solution employs potent machine learning to maintain control over third-party applications. This approach enables organizations to effectively reduce the risks associated with third-party app installations. SpinOne provides a 24/7 monitoring solution that allows running a daily automated scan of installed third-party applications that have been integrated into G Suite.
SpinOne is able to assess the risk of the installed third-party application and if it is found to be risky, it can remediate access to the third-party application in question. The underlying technology behind SpinOne’s ability to effectively scan and remediate risky third-party apps lies in powerful machine learning algorithms and AI.
Machine learning algorithms provide SpinOne with the ability to:
- Provide a real-time assessment of the third-party app
- “Profile” the third-party app and discover what its “intent” is by determining connections, data it has access to, employees it has access to, data flows to and from the third-party app
- Discover the types of connected devices and any discovered anomalies
SpinOne’s High-Risk Third-party App control allows it to detect when applications have started to inadequately work with data, suspicious email addresses, and other factors so as to determine what behavior is abnormal. SpinOne machine learning is able to build trends as to what normal application data usage and connections look like. It can thereby determine anomalies based on this historic usage and to what degree usage deviates from the normal baseline.
SpinOne is also able to identify if the installation itself is abnormal by monitoring the behavior of risky third-party application installs. Machine learning can determine if the installation is in line with normal G Suite administrator behavior or perhaps the work of an attacker or virus.
By looking at the login time, IP geolocation, SpinOne machine learning is also able to accurately identify a possible compromise of an account based on the historical “normal” login behavior. Any login anomaly that does not fit regular usage patterns is subject to the scrutiny of the machine learning algorithm.
G Suite Ransomware Protection
Ransomware is a nightmare for corporate environments and their business-critical data. Organizations today must be vigilant to protect both on-premise and public cloud environments from ransomware attacks. Public cloud environments can be the most difficult to manage simply due to the nature of the public cloud. Multiple users can connect from multiple devices and from multiple locations and networks.
Organizations do not have the traditional perimeter network and management tools they are accustomed to with public cloud environments. Additionally, simply staying ahead of the curve when it comes to fighting ransomware can be extremely difficult, especially in today’s hybrid cloud environments.
SpinOne’s G Suite ransomware protection and remediation are ahead of the curve when it comes to protecting organizations from current and future threats. By utilizing intelligent machine learning, the SpinOne ransomware protection module is able to detect anomalous behavior that is characteristic of ransomware infection such as rogue processes changing large numbers of files, irregular file extensions, or otherwise abnormal behavior.
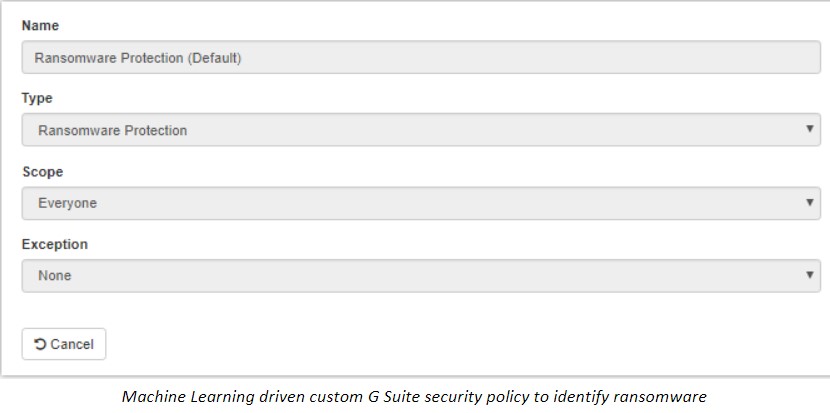
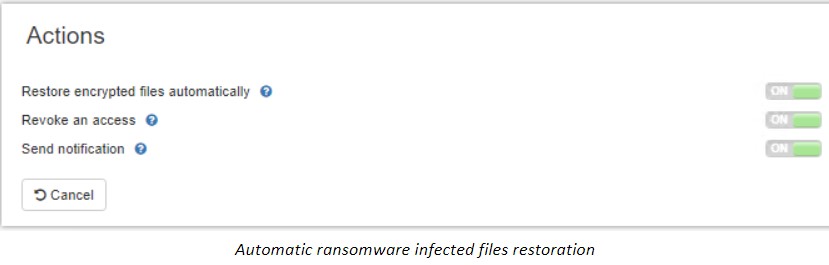
SpinOne’s machine learning enabled ransomware protection module allows for:
- Detecting Ransomware Infections
- Automatically placing a block on Ransomware encryption processes that are actively damaging files
- Accurate identification of files that have been encrypted and automatically restoring them
- Versioning file so that previous versions can be restored before ransomware damages them
- Automated administrative security alerts
If we think about what it would take for a human being to scan through an entire G Suite environment and detect files that may actively be undergoing encryption and identify the processes responsible, this would be an almost impossible task. However, SpinOne’s machine learning algorithms take the heavy lifting out of the process by constantly analyzing the data presented and detecting the abnormalities. When it comes to ransomware protection, there is no human alternative to powerful, intelligent machine-learning algorithms.
