Microsoft Cloud App Security Concerns

Microsoft Cloud App Security: Let’s Talk About It. Microsoft Office 365 is one of the most powerful business productivity suites housed in the public cloud today. Today, many businesses are using Microsoft’s Office 365 environment. They are either running business-critical services and applications or considering moving prem to the public cloud. Office 365 indeed touts some great benefits for organizations looking to move to the public cloud. As with any technology solution used for business today, it must be scrutinized for potential security risks.
Are not public cloud environments immune to the common security risks to business data that lives on-prem? Hardly! Many today have a huge misconception that simply moving to the cloud eliminates many of the significant security concerns in on-prem environments. Microsoft has taken a few steps in the right direction in terms of security for its Office 365 customers. However, there are still concerning security gaps in Microsoft’s Office 365 environment that businesses need to be aware of. Let’s look at some of the security concerns in Office 365 today and why organizations mustn’t take these lightly.
On-prem vs. Cloud – No more security risks, right? Wrong!
A common misconception among many when considering moving to the public cloud is that security concerns such as Ransomware that can have significant impacts within-prem environments do not apply to the public cloud. Many may think that since the servers do not exist in your enterprise data center, the data contained on public cloud servers is untouchable by threats that utilize Ransomware or other means to compromise data. However, this is an extremely dangerous assumption to make comparing the security of on-prem with the public cloud.
As is the case, public cloud architecture is vastly different from on-prem enterprise datacenters. However, attackers can still prey upon essential security holes and utilize phishing techniques to lure unsuspecting end-users into running executables or installers that ask for permissions to their public cloud-stored data or emails.
Also essential to consider is the threat vector of file synchronization. Most public cloud environment providers such as Google and Microsoft provide utilities for synchronizing files from on-prem devices up to cloud storage. Microsoft’s One Drive on an on-prem device synchronizes changes to the cloud. It is easy to see how security events affecting on-prem environments are easily extended to the public cloud with file synchronization. If Ransomware starts encrypting files on-prem, One Drive views the files as “changed” and would trigger a synchronization with the One Drive public cloud.
There is no doubt that attackers today are shifting their focus to public cloud environments. After all, this is where businesses today are storing more and more of their data. Adding to the challenge of public cloud security, the native public cloud security mechanisms that exist are either misunderstood, underutilized, or improperly configured. Traditional security models that have worked for years on-prem are not good enough with the complex and easily accessed public cloud resources that today’s providers make available.
The security risks and dangers associated with the public cloud will only evolve with today’s attackers targeting these treasure troves of data and the potential for exploitation. What about the native tools that public cloud vendors such as Microsoft provide for public cloud customers that utilize services such as Office 365? Are the security mechanisms offered good enough to protect organizations today from the potential for data loss or data leak? What about cybersecurity in general? Let’s look at Microsoft Office 365 native security tools and features and explore just how much protection these afford to Office 365 customers.
What is Microsoft Cloud App Security
Microsoft offers its native security solution for protecting Office 365 environments called Cloud App Security. Cloud App Security is Microsoft’s comprehensive cross-SaaS solution engineered to bring deep visibility, data controls, and enhanced threat protection to cloud apps. Through this offering, Microsoft wants to allow customers to gain visibility into Shadow IT and other potential security risks to Microsoft public cloud environments.
Microsoft makes a distinction between Cloud App Security and Office 365 Cloud App Security which, as it describes, is a subset of Microsoft Cloud App Security that provides enhanced visibility and control for Office 365. As it describes, the Office 365 Cloud App Security variant provides threat detection based on user activity logs, the discovery of Shadow IT for apps that have similar functionality to Office 365 offerings, and control app permissions therein.
Microsoft places this as a critical component of the Cloud Security stack. It is positioned to help organizations with the challenge of moving from on-premises environments to cloud-hosted solutions by providing the tools to gain control and visibility in cloud applications and is set to protect critical data across cloud applications.
