What is Ransomware as a Service (RaaS)

In the past few years, the RaaS model has become not only extremely popular among cybercriminals but also exceptionally successful. What is ransomware as a service, how is it different from previous models, and why is it so efficient?
What is ransomware as a service?
Ransomware-as-a-service (RaaS) is a new model that likens software-as-a-service. The malware is developed by a group of people who then sell subscriptions to it to cyber criminals on the Dark Web.
Check out the history of ransomware
How the RaaS Model Works and How Does Ransomware Get into Your Computer?
The RaaS model doesn’t differ much from your regular SaaS. There are people who build the software, people who develop supporting tools (add-ons), and people who use these tools to infiltrate the systems of their victims.
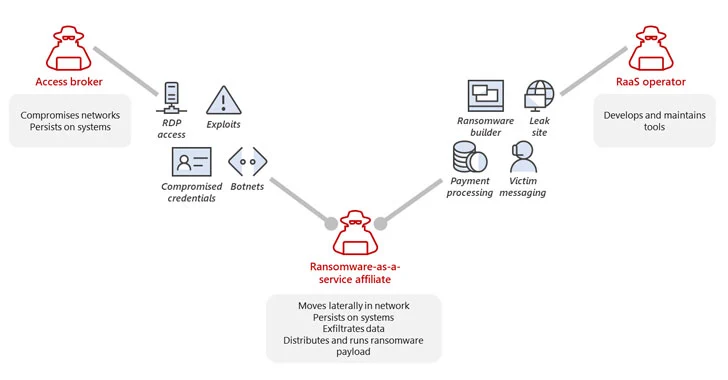
Respectively, there are three main roles within this system: RaaS operators, access brokers, and RaaS affiliates.
Operators create software. It can look like a regular SaaS website. Affiliates pay for the access and use of this service. They can also purchase toolkits to help them attack the systems from access brokers. These are, for example, botnets, compromised credentials, and exploits.
Of these people, only RaaS affiliates conduct attacks. The rest of the criminals earn money by creating possibilities for themselves.
How RaaS Model is different
Cybersecurity experts who have been watching ransomware attacks for over a decade state that ransomware-as-a-service differs significantly in several key aspects.
The first difference is the complexity of the system
At this point in time, we can talk about the ransomware economy. There is a labor division between developers and attackers. There are many RaaS producers who compete with each other for ‘customers,’ the criminals attacking companies. There is the infrastructure that includes websites for leaked data and auxiliary tools to facilitate attacks (like messaging, credentials, etc.).
The second difference is in how criminals conduct an attack
Previously, cybercriminals that used ransomware acted “opportunistically.” They targeted many organizations at once, hoping that some employees within these organizations would fall victim to their tricks or that some targets would have vulnerabilities.
Now the attack techniques have become more “personalized.” Criminals deliberately look for opportunities to exploit vulnerabilities in the company system. They also seek to target employees within organizations that have more privileges than others, for example, top management or Administrators.
Once in the system, criminals search for opportunities to gain even more access and lay their hands on the most sensitive data they can find. One can say they shift their attack strategy depending on the target.
Finally, criminals do not leave the environment immediately upon getting a ransom for encrypted and/or stolen data. They try to retain access and attack repeatedly. They also generate opportunities for this.
In 2022, over one-third of attacks were repeated. And we believe this trend will prevail and this percentage will grow.
Related Link: Ransomware Attacks Surge in 2023: What SMBs Should Know
The third difference is monetization – the primary goal of ransomware
Previously, criminals gained money for the decryption keys. Modern ransomware gangs threaten to leak sensitive information rather than refuse to recover the victim’s data. Furthermore, criminals who do not target organizations directly earn money by providing their ransomware tools, exploits, botnets, etc.
Does RaaS Model Lead to More Ransomware Attacks?
The answer is yes. And there are many reasons for that. First, the division of labor enables criminals to focus on things they do best, be it attacks, software development, access exploits, search, and creation.
Second, collective work helps people to share critical knowledge, have a third-party perspective, and improve through feedback, spot mistakes and work on them. Third, it enables attracting people lacking technical skills and seeking easy money to become part of highly technological cybercrime.
Learn how to protect your business from ransomware as a service.
Was this helpful?
How Can You Maximize SaaS Security Benefits?
Let's get started with a live demo
Latest blog posts
How to Restore A Backup From Google Drive: A Step-by-Step Guide
April 10, 2024Backing up your Google Drive is like making a safety net for the digital part... Read more
Protecting Partner Margins: An Inside Look at the New Spin.AI Partn...
April 2, 2024Google recently announced a 40% reduction in the partner margin for Google Workspace renewals –... Read more
Expert Insights: SaaS Application Data Protection Fundamentals
March 21, 2024SaaS applications appeal to organizations because they make running the application “somebody else’s problem.” However,... Read more