The Best Ransomware Protection for Google Workspace and Office 365: SpinOne

If you are here, you probably know what is ransomware and how ransomware works. Ransomware protection is necessary for any organization, as ransomware attacks entail significant costs, plus data recovery and downtime processes can last for many weeks.
SpinOne is a fully automated end-to-end ransomware protection solution. Our platform doesn’t require human involvement to detect, stop, and recover from a ransomware attack.
Here is how to get the best ransomware protection for your Google Workspace or Office 365 data.
How Ransomware Infects Your System?
Ransomware authors come up with sophisticated tactics to catch you off-guard. There are five main ways to get a ransomware infection:
- Phishing emails
- Exploit kits
- Brute force attacks
- Malicious apps and extensions
- Infected executables
You can get more details in our article, revealing 5 main ransomware sources.
SpinOne: Backup + Ransomware Protection + Apps Audit
SpinOne provides complete ransomware protection solutions for Google Workspace (G Suite) and Office 365. It combines backup and ransomware protection functionality to counter the ransomware threat.
SpinOne leverages Machine Learning-enabled ransomware protection methods to detect ransomware attacks. Our algorithms analyze file-level behavior for any anomalies and if they recognize ransomware encryption patterns, they block the source of the attack and revoke access to the user account to stop any further encryption processes.
After that, all damaged files are restored from a safe backup. The whole process is automated.
SpinBackup: Backup and Recovery Solution
Backup is a safe copy of your data that can be used to restore it in case of an emergency. Ransomware encrypts your files, and backup is the best way to get them back.
Automated SpinBackup solutions for Google Workspace and Office 365 ensure 100% accurate recovery, as backups are stored safely in the cloud of your choice (GCP, AWS, or Azure). SpinBackup keeps multiple versions of backed up data available for recovery at any time.
SpinSecurity: Ransomware Protection
Though backup helps to restore the ransomware-damaged files, there is still a risk of having your sensitive data leaked. That’s why stopping a ransomware attack early is vital. In addition to backup, we offer ransomware protection solution – SpinSecurity.
SpinSecurity Ransomware Protection helps to identify an attack and block its source, keeping the number of affected data as low as possible. After the threat has been neutralized, all encrypted files are recovered from SpinBackup.
SpinAudit: Additional Cybersecurity Features for Google Workspace (G Suite) Users
Aside from the Ransomware Protection module included with SpinOne, we have an additional cybersecurity solution SpinSPM. Additional security features include:
- Risky apps control – block risky third-party applications from integrating into your SaaS environment
- Behavioral analysis – Detect anomalous behavior from end-users
- Insider threat prevention – Effectively identify a malicious end-user or one that has compromised credentials
- Brute-force login detection – Provides visibility to brute-force login attempts to your SaaS environment
- Abnormal data download protection – Is a user performing an unsanctioned data download? Identify and prevent data leakage
- Reporting and alerting – Realtime alerts and reporting based on ML intelligence
- Policy-based control – Configure different policies based on different business units or other organizational boundaries.
Spin Technology’s solution is a helping hand for:
- Administrators looking for a seamless, easy-to-use, automated ransomware protection service;
- Business owners who need to protect their company from data losses and prevent losing money and clients’ trust;
- CISOs, who seek a solution that will help their companies to comply with data protection regulations.
You may want to know more about how our platform works. Here we go.
How Does SpinOne Protect You Against Ransomware?
SpinOne provides reliable ransomware protection for your Google Workspace and Office 365 data. More than that, SpinOne is an end-to-end solution. We offer ransomware detection, remediation, and recovery – all in one platform.
Our anti-ransomware process consists of four stages:
- Ransomware Detection Scanner Identifies an Attack.
- System Blocks Access to Google Workspace/Office 365.
- System Identifies Damaged Files.
- Recovery from Backup.
After a ransomware attack is stopped, you’ll get an email notification with details.