There are quite a few differences to be noticed regarding security capabilities between Microsoft Cloud App Security and Office 365 Cloud App Security. At first glance, the Office 365 Cloud App Security offering is a much more lightweight offering when compared to Microsoft Cloud App Security. You can see that Office 365 Cloud App Security is not as fully featured and robust as the Microsoft Cloud App Security offering via the official comparison made by Microsoft.
| Capability | Feature | Microsoft Cloud App Security | Office 365 Cloud App Security |
|---|---|---|---|
| Cloud Discovery | Discovered apps | 16,000 + cloud apps | 750+ Cloud apps with similar functionality to Office 365 |
| Deployment for discovery analysis | Manual and automatic log upload | Manual log upload | |
| Log anonymization for user privacy | Yes | ||
| Access to full Cloud App Catalog | Yes | ||
| Cloud app risk assessment | Yes | ||
| Cloud usage analytics per app, user, IP address | Yes | ||
| Ongoing analytics & reporting | Yes | ||
| Anomaly detection for discovered apps | Yes | ||
| Information Protection | Data Loss Prevention (DLP) support | Cross-SaaS DLP and data sharing control | Uses existing Office DLP (available in Office E3 and above) |
| App permissions and the ability to revoke access | Yes | Yes | |
| Policy setting and enforcement | Yes | ||
| Integration with Azure Information Protection | Yes | ||
| Integration with third-party DLP solutions | Yes | ||
| Threat Detection | Anomaly detection and behavioral analytics | For Cross-SaaS apps, including Office 365 | For Office 365 apps |
| Manual and automatic alert remediation | Yes | Yes | |
| SIEM connector | Yes. Alerts and activity logs for cross-SaaS apps | Yes. Office 365 alerts only. | |
| Integration to Microsoft Intelligent Security Graph | Yes | Yes | |
| Activity policies | Yes | Yes |
There are three main components to the Cloud App Security platform: the Security Framework for the solution, enabling organizations to map out and identify cloud apps, sanction and unsanctioned apps in the cloud, deploy app connectors and configure policies.
- Cloud Discovery – A discovery mechanism for all the apps in use in the organization
- Data Protection – Monitoring and control mechanism for increased visibility, DLP policies, alerts, and forensics
- Threat Protection – Detects anomalies in user activity, behaviors, and other activity-related metrics and provides advanced investigation tools that help configure policies and alerts.
The architecture of the Microsoft Cloud App Security platform as outlined by Microsoft:
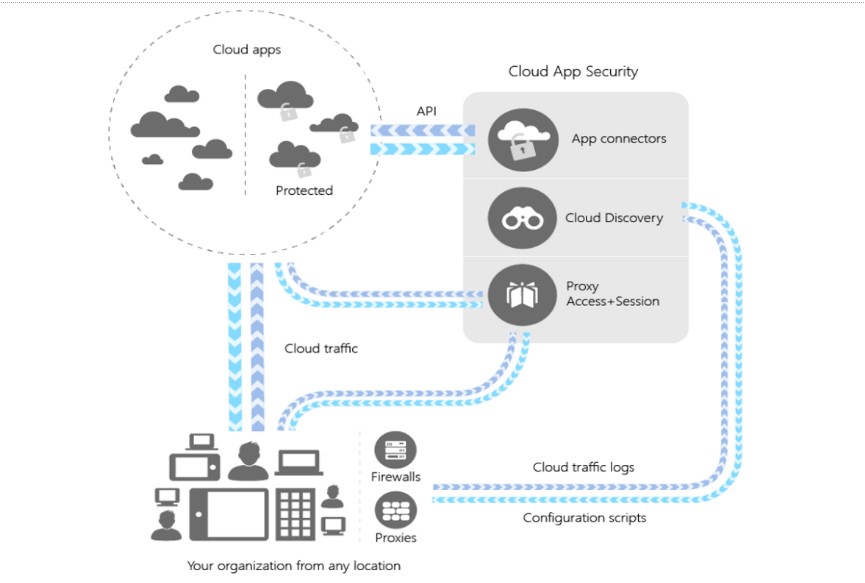
Cloud App Security uses traffic logs to discover and analyze cloud apps found and utilized within the organization with the Cloud Discovery mechanism.
Cloud Discovery
Cloud App Security uses traffic logs to discover and analyze cloud apps found and utilized within the organization with the Cloud Discovery mechanism. It allows manually uploading log files from the firewall, proxies, and other devices for analysis. Log collectors can be configured, allowing the continuous upload of these types of logs to Cloud App Security.
Sanctioning and Unsanctioned an app
Microsoft maintains an ever-growing list of apps by way of a Cloud app catalog. These apps are ranked and scored based on industry standards, and risk is assessed based on several metrics, including these standards and other factors.
App Connectors
App connectors leverage APIs provided by cloud app providers to allow tight integration with Cloud App Security. These integrations extend control and protection between third-party cloud app providers.
