Understanding What is Ransomware Attack: A Brief Guide

The number of ransomware attacks has been growing steadily for the past years. So have the ransom payments. Experts predict this trend to continue. In this article, we explain what a ransomware attack is and how to protect your data.
Ransomware Basics
Ransomware is a type of malware that encrypts files in a system. It is impossible to retrieve data from them without a decryption key which hackers can provide for the victim in exchange for a hefty sum of money. Recently we’ve seen many new tactics that basically hold the data “hostage” to ensure the ransom is paid.
The first ransomware attack was carried out with AIDS Trojan Horse by evolutionary biologist Dr. Joseph Popp in 1989. He demanded as little as $189 in exchange for the decryption key. Today ransomware payments average in millions of dollars.
Decrypting the files is possible, however, it is a very long and expensive process. The companies that fell victim to ransomware cannot afford to wait for such a long period for their mission-critical data to be recovered. That’s why they usually choose to pay.
Several initiatives to battle this type of malware have been collecting the decryption keys and have made them publicly available for free. Unfortunately, dozens of new ransomware strains emerge every year because it’s very easy to develop.
Ransomware Types
Since its first introduction 30 years ago, ransomware has evolved into one of the most efficient cybercrime tools. Today there are many ransomware types that differ in their impact on the system, their attack type, and extortion techniques.
The most popular ransomware types include:
- Cloud (encrypts cloud applications)
- Crypto (encrypts files in the system)
- Full encryption (encrypts all the data)
- Leakware (steals data before encrypting)
- Ransomware-as-a-service (hackers buy subscriptions to ransomware apps).
How Ransomware Works
Ransomware infiltrates the secured IT system via different entry points. Once there it begins the file encrypting process. Often it happens outside business hours to ensure that the malware has time to affect as many files in the system as possible before anyone notices and takes any actions.
On-prem ransomware is a downloadable software. Cloud ransomware is a SaaS application that people access using OAuth authentication. For example, a victim’s company uses Google Workspace as a cloud office suite. The victim logs into a web application using their work account assuming it is a legitimate app. The app requests permission to edit data. Once the victim has given those permissions, ransomware can start the process of data encryption.
Ransomware attack vectors
Ransomware gets into a victim’s cloud or on-prem system via different “entry points.” There are 4 most popular ransomware attack vectors:
1. Social engineering
This attack vector is probably the most popular one. Social engineering is an attack on the weakest point in any system’s security – the human. In a nutshell, a hacker manipulates people into doing something they do not want to do. Examples include downloading malicious software from email or providing their credentials in a fake app that imitates a legitimate application.
The most widespread social engineering attacks are:
- Phishing emails (and their different subtypes, like CEO fraud) with a downloadable file or a link to a malicious
- Infected USB flash drives (planted in the office).
This type of attack is carried out in the cloud and on-prem systems.
2. Botnets
Some computers become infected with trojans or other malware due to the lack of antivirus software and visiting risky websites. As a result, they can become a part of a large botnet. At some point, the owner of the botnet might choose to infect the computer with ransomware if they decide that a victim can pay.
3. Account hijack
In certain cases, hackers can steal the credentials of one or multiple accounts in the system to get access to it. There are different ways in which a hacker can “guess” these credentials. It includes getting the right email address. This is easy as many email addresses are either provided online by the company itself or can be purchased from firms that sell outreach lists to sales organizations or marketers.
The password might be trickier to guess. However, the lists of the most popular passwords are available online. According to one such list, there are 4.5M people who use “123456” and another 4M using “admin.”
The two most popular techniques are credential stuffing, keyloggers, and password spraying.
4. Zero-day attacks
A zero-day attack occurs when hackers find a vulnerability in a legitimate SaaS application and exploit it to get access to its user data and IT system to infect it with ransomware. Zero-day attacks gained momentum after most businesses had shifted to the cloud.
Ransomware Trends and Attack Examples
The battle against ransomware is likened to an arms race. As cybersecurity experts come up with new strategies and tools to battle ransomware, hackers invent new ways to make sure their victims pay.