Data Leak Detection
One of the most catastrophic events that can potentially happen to an organization is to have sensitive data leak to unauthorized individuals or entities. These are the types of events that make headlines and can literally take a business out of business overnight! Data is becoming more and more precious.
When you look at how data rights and other compliance standards are being developed such as the new GDPR regulations, it is obvious to see that organizations must view protection of G Suite data and especially sensitive data as a top priority. As is the case with the other challenges mentioned above, sensitive data control in the realm of a hybrid cloud can be extremely difficult. This is where additional machine learning algorithms implemented by SpinOne can pay dividends when it comes to protecting business-critical and sensitive data.
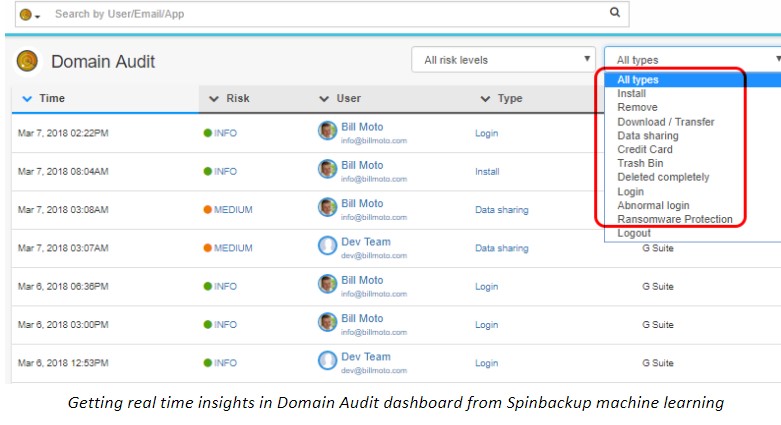
When you think about the types of data leak events that can potentially happen – these can amount to both intentional or unintentional actions by someone on the inside (employee), malicious attacker, or virus. Again, this is where SpinOne machine learning comes into play by detecting data that is traversing from the G Suite environment in an unauthorized way. This could be detecting an employee who is downloading inordinate amounts of company data locally or trying to copy G Suite data to another cloud environment (personal cloud environment).
Insider threats can pose a significant danger to organizations. Using SpinOne’s Domain Audit functionality, organizations can gain tremendous visibility to employee actions including the suspicious downloading of data locally or to personal cloud environments and many others. All of the insights are provided using SpinOne’s powerful machine learning.
Sensitive Data Control
Besides general G Suite data leak prevention, SpinOne can pinpoint data that is sensitive such as information containing credit card numbers. In general, sensitive information may cover a wide range of subjects including credit card numbers, social security numbers, PII (personally identifiable information), HIPAA information, etc. Businesses today must be vigilant to protect all types of sensitive data.
Machine learning provides a powerful use case when it comes to tagging and classifying sensitive data. With the enormity of files and other data that potentially exist via email and Team Drives, it would be impractical at best and impossible at worst for a human being to open and correctly identify all sensitive data that may exist across an organization.
However, a machine learning algorithm can scan files very quickly and efficiently and automatically determine any sensitive data violations that may exist. SpinOne’s powerful G Suite sensitive data control classifiers allow creating custom data protection rules that leverage machine learning to both classify data and yield an automatic triggered response.