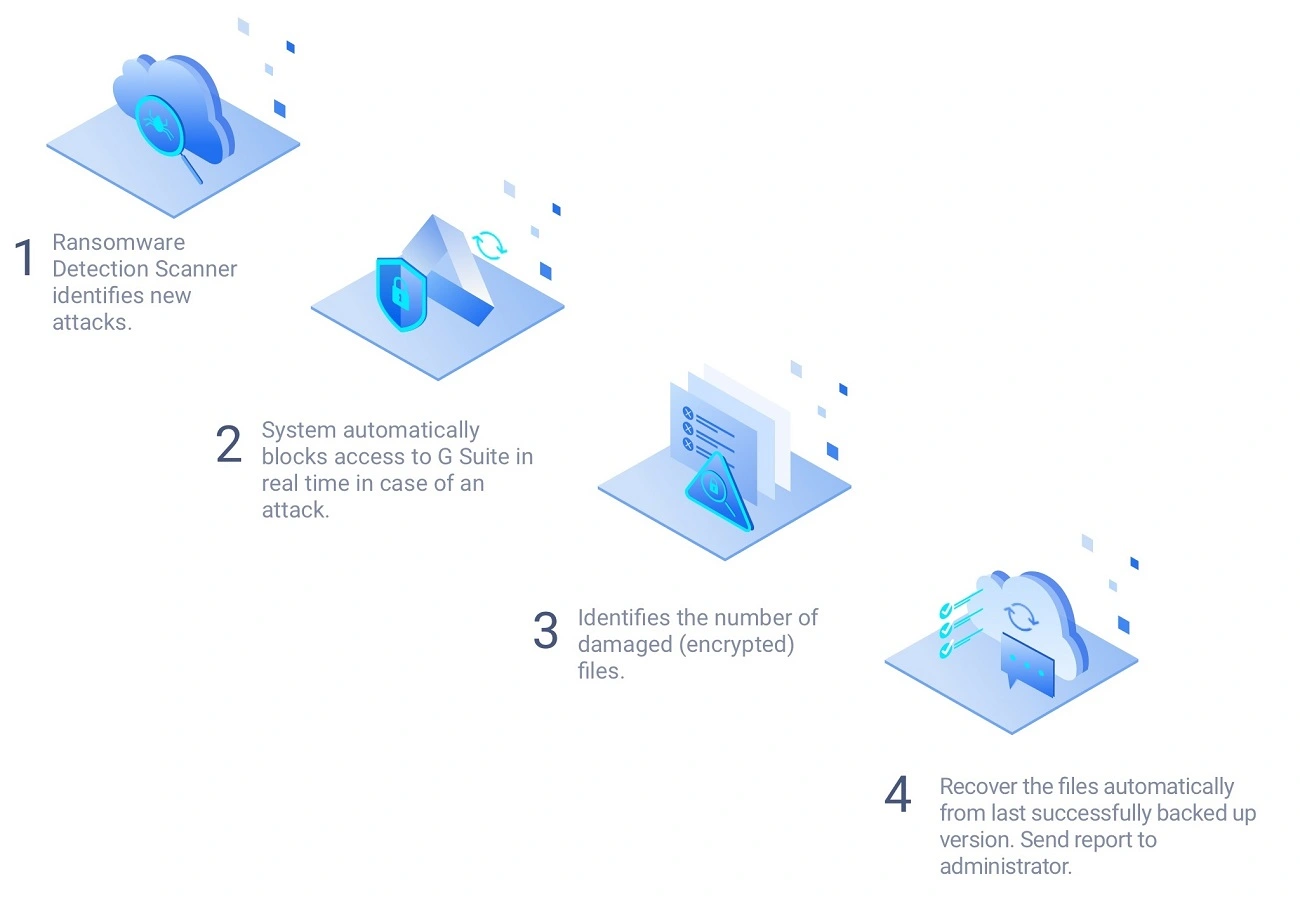
On top of the automated actions carried out by the SpinOne solution, administrators are automatically notified about the ransomware attack and protection against it. Now let’s see what happens at each stage in detail.
Stage 1: Ransomware Detection Scanner Identifies an Attack
Early ransomware detection is crucial, as it allows you to stop ransomware attack before it encrypts all of your files. There are three major methods to detect ransomware:
- Signature detection.
- Abnormal traffic detection.
- Abnormal file behavior detection.
Signature detection allows to recognize dangerous patterns in web traffic/software. This method helps to detect known ransomware by a signature – a unique “fingerprint” of a ransom code. However, the method fails against recent versions. Let’s say, a hacker copies WannaCry code and changes its signature to WannaCry123. Such simple actions are enough to trick signature detection algorithms, often used by antiviruses.