The most recent ransomware trends include:
- Multiple extortion;
- Intermittent encryption;
- Crime reporting.
Multiple extortion includes data theft with the subsequent data exposure to the public or on the dark web. In double extortion, criminals only blackmail the victim of the attack. In triple extortion, they also threaten people whose data they have stolen from the victim of the attack. In quadruple extortion, they also threaten to unleash a DDoS attack on the public-facing servers of the victim.
Intermittent encryption is the type of encryption that only targets some of the files in the system (e.g., containing certain keywords or having a certain size). It ensures a faster attack.
Crime reporting is when a ransomware gang reports to the authorities about their successful attack. In many countries, companies are mandated by the law to inform a certain government agency about cyber incidents (e.g., SEC in the US).
Some companies try to swipe the ugly truth under the carpet in the hope of avoiding reputational losses and legal implications. Cybercriminals can now threaten to report the crime as leverage in their negotiations with the victim. The disclosure of the attack can also pressure victims to pay ransom.
This tactic is a new thing that emerged in November 2023. It is not yet clear whether it will become a new trend or not. However, in our opinion, it will as there is a great potential to manipulate it in one way or another.
Examples of impactful ransomware attacks in 2023 include:
Check out ransomware examples from the previous years.
Download a full list of ransomware attacks reported on the media.
Ransomware Prevention Tips for Your Organization
In this section, we discuss the best practices for safeguarding your business systems against ransomware. Get our full guide on ransomware prevention.
Employee training and awareness
As mentioned above, your users will be your weakest link in the security system. People make errors if they’re under stress, have their attention elsewhere, or simply lack knowledge. Empower them with information about ransomware, how it works, and proliferates.
Employee awareness is the first layer of defense against ransomware.
Regular data backup
Data backup is essential when you’re dealing with malware that can cause a massive data loss in your system. You can always recover data once you eliminated the attack source. Keep in mind though, that data recovery will take weeks in the cloud environments.
Strong access control
Imposing multifactor authentication, and strong passwords, and making users change them regularly can minimize the risk of account hijacking. However, access control doesn’t end here.
The zero-trust approach should be your next step. This approach stipulates that every user in your system should have minimal access to the data, just enough to do their job, not more. It will minimize the risk of data extortion in case your hacker uses an account hijack.
Third-party apps control
The control over the applications that have OAuth access to your data can prevent SaaS ransomware from accessing your system. It can also eliminate the risky applications that don’t have good security and don’t patch regularly (and thus are more susceptible to vulnerability exploits).
Third-party ransomware prevention tools
Third-party ransomware prevention tools will become your last layer of defense in case all the previous defenses fail. We suggest using AI-based solutions that analyze data behavior in the system. These tools have the least number of false positives and can detect an attack minutes after it begins.
Learn how to choose the ransomware prevention tool for your organization.