Conditional Access App Control Protection
Microsoft Cloud App Security Conditional Access App Control Protection uses reverse proxy architecture. This allows real-time visibility and control over access to resources and activities performed by end-users in the cloud environment. These capabilities include:
- Data Leak protection by blocking downloads
- Enforce encryption rules with downloaded content
- Ensure visibility with endpoints that are unprotected or unmanaged
- Control non-corporate network access or filter dangerous IP addresses
Policy Control
Administrators can set policies to define what users can and can’t do in the cloud. This includes detecting risky behavior and suspicious data downloads. Remediation processes can be put in motion that allow mitigating dangerous user activities.
Pricing
Microsoft’s Cloud App Security is available for purchase a subscription for $3.50 per user per month retail. It is also included as part of the Microsoft Mobility + Security E5 offering.
Microsoft’s Cloud App Security provides a good step in the right direction. However, are there security gaps that exist, even with using Cloud App Security and, in particular, Office 365 Cloud App Security? There are certainly Cloud App Security shortcomings and security concerns that organizations need to be aware of when relying on Microsoft’s solution for providing cloud security for their environments, especially Office 365. What areas do Cloud App Security fall short, and why should organizations be concerned about this?
Microsoft Cloud App Security Shortcomings
Microsoft’s solution for cloud security certainly has merit and is a solution that one can easily take advantage of natively with Microsoft’s cloud ecosystem. However, for businesses looking for the best solution for Office 365 security, Microsoft’s Cloud App security may come up a bit short as it relates to Office 365.
As stated by Microsoft, the Office 365 Cloud App Security offering is a subset of Cloud App Security. Being a subset means not including functionality and features as the parent Cloud App Security solution. Be sure to review the table above for a detailed listing and comparison of features and functionality between the two. Let’s focus on the following areas and gaps that exist in the Office 365 Cloud App Security option for businesses housing resources in Office 365:
- Limited App Discovery and Risk Assessment
- DLP capabilities are limited
- Limited Threat and Anomaly Detection
- Threat Remediation and Response can be lacking
- No Backup and Recovery Capabilities
Let’s look at each of these a bit closer to see in greater detail the security gaps that businesses need to know when using Microsoft’s Cloud App Security to protect Office 365 environments.
Limited App Discovery and Risk Assessment
One component of today’s public cloud environments that can pose significant security risks involves third-party applications integrated with Office 365. This is particularly true given the modern cloud-enabled workforce. End users tend to blindly grant permissions to requested data and other resources when prompted by third-party applications. This can easily allow integration with corporate data for risky third-party applications.
With Cloud App Security, Microsoft documents visibility to more than 16000+ cloud apps. However, with Office 365 Cloud App Security, only 750+ cloud apps with similar functionality to Office 365 are established as part of the cloud discovery capabilities of Office 365 Cloud App Security. So, with the Office 365 variant, businesses get a much cut-down version of the cloud discovery capabilities with Cloud App Security.
As will be discussed later, the governance actions depend on these app integrations with Office 365 and Cloud App Security to be used for effective security remediation. This certainly leaves room for a gap in protection for applications integration with Office 365 Cloud App Security.
DLP Capabilities Are Limited
Data Loss Prevention or DLP is a massive concern for businesses today. Data leakage can cost enterprises their existence with potential financial and reputation damage amounting to more than the organization can bounce back from. With new data protection regulations such as General Data Protection Regulation or GDPR, businesses must be vigilant and proactive when protecting customer data.
With Office 365 Cloud App Security, the DLP solution is only available to businesses utilizing the E3 subscription and above with Office 365. Those businesses with lower Office 365 subscription levels do not have access to the DLP functionality provided by Cloud Access Security. This leaves organizations that do not have the business needs for the Office 365 Enterprise E3 and higher subscriptions with the dilemma of cost vs. security, which generally never turns out well for the security side of things.
Not having the option for effective DLP as a service in the lower level subscriptions with Office 365 leaves a significant security gap for smaller and SMB organizations looking to bolster data leak protection across their Office 365 landscape. In some cases, organizations can bolt on individual pieces of the DLP solution. However, this leaves businesses paying more for bits and pieces of a proper all-in-one DLP solution.
Limited Threat and Anomaly Detection
Microsoft’s Office 365 Threat Intelligence offering helps security analysts and administrators protect their organization’s Office 365 users by helping to identify and monitor attacks from threat actors, address threats in Exchange and SharePoint Online.
However, with Office 365, the advanced threat management you get is tied to the Business and Enterprise plans that organizations subscribe to what Microsoft describes as “Advanced Threat management,” which includes customer lockbox and threat explorer for phishing campaigns tied to the Office 365 E5 subscription. Essential “Threat Management” is described as mail filtering and anti-malware only can be had with subscription levels from office 365 Business Essentials, all the way to the Office 365 Enterprise E5 subscription.
