Spin.AI Releases Google Workspace Security Policies

Organizations moving to the public cloud are faced with serious challenges to security and security related processes. Security teams in organizations with on-premise infrastructure have control over securing data access. They also have control over data loss prevention. Additionally, they have control over ensuring data security.
When moving to the public cloud, however, how can organizations provide this same, or even superior, level of data protection, data leak prevention, and data security?
SpinOne is an essential solution for organizations moving to Google G Suite Suite or Microsoft Office 365 cloud platforms. It offers high-level security and protection for important business data, all in one convenient product.
Recently, an exciting new feature set has been added to SpinOne’s Cybersecurity functionality, called Custom G Suite Security Policies. Let’s take a closer look at what exactly Custom G Suite Security Policies are and how we can create them.
What are SpinOne G Suite Security Policies?
The new G Suite Security Policies functionality allows for the added ability to customize policies for Apps, Data, and Domain-related event types. This gives G Suite administrators much greater control over their public cloud environments. They have the ability to set rule scopes, exceptions, and notification settings on a per-rule basis, which provides much greater flexibility.
Organizations may need to allow exceptions or scope a rule for policy-driven actions according to their individual business and security needs. With Custom Policies, it is now possible to create a custom policy-driven framework for actioning security events.
The new Custom Policies provide a number of very granular rule types that can be found within the scope of the Apps, Data, and Domain audit policies. The new Rule types include the following definable custom policies:
Data Audit Policies
DAP is intended to eliminate all main Google Workspace security risks.
- Shared Items Control – This disables the sharing of specific files to certain domains (including external) and specific users. Ownership can be changed on the specific files to the designated user. Notifications can also be sent for the specific event.
- Ransomware Protection – A powerful custom policy that enables automatic actions to be taken when Ransomware encryption and synchronization events are detected. The actions include restoring encrypted files automatically, revoking access to the synchronizing application, and sending notifications for encryption events.
- Sensitive Data Detection (CCN) – Identifies and notifies the Google Workspace Administrator of messages containing sensitive information such as a credit card (CCN).
- Restore Filtration – Prevents restoring emails that have been marked with predefined subjects, sender email addresses, or domain names.
Domain Audit Policies
- Abnormal Download Detection – Notifies G Suite administrators when a user downloads a specified number of files in bulk, or when an unauthorized application is used for cloud-to-cloud synchronization.
- Abnormal Login Detection – This policy notifies the G Suite Administrator when a brute force login attack has been detected.
Creating SpinOne Custom Policies
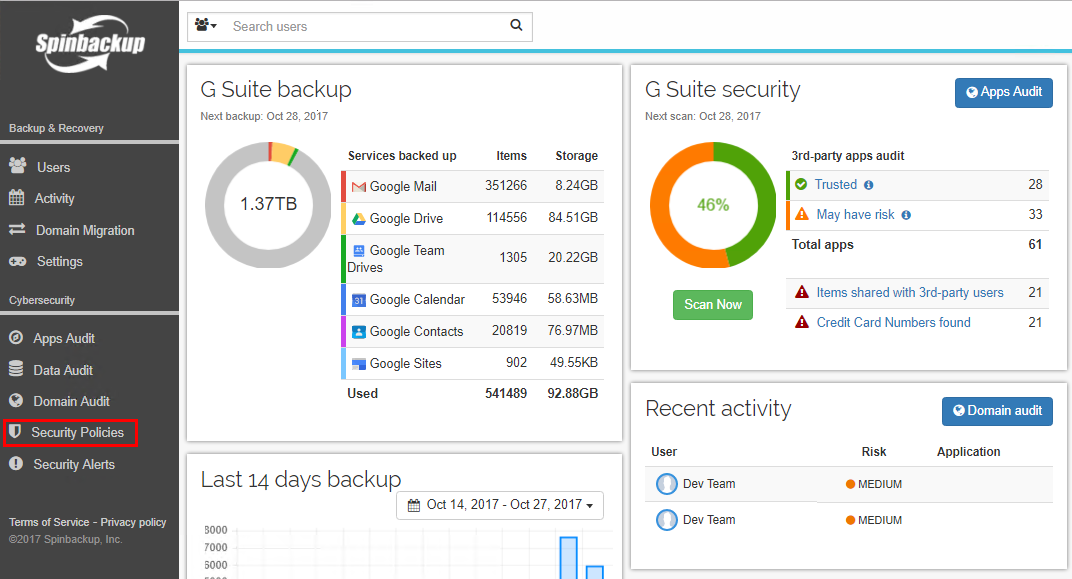
Navigate to Security Policies to launch the new Custom Policies interface
To create a new Custom Policies rule, we can click the Create Rule button at the top of the page. Additionally, we can use the Change priority button to change the order of the Custom Policy rules. These are processed from top down. Rules can also easily be enabled or disabled with the “On/Off” switch in the interface, making it easy to bring rules online or to take them offline without removing them completely.