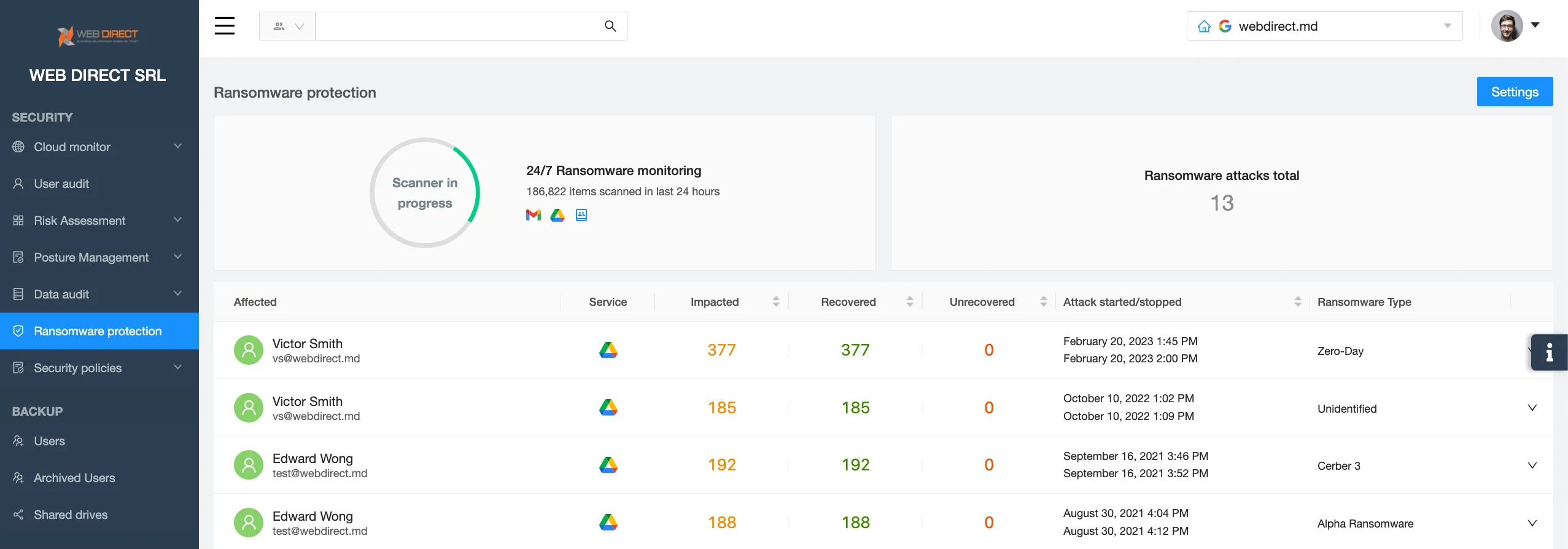
SpinOne – the Ultimate Ransomware Protection Solution
SpinOne SaaS Ransomware Detection and Response is the ultimate solution to battle cloud ransomware that infects Microsoft 365 and Google Workspace.
SpinOne utilizes AI that monitors your data behavior 24/7 and detects a ransomware attack within minutes after it has begun. The tool immediately alerts your IT security team. Next, it identifies the source of the attack and revokes the ransomware’s access to your system.
After the attack has been successfully terminated, SpinOne recovers the data from an in-built backup solution protected from ransomware intrusion. All these steps are done automatically without any human intervention. Usually, by the time your IT security team has logged in to the system, the attack is over and the data is recovered.
FAQ
What are some popular ransomware variants?
Some of the most infamous ransomware variants so far include:
WannaCry. Notorious for its global impact in 2017, exploiting Windows vulnerability and spreading rapidly.
Locky. Known for encrypting files with the .locky extension and distributing through malicious email attachments.
CryptoLocker. Originating in 2013, it stands as one of the initial and notable ransomware variations that required payments in Bitcoin.
Ryuk. Targets large organizations and demands high ransom payments. Often associated with advanced persistent threat (APT) actors.
Conti. A variant of Ryuk, Conti is known for its association with high-profile attacks on healthcare organizations.
NotPetya (ExPetr). Initially thought to be a variant of Petya, NotPetya turned out to be a destructive wiper disguised as ransomware.
How can I protect against ransomware?
To protect your organization from ransomware, do the following:
Defend against prevalent ransomware attack vectors by deploying endpoint protection featuring anti-exploit capabilities. Utilize zero-trust network access (ZTNA) to thwart the misuse of compromised credentials. Establish robust user access protocols and authentication policies to reduce the risk of unauthorized data infiltration.
Do regular backups. While backups cannot thwart a ransomware attack, they can mitigate the impact if one occurs. Therefore, consistently create multiple copies of your data using diverse storage mediums, and ensure that at least one of these copies is stored off-site to provide protection against potential physical damage to your on-site systems.
Use technologies that ensure ransomware detection and response. Consider using an automated AI-driven system such as SpinOne Ransomware Protection. SpinOne incorporates AI-based cybersecurity measures that back up and recover files that might have been exposed to ransomware.
Maintain good security hygiene. Ensure timely patching of your applications and regularly review security tool configurations.
How can I reduce the attack surface against ransomware?