Threat Response and Remediation
When considering the capabilities of any threat protection or security add-on for Office 365, the power displayed by any solution often comes from its ability to perform automated responses and proactive actions to provide security within the public cloud environment. Microsoft has incorporated alerting mechanisms into the Cloud App Security module. These can trigger notifications for suspicious activities, such as external sharing or downloading of sensitive files. Custom alerts can be created that contain the following policies:
- Activity policy
- Anomaly detection policy
- App discovery policy
- Cloud Discovery anomaly detection policy
- File Policy
Governance actions can be taken based on the specific type of policy being implemented—an example of configuring a governance action on a Cloud App Security policy is below.
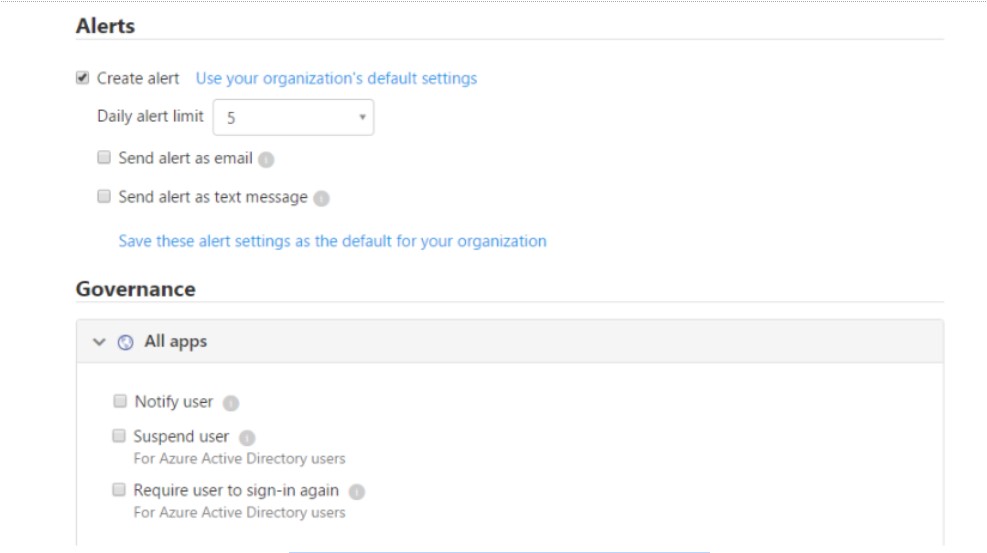
Governance actions with Microsoft Cloud App Security applications
However, a point to note here is that governance actions or remediation actions as described by Microsoft use the cloud provider APIs and might vary from one app to another. A security note to be made here and a potential gap as well – it is less than desirable to rely on third-party app APIs as these will vary from vendor to vendor to determine the governance action that can be taken.
One of the other security responses documented with Cloud App Security allows triggering a user to log in again when suspicious activity is detected on an account. The logic here is that when an attacker gains unauthorized access to an account, simply disabling the account does not invalidate the currently logged-in sessions, so potentially an attacker still has access—requiring another login forces authentication on the credentials again. While requiring a user to reauthenticate is an excellent first step, it would be nice to see additional capabilities here.
The capabilities to contain or prevent Ransomware with Microsoft Cloud App Security are limited as well. Security professionals have demonstrated, how an unsuspecting user might inadvertently encrypt their entire Office 365 email inbox. This can occur by simply granting the app permission for email integration, such as with a fraudulent WebEx plugin. An attacker can deliver a ransomware payload that encrypts all emails in a user’s mailbox by impersonating a legitimate app. There is no built-in process with Cloud App Security that can restore email data once the process begins, leading to the following security gap – no backup and recovery options.
Limited Backup and Recovery Options
One of the glaring security gaps with most security add-ons from public cloud vendors and third parties is the lack of effective backup or recovery options. Although numerous crucial components of security are often addressed by third-party solutions, backup and recovery is an area frequently overlooked. Often, it is dismissed as merely the responsibility of a “backup solution.”
Many may not think of backups as part of security. However, backups should prove to be a cornerstone in design when architecting any security solution. For instance, if Ransomware activity is detected, this does not “undo” the damage to files caused by Ransomware affecting OneDrive Storage or even email. Even if the progression of the ransomware infection is stopped, the downtime that could result from already damaged or encrypted files could be catastrophic.
With Microsoft’s Advanced Threat Protection or Cloud App Security, there are limited backup and recovery features for Office 365. With OneDrive for Business, customers can restore files for up to 30 days that have been deleted, infected, or otherwise corrupted. However, business customers can only restore OneDrive files with this restore option and not other Office 365 services. The granularity of restores is also limited.