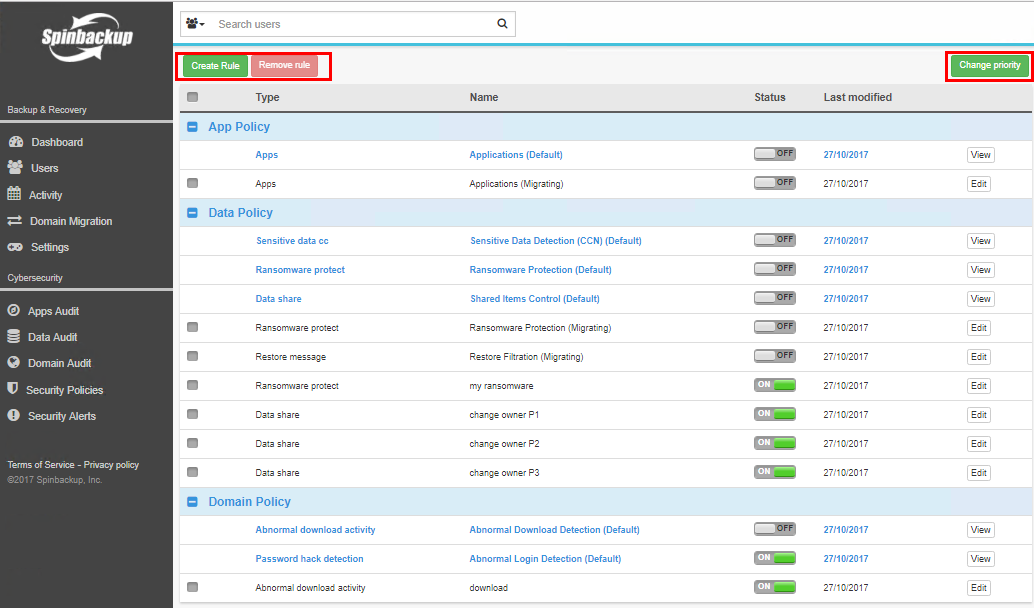
Using the Custom Policy interface, we can Create, Remove, and Change the Priority of rules
The new rule can be created in a very simple “3-step” process that involves setting the Scope, determining the Conditions And Actions, and then finally reviewing the configuration in the Summary screen. In Step 1 (Scope), we determine the “scope” of the rule by naming, creating a description, choosing the rule type, setting the scope (who it applies to), and setting exceptions.
In Step 1, we define the scope of the new Custom Policy rule
Next, in Step 2, we define the Conditions and Actions which allows us to setup rule options that are specific to each rule type created. Most rules’ conditions and actions involve setting the rule type specific action and notification options.
