What is the Reason for Encrypting Data in a Backup: Uneasy Answer Businesses Need to Hear

Cloud backup security is becoming an increasingly important issue with the extensive cloud technology adoption. What is the reason for encrypting data in a backup? What types of encryption are necessary? How to choose a backup solution that will keep your data secure? Learn in our article.
What is the Reason for Encrypting Data in a Backup?
In traditional on-site backup systems security is mainly a physical concern – ensuring data is backed up in more than one location in case of hardware loss or failure and restricting access to the physical backup media to only trusted employees.
In cloud backup, security concerns are different. In many cloud applications such as G Suite (formerly known as Google Apps), Office 365, and Salesforce, data is created in the cloud and then copied to the backup provider. Cloud backup providers have their own security in place to ensure the security of the physical servers, but data may be vulnerable while it is in transit.
This is why data encryption is the most vital key to cloud security. Encrypted data cannot be accessed in a readable format, even if it is intercepted while in transfer online.
90% of organizations say they have concerns about cloud security and 45% cite security as the main barrier to further cloud adoption, with unauthorized access to data being the main security concern. 65% of those surveyed also recognize that encryption is the most effective security control for cloud data.
Data should be encrypted both in transit and once it reaches the servers of the cloud provider and remains in storage. Storing the data in encrypted format means that if an unauthorized person manages to achieve physical or electronic access to these backup servers, the actual data will still be inaccessible.
Data Encryption in Transit via Communication Channels
Data Encryption Certification
Any communication of data between the client and the cloud provider must be encrypted. Not all encryption algorithms are equal and it’s important to make sure the provider you use is utilizing industry-standard encryption protocols.
Cloud data services should use only protocol TLSv1.1 or higher. Additionally, they should own a security certificate that has been confirmed by a well-known and trusted certification center such as Symantec, VeriSign, Thawte, or GoDaddy.
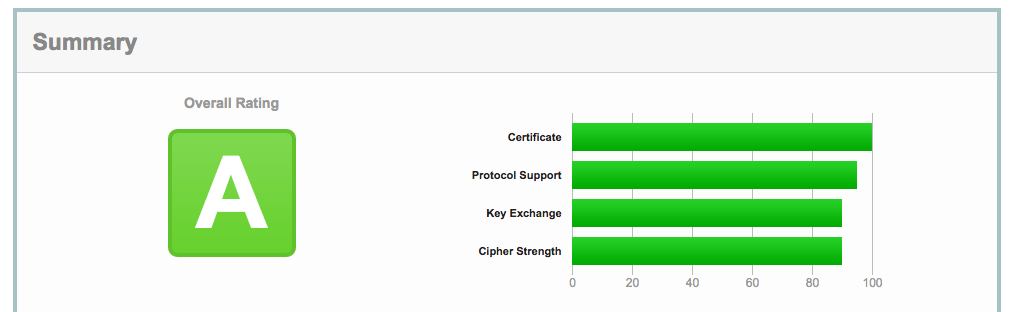
If you want to check the security of the communication channels of any cloud service provider, this is easily checked by visiting SSL labs and using their testing service, which will give you a rating. Reliable and secure providers should have a rating of A or B.
For example, you can see the rating of Spinbackup from SSL labs here:
Data Encryption at Rest
You can determine the overall security of encrypted data by considering four main parameters:
- The algorithm used
- The encryption mode
- The length of the secret key
- Management of the encryption keys
1. Encryption Algorithm
The algorithm used to encrypt the data is the most important aspect of its security.
One of the most well-known and secure algorithms is the AES algorithm, which was adopted as the US national encryption standard in 2001 and has a long history of use in data security. This algorithm was developed by two Belgian cryptographers in 1998. There are currently no known attacks that can be used to read data encrypted with AES and it would take billions of years to access via brute force. The US government has been using AES to protect classified data since 2003.
There is a lot of public information available about this algorithm and it has been thoroughly tested and studied for many years by scientists and cryptography specialists, so this is one of the most popular and secure algorithms used to secure data in cloud applications.
If a cloud provider claims to use their own algorithms for data encryption, this should raise a red flag, as they are unlikely to be as secure as the industry-standard algorithms.
2. Data Encryption Mode
Secondly, the mode by which data is encrypted is another important piece of the overall security.
Encryption mode is a type of add-on encryption algorithm and can help to make your data secure. However, if you choose an unsuitable mode, this could put the security of your data at risk, which may lead to data loss.
Encryption modes have been studied and tested extensively since the earliest modes of operation were developed in 2001 and sometimes new research discovers a weakness in a particular type of encryption mode.
For example, CBC mode (Cipher Block Chaining) was considered safe for many years but serious vulnerabilities have been discovered in it recently and it is now not recommended for securing customer data.