Organizations need the capability to back up all business-critical services hosted on the Office 365 infrastructure. Furthermore, they must be able to recover files and services as an integral part of their comprehensive security strategy. Data protection must be required for businesses looking to house business-critical data in the public cloud, including Office 365. There will never be an impenetrable security solution. Companies must plan for and expect the day when data in the public cloud must be restored.
Microsoft Cloud App Security: Concluding Thoughts
Microsoft Office 365 is a powerful platform for today’s businesses to migrate data and services to the public cloud. Microsoft has come a long way in providing security for Microsoft Office 365 customers looking to bolster security. With Microsoft Cloud App Security, Microsoft has introduced a platform that allows customers to have some basic security features and functionality to protect Microsoft Office 365 environments.
However, businesses should be aware that there are gaps in the security coverage provided by Microsoft Cloud App Security. This also applies to other Microsoft security offerings, including the Advanced Threat Protection module. The effectiveness of automated responses and governance lies in the integration between the app and Office 365.
Despite not having Apps integrations with Microsoft Office 365, Microsoft Cloud App Security offers limited capabilities. One of these is the ability to restore data that might have been corrupted or damaged during a security event like a ransomware attack. Data protection should play a vital role in the security of Office 365 or any other public cloud environment. Additionally, threat responses and alerting provide only basic capabilities. While native Microsoft tools have come a long way, it is evident that more is needed to secure Microsoft Office 365 environments.
Resource: https://learn.microsoft.com/th-th/defender-cloud-apps/editions-cloud-app-security-o365
Frequently Asked Questions
What is the Microsoft Defender for Cloud Apps (Microsoft Cloud App Security)?
Microsoft Defender for Cloud Apps (formerly Microsoft Cloud App Security) is a Cloud Access Security Broker (CASB) that functions across various cloud environments. It offers extensive visibility, the ability to manage data movement, and advanced analytics for the detection and mitigation of cybersecurity threats across all your cloud-based services.
What are the main uses of Microsoft Defender for Cloud Apps (Microsoft Cloud App Security)?
Consider using Microsoft Defender for Cloud Apps if your organization relies on cloud-based applications and services. Microsoft Defender for Cloud Apps is beneficial for enhancing cloud app visibility, preventing data leaks, detecting and responding to cybersecurity threats, getting tools to help ensure that cloud apps meet compliance requirements, implementing advanced access controls, enhancing overall security posture and addressing the challenges associated with cloud app usage.
What are the features of Microsoft Defender for Cloud Apps (former Microsoft Cloud App Security)?
Microsoft Defender for Cloud Apps helps protect SaaS applications by monitoring and protecting cloud app data across the following feature areas:
- Cloud Access Security Broker (CASB) Functions: This includes detecting unauthorized cloud app usage (Shadow IT), gaining visibility in how cloud apps are being utilized, defending against threats originating from cloud environments, and evaluating data protection and compliance.
- SaaS Security Posture Management (SSPM): Helps enhance the organization’s overall security stance, providing tools and insights to bolster protection.
- Advanced Threat Defense: Enables correlation of signals and visibility throughout the entire lifecycle of advanced attacks.
- App-to-App Security: Expanding the core threat scenarios to OAuth-enabled apps that possess permissions and privileges related to critical data and resources.
Was this helpful?
- On-prem vs. Cloud – No more security risks, right? Wrong!
- What is Microsoft Cloud App Security
- The architecture of the Microsoft Cloud App Security platform as outlined by Microsoft:
- Microsoft Cloud App Security Shortcomings
- Limited App Discovery and Risk Assessment
- DLP Capabilities Are Limited
- Limited Threat and Anomaly Detection
- Threat Response and Remediation
- Limited Backup and Recovery Options
- Microsoft Cloud App Security: Concluding Thoughts
- Frequently Asked Questions
How Can You Maximize SaaS Security Benefits?
Let's get started with a live demo
Latest blog posts
Reducing Browser Extension Risk with Spin.AI Risk Assessment + Perc...
April 24, 2024Spin.AI is collaborating with Perception Point: integrating the Spin.AI Browser Extension Risk Assessment within the... Read more
How to Restore A Backup From Google Drive: A Step-by-Step Guide
April 10, 2024Backing up your Google Drive is like making a safety net for the digital part... Read more
Protecting Partner Margins: An Inside Look at the New Spin.AI Partn...
April 2, 2024Google recently announced a 40% reduction in the partner margin for Google Workspace renewals –... Read more