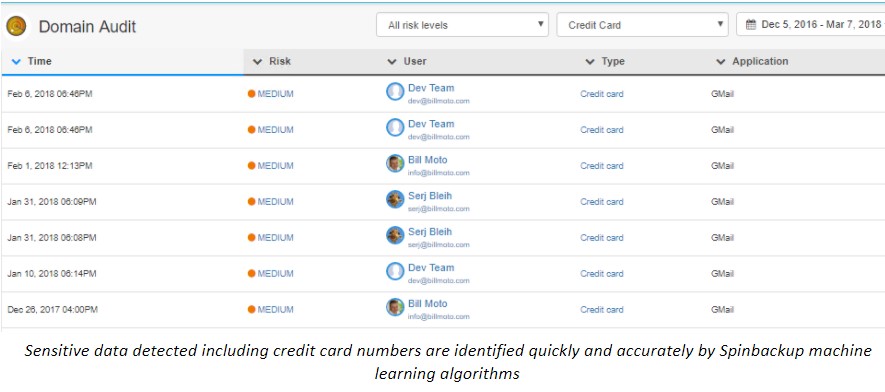
SpinOne’s sensitive data protection that is bolstered by machine learning algorithms allows organizations to solve the complicated issues resulting from data housed in the G Suite public cloud and effectively identify sensitive data before it is leaked.
Advantages of Machine Learning for Cyber Threat Analysis
Machine learning is not simply a “nice to have” feature of cybersecurity, it is required if organizations are able to stay on top of and ahead of cybersecurity threats that exist in the wild. Public cloud environments add a whole new layer of complexity on top of securing on-premise environments. Without the proper tooling and cybersecurity mechanisms in place, public cloud environments such as Google’s G Suite can be exposed to a wide range of cybersecurity risks.
SpinOne’s cybersecurity solution for G Suite environments is a great example of powerful machine learning algorithms in practice. SpinOne’s implementation of such G Suite security modules as High-Risk Apps Control, Ransomware Protection, Data Leak Protection, and Sensitive Data Control makes use of intelligent machine learning threat intelligence that allows both effective and efficient mitigation of critical cybersecurity threats. SpinOne best G Suite backup and security solution provides organizations with the peace of mind and confidence that data is protected in the public cloud.
Machine learning algorithms are changing the landscape of cybersecurity and helping to level the playing field with attackers whose attention is focusing more and more on public cloud environments.
Changes to the cybersecurity enhancement process will not happen overnight. Check out SpinOne’s Ultimate G Suite Security Guide and start making those changes right now!
Frequently Asked Questions
What is the impact of machine learning on cybersecurity?
Machine learning (MI) can both enhance cybersecurity capabilities and empower criminals with new cyber attack methods.
On one side, machine learning revolutionizes cybersecurity by relying on a proactive defense approach. It allows devices to filter through the bulks of data, “learn” from that data, identify complex cybersecurity patterns or anomalies, and make decisions based on these “self-learned” skills.
On the other side, machine learning provides criminals with advanced tools for cyber attacks. This includes either the automation of cyberattacks or the development of sophisticated phishing and social engineering attacks by the creation of deepfakes, disinformation campaigns, deceitful websites, AI-powered scam bots, etc.
Can machine learning be used for cyber security?
Yes, machine learning is widely used for enhancing cybersecurity by providing advanced opportunities for threat detection, vulnerability management, adaptive security, and adaptive responses. For instance, SpinOne’s security solution is built around the power of machine learning to ensure high-risk third-party apps control, ransomware protection, data leak detection, and sensitive data control.
What are AI-powered cyber attacks?
AI-powered cyberattacks refer to cyberattacks that leverage artificial intelligence (AI) and machine learning (ML) techniques to enhance their effectiveness and sophistication. These attacks use AI not only to automate certain tasks but also to adapt, learn, and evolve in real time, making them more challenging to detect and mitigate. Examples of AI-powered attacks include advanced persistent threats (APTs), brute-force cyberattacks, AI-powered malware, DDoS Attacks, zero-day exploitations, social engineering, etc.
Was this helpful?
How Can You Maximize SaaS Security Benefits?
Let's get started with a live demo
Latest blog posts
How to Restore A Backup From Google Drive: A Step-by-Step Guide
April 10, 2024Backing up your Google Drive is like making a safety net for the digital part... Read more
Protecting Partner Margins: An Inside Look at the New Spin.AI Partn...
April 2, 2024Google recently announced a 40% reduction in the partner margin for Google Workspace renewals –... Read more
Expert Insights: SaaS Application Data Protection Fundamentals
March 21, 2024SaaS applications appeal to organizations because they make running the application “somebody else’s problem.” However,... Read more