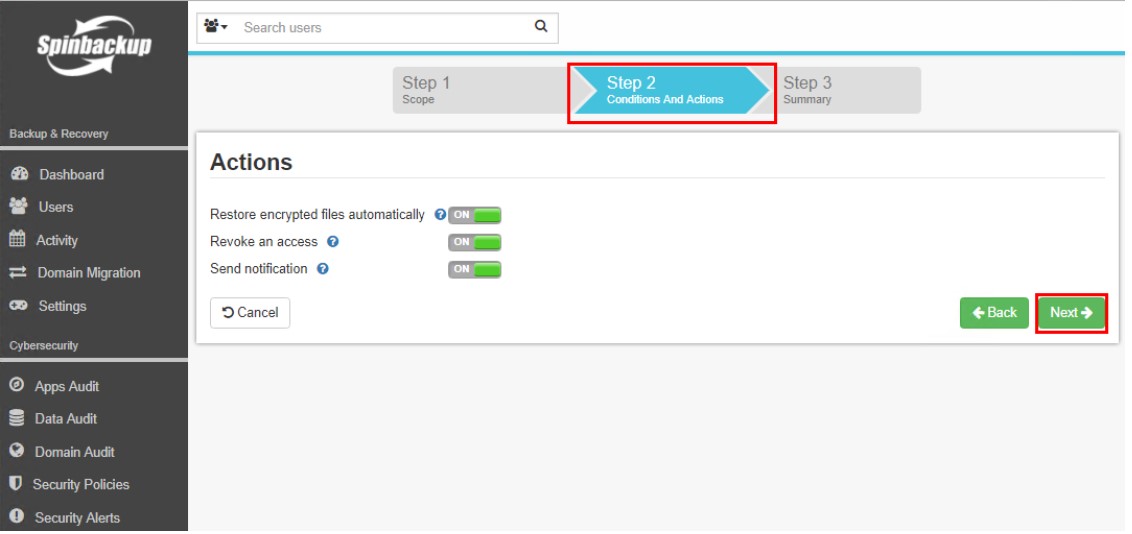
In Step 2, we configure the Conditions and Actions
In Step 3, which is the final step, we validate our configuration options. Once we validate, we click the Create button to create the new Custom Policy rule.
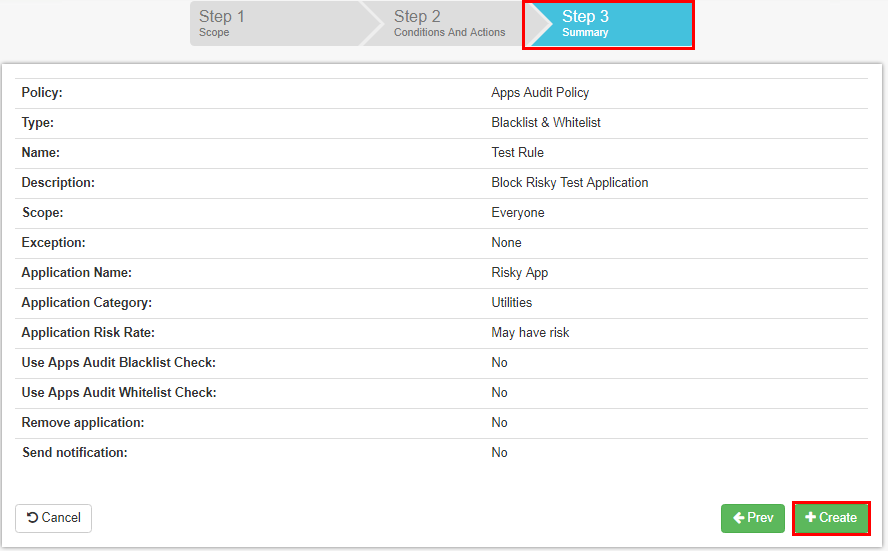
Verify the new Custom Policy rule in Step 3 before creating
Thoughts
Cybersecurity in the public cloud is one of the most pressing security topics that organizations today have to think through with their overall security strategies. Public cloud is difficult for organizations used to controlling everything on-premise. They may struggle with the challenges of public or hybrid cloud infrastructure.
By utilizing forward-thinking solutions such as SpinOne, organizations are able to successfully execute data migration of their employees and still maintain data protection, loss prevention, and data security. The addition of Custom Google Workspace Security Policies provides the continued evolution of exciting technology from SpinOne.
The new Custom Google Workspace Security Policies feature enables Google Workspace administrators to apply Cybersecurity policies to public cloud environments. This can be done in a flexible and detailed manner.
The new rule types offer a great amount of coverage to the types of security events that organizations are able to control and remediate. Organizations can leverage these powerful cybersecurity features to provide a flexible, secure, and agile approach to managing data security in the public cloud.
Was this helpful?
How Can You Maximize SaaS Security Benefits?
Let's get started with a live demo
Latest blog posts
Importance of Backing Up Google Workspace Data Daily
January 23, 2024Many organizations today are heavily relying on cloud Software-as-a-Service offerings for business productivity, communication, and... Read more
Google Workspace in 2024: Key Updates and Features
December 14, 2023Google Workspace is constantly improving to bring new productivity features for businesses. In this article,... Read more
How to Implement Data Leak Prevention in Google Workspace
October 27, 2023Data leaks in Google Workspace can have severe legal, financial, and reputational implications for the... Read more