Abnormal traffic detection method helps to detect ransomware by analyzing web traffic. If it is abnormally high or low – it may be an attack. Problem is, it has too high false-positive rate. With this method, security algorithms may mistake some minor abnormalities for a ransomware attack and block the whole account. The impact can be even worse than ransomware itself.
Abnormal file behavior detection is a method of analyzing how files usually act and when they behave anomalously. This method detects ransomware attack as soon as possible, without disrupting your workflow.
What makes this method effective?
- Ability to recognize both known and new ransomware versions.
- Ability to identify the attack source and block it by revoking access to your data.
- All the Office 365/Google Workspace (G Suite) services are available during the whole process.
In our opinion, this is the most accurate, innovative, and stressless way to fight with ransomware in the cloud. That’s why we use it.
Check your recent article to find out more about how we use machine learning in ransomware detection.
Stage 2: System Blocks Access to Google Workspace/Office 365 in Real-Time
Fast detection allows us to stop hackers from carrying out an attack. After an attack is detected, we block it to avoid any further damage. Our algorithms help to prevent ransomware from synchronizing with the cloud and infecting new items in your system.
Stage 3: System Identifies Damaged Files
Identifying the number of encrypted files is the next step. SpinOne provides granular recovery, which means we recover only damaged data, without wasting computing resources on recovering unaffected files.
To identify all IDs of corrupted files we analyze the data, provided by Google Workspace (G Suite)/Microsoft Office 365. Knowing the IDs, we can restore damaged files from a safe backup version.
Stage 4: Recovery from Backup
Some of your files get encrypted during a ransomware attack. Backup is a simple, yet effective solution to get them back. Backup is a safe copy of your data, stored separately from the original data. The features of our backup include:
- Advanced encryption.
- Automated backup up to 3 times/day to cloud storage of your choice: GCP (Google), AWS (Amazon), and Azure (Microsoft).
- Unlimited storage.
- Indefinite retention.
- Several data versions to choose for recovery
- Granular recovery – recovery takes less time, as only damaged files are restored from backup
SpinOne follows the recommendations provided by ISO/IEC 27002 (internationally-recognized standard of good practice for information security) to ensure your data is reliably recovered in case of a ransomware attack.
How to Protect Your Business From Ransomware with SpinOne
Protecting your data with SpinOne is very easy as our service is an automated end-to-end solution, designed to save your time and effort. How can you start your journey with SpinOne?
Choose the cybersecurity solution you need and sign up for a Free Trial. SpinOne platform offers:
| For Google Workspace Users | $, user/month | For Office 365 users | $, user/month |
| SpinBackup: Backup (Team Drives, Google Drive, Gmail) | 3 | SpinBackup: Backup (OneDrive, Outlook, People, Calendar) | 4 |
| SpinRDR: Backup + Ransomware Protection | 4 | SpinSecurity: Backup + Ransomware Protection | 5 |
| SpinOne: Backup + Ransomware Protection + Apps Audit | 5 |
All solutions have a Free 15 Day Trial.
After signing up, you’ll get access to the SpinOne platform. The protection provided by SpinOne is automated and doesn’t require day-to-day operations from your side. But you may want to explore the platform and customize it to fit your needs, so let’s take a look at our ransomware protection from a user perspective.
Interface
Let’s take a look at SpinOne for Office 365 interface (SpinOne for Google Workspace (G Suite) looks similar). We made the interface as user-friendly as possible. Here you can monitor the security of your data and get information about any attacks you may experience.
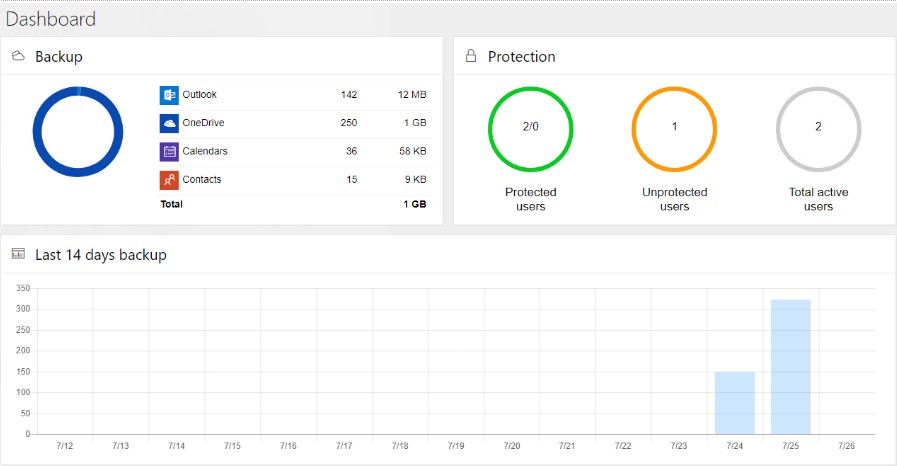
You can customize the platform to align it with your workflow. To do it, go to Settings.