Most experts recognize GCM (Galois / Counter Mode) as the most secure encryption mode currently. Using this model allows you to increase privacy, as well as control the integrity of the encrypted data.
3. Length of the Encryption Key
It is also vital that cloud providers use an encryption key that is long enough to ensure cryptographic security of the data. Keys that are too short can be decrypted more easily.
Computer technology moves very quickly and advances are made in decryption techniques all the time. If a provider is storing sensitive client data, it needs to ensure it will stay intact for several years.
Currently, a key length of 128 bits is sufficient to ensure the data is secured for 2-3 years. Systems that use a 256-bit key can guarantee full data security for many years longer.
4. Management of Encryption Keys
The final aspect of encryption security, which is equally important as the previous three points, is how the provider manages the encryption keys.
Even providers who use the most secure and up-to-date encryption algorithms and technology will not be able to ensure complete security of your data if the encryption keys are not also secured in an adequate way.
Less than ideal scenarios for managing encryption keys that may lead to a data breach include:
- Keys are easily accessible to any employee or potential intruder so that the data can easily be deciphered by anyone who can access the keys.
- Encrypting all the data with one key, which means that all the data is vulnerable if the key is discovered.
- Keys are stored in pure form.
To ensure complete data security it is important that the cloud provider has a key management system in place ensuring that each object is encrypted with an individual key and these keys are not accessible by anyone. Even the most trusted employee should never be granted independent access to encryption keys of customer data.
Spinbackup Data Security
- Spinbackup never asks for your Google password. It communicates with your Google account via OAuth 2.0, Google’s latest and most secure API, developed by Google’s own developers.
- Spinbackup uses Amazon S3 to store users’ backed-up data. Amazon S3 guarantees 99.9% uptime in their Service Level Agreement (SLA). Even if Google is down you will have access to your Google data via your Spinbackup account.
- Spinbackup provides a 256-bit SSL secure certificate to access your user account. All security concerned financial services institutions (banks, brokerage firms, etc) use the same type of certificate.
- Spinbackup does not share any user data or emails with any third party. No other entity will even know that you have an account.
- Recognizing the importance of GDPR compliance, Spinbackup applies best practices, international standards, and follows legal requirements when building an Information Security Management System (ISMS) within the company. We incorporate the highest security standards into every phase of Spinbackup’s software development process, from the outset to completion. Spinbackup employs the highest security and privacy controls, audited regularly in our SOC 2 reports. Spinbackup’s cutting-edge services are driven by a collaborative effort with leading cloud service providers such as Amazon, Google, and Microsoft, whose reliability is globally recognized. Spinbackup follows the recommendations provided by ISO/IEC 27002 to ensure that the information security controls are implemented in Spinbackup.
P.S.: secure your employees’ exit with these tips!
* source: Bitglass.com
Frequently Asked Questions
What are the primary encryption techniques?
Symmetric and asymmetric encryption are the two primary techniques to secure data.
Symmetric encryption involves the utilization of a single key for both encrypting and decrypting data, while asymmetric encryption relies on a pair of keys — a public key for encryption and a private key for decryption.
What are the best types of backup encryption for the cloud?
AES-256 is a symmetric encryption algorithm that uses a 256-bit key.
RSA is an asymmetric encryption algorithm that uses a public key and a private key. The public key is used to encrypt data, and the private key is used to decrypt data. RSA is often used in conjunction with AES-256 to provide a high level of security for cloud backups.
Two-factor authentication (2FA) is an additional security measure that can be used to protect cloud backups from unauthorized access. 2FA requires users to enter a code from their phone in addition to their password when they log in to the cloud backup service.
Why do we encrypt data in cloud backups?
Encrypted data cannot be accessed in a readable format without authorization, even if it is intercepted while transferring online. So, this helps maintain the authenticity, integrity, and confidentiality of information.
In many cloud applications such as GCP, Office 365, and Salesforce, data is created in the cloud and then duplicated to the backup service. While cloud backup providers implement security measures to protect the physical servers, there remains a potential vulnerability during the data transfer.
Was this helpful?
How Can You Maximize SaaS Security Benefits?
Let's get started with a live demo
Latest blog posts
Reducing Browser Extension Risk with Spin.AI Risk Assessment + Perc...
April 24, 2024Spin.AI is collaborating with Perception Point: integrating the Spin.AI Browser Extension Risk Assessment within the... Read more
How to Restore A Backup From Google Drive: A Step-by-Step Guide
April 10, 2024Backing up your Google Drive is like making a safety net for the digital part... Read more
Protecting Partner Margins: An Inside Look at the New Spin.AI Partn...
April 2, 2024Google recently announced a 40% reduction in the partner margin for Google Workspace renewals –... Read more