Reducing the attack surface is one of the best ways to protect against ransomware. Consider implementing the following best practices to reduce the attack surface against ransomware:
- Assume zero trust. Access to your resources should only be granted once a user has successfully verified their identity and ensured the security of their device.
- Create strong user access protocols and authentication policies. Implement advanced measures like Single Sign-On (SSO) and multi-factor authentication (MFA) to guarantee that only authorized accounts gain access to applications.
- Monitor network activity. Conduct regular scanning of your active domains, IP addresses, endpoints, and usage patterns that may not be readily visible.
- Segment your networks. Perform the network segmentation based on the business role or sensitivity of data to be able to isolate attacks and thereby prevent their spread.
- Update your systems regularly. This would prevent ransomware variants such as WannaCry and REvil from exploiting unpatched software and OS vulnerabilities.
- Encrypt your data. Strong encryption policies will protect data at rest, in storage, and in use from being exposed if attackers get their hands on it.
- Protect your backups. Use strict protection protocols to keep these backups safe from those who might harm you.
- Train your workforce about how to spot phishing, social engineering, and other types of malicious activity.
Can you provide some examples of ransomware attacks?
Some of the most infamous examples of the ransomware attacks of recent years include the following:
- Ransomware attack on US Marshals Service, February 2023. The breach affected a computer system containing sensitive law enforcement data. Stolen data comprised employees’ personally identifiable information, returns from legal processes, administrative details, and personally identifiable information related to subjects of USMS investigations and third parties.
- DarkSide ransomware attack on the Colonial Pipeline (May 2021, $ 4,4, million lost). The company, which operates a major fuel pipeline in the United States, fell victim to the DarkSide ransomware. The attack disrupted the pipeline’s operations, leading to temporary shutdowns and causing significant disruptions in fuel supply along the U.S. East Coast. The attackers demanded a ransom payment in Bitcoin. The incident highlighted the vulnerabilities of critical infrastructure to cyber threats and prompted discussions on cybersecurity measures and incident response strategies for such crucial systems.
- NotPetya ransomware attack on Ukraine (2017, $10 billion lost globally). While over 60 nations experienced the impact, the attack mainly targeted France, Germany, and Ukraine. Ukraine bore the brunt of these attacks, sustaining about 80% of the attacks. The cyber incident affected the country’s computer systems, along with networks managed by private firms and electric utilities.
What should I do if I’m a victim of a ransomware attack?
Refer to CISA best practices below to effectively mitigate the risk associated with ransomware and facilitate a well-coordinated and streamlined response to a ransomware incident within your organization:
- Determine which systems were impacted, and immediately isolate them.
- If you cannot disconnect devices from the network, shut them down to prevent the ransomware infection from spreading further.
- Report the incident to law enforcement agencies, such as local police and cybercrime units.
- Do not pay the ransom. Paying does not guarantee the recovery of files, and it may encourage further criminal activities.
- Assess the damage by determining which systems and data are affected. This assessment is crucial for recovery planning.
- Follow notification requirements according to your cyber incident response plan to involve internal and external teams and stakeholders. Ensure they comprehend their roles in aiding the mitigation, response, and recovery efforts following the incident.
- Take a system image and memory capture of a sample of affected devices (e.g., workstations, servers, virtual servers, and cloud servers).
- Apply mitigation steps including restoring data from backups, applying security updates, changing passwords, etc.
Was this helpful?
How Can You Maximize SaaS Security Benefits?
Let's get started with a live demo
Latest blog posts
How to Restore A Backup From Google Drive: A Step-by-Step Guide
April 10, 2024Backing up your Google Drive is like making a safety net for the digital part... Read more
Protecting Partner Margins: An Inside Look at the New Spin.AI Partn...
April 2, 2024Google recently announced a 40% reduction in the partner margin for Google Workspace renewals –... Read more
Expert Insights: SaaS Application Data Protection Fundamentals
March 21, 2024SaaS applications appeal to organizations because they make running the application “somebody else’s problem.” However,... Read more