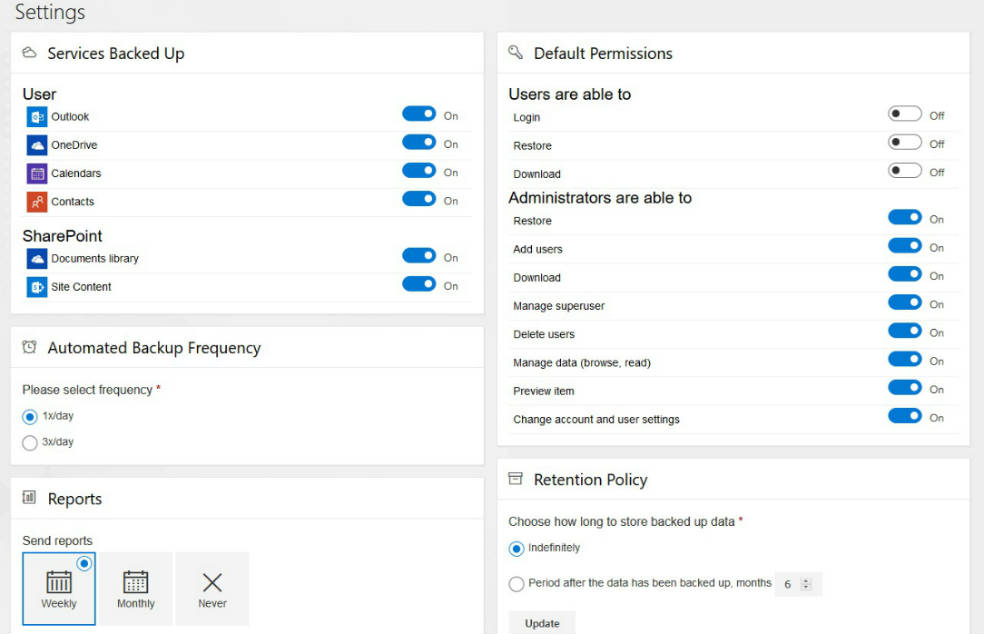
Here you can change the cloud services you want to back up, as well as backup frequency, retention policy, and much more.
Backup and Recovery
The backup/recovery process is automated. If you wish, you can create a backup version or restore data manually (just click the respective buttons). We keep multiple versions of your backed up items. If an attack happens, your backed up data will be restored. For example, let’s take a look at Spinone’s backup functionality.
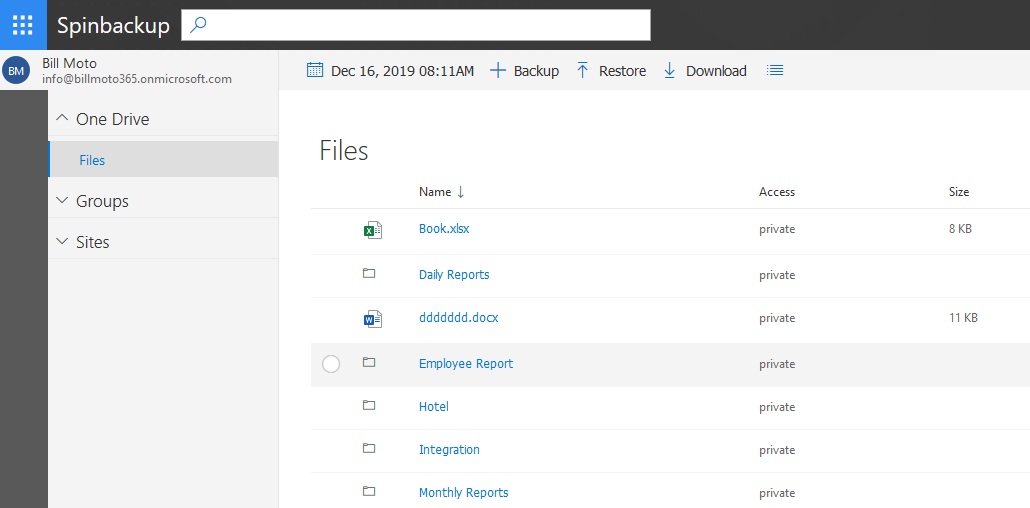
Backup ensures that all files, encrypted by ransomware, will be recovered.
Ransomware Protection
To check the ransomware protection status, you can select Ransomware.
Under normal circumstances, you won’t see much information here. But if the ransomware attack was attempted, you can see the details.
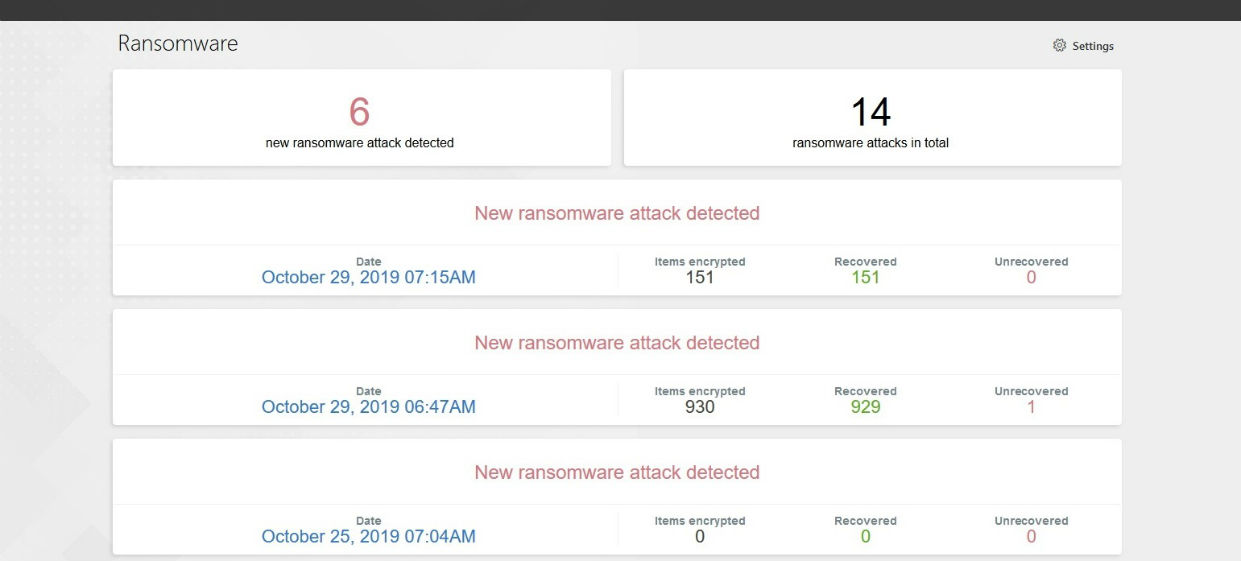
If an attack begins, it is stopped automatically, and your files are restored from safe backups.
You don’t need to monitor this interface all the time. Ransomware protection and recovery are automated. Besides, you’ll get an email notification in case of an attack.
Ransomware does irreversible damage to the company’s reputation and market position. Don’t let ransomware affect your company, sign up for SpinOne Free Trial now!
Was this helpful?
How Can You Maximize SaaS Security Benefits?
Let's get started with a live demo
Latest blog posts
The History and Evolution of Ransomware
January 25, 2024Ransomware has become an efficient tool for illegal money extortion and achieving political goals worldwide.... Read more
Types of Cyber Security Threats in 2024 and How to Prevent Them
December 21, 2023Over the past decade, businesses have become extremely dependent on the IT environment for their... Read more
Ransomware in the Cloud: Challenges and Best Practices
December 13, 2023The rise of SaaS ransomware is quickly becoming a prevalent issue in cybersecurity as it... Read more


