Google Workspace Backup and Recovery Solutions
Backup Google Workspace with SpinBackup to protect your data and stay compliant. For enterprises to SMBs.

Advantages of Google Workspace Backup for Enterprise
SpinBackup for Google Workspace helps enterprises improve their SaaS data recovery strategy and compliance. See what sets us apart when backing up your Google Workspace:
Why Backup Google Workspace with SpinBackup?
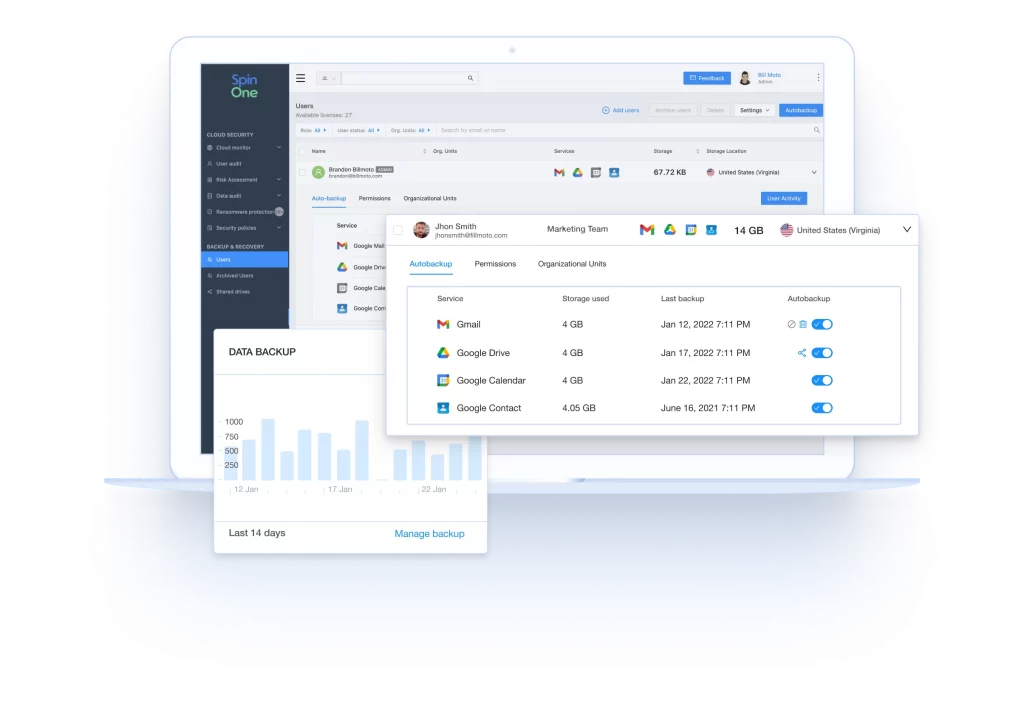
SpinBackup offers comprehensive Google Workspace data protection solutions, including customizable backup retention, automated 3x daily incremental backups to secure cloud storage and full data security with encryption. These features work alongside flexible data restoration options, local downloads, data migration, data loss prevention, instant data location for quick searches, and ongoing monitoring.
- Backed-up services: Gmail, Drive, Contacts, Calendar, Shared Drives
- Automated 1x/3x a day Backup
- Multiple storage locations (AWS, GCP, Azure, custom)
- 99.9% accurate granular recovery
- Fast restoration
- Easy data management
- Archived users
- Flexible retention policies
- Centralized Admin Panel
- 24/7 support: chat, email, phone
- Compliant backup: SOC 2, EU Privacy Shield, and GDPR


Backup Google Workspace: Drive, Gmail, Contacts and More

Backing up GSuite (now Google Workspace) is a critical strategy for businesses to ensure the security and accessibility of their data. Google Workspace is the backbone of many business operations. Despite Google’s robust infrastructure, data within GSuite is still vulnerable to user errors, malicious deletions, ransomware, and other cyber threats. A dedicated backup solution for GSuite not only provides a safety net against these risks but also ensures business continuity by allowing for the quick restoration of lost data.
SpinOne Featured by Pentester Academy

SpinOne Google Workspace Backup was acknowledged by Pentester Academy for simplicity of use and automation

Google Workspace Backup Solutions
Gmail Backup
Despite Gmail’s robust security as a SaaS application, it remains vulnerable to threats like ransomware, man-in-the-middle attacks, and human error. Using SpinBackup, you can quickly recover deleted emails from your Gmail data by performing daily backups. Secure copies of your data are stored in your preferred storage solution, such as Azure, GCP, AWS, or others, protected against ransomware and cybercrime.
In Google Workspace, Google Drive serves as a repository for important corporate information. Cyber threats or accidental deletions can compromise or lose this data. If Google Drive content is lost, there could be significant repercussions, including disruptions in operations and criminal penalties. SpinBackup provides small and medium-sized businesses, educational institutions, and large enterprises with a premier Google Drive backup solution, backed by a 99.9% Service Level Agreement (SLA).
You can use Shared Drive in your organization if you have Google Workspace Enterprise, Google Workspace Business, or Google Workspace for Education editions. Using Team Drives in Google Workspace allows enterprise teams to collaborate securely and efficiently in the cloud. Adding Google Shared Drives Backup through SpinBackup to your data protection plan can strengthen your strategy for preventing data loss.
Google Contacts is essential to various organizational departments, including Sales, Procurement, Public Relations, Customer Success, and Marketing. Even though Google Contacts is a SaaS application, it is susceptible to threats such as ransomware, user errors, corruption, or intentional deletions. SpinBackup solves these vulnerabilities by providing daily backups of your Google Contacts data, which can be restored quickly if any information is lost. Data backups are securely stored in Azure, GCP, AWS, or other storage solutions.
While Google Calendar’s security is robust as a SaaS platform, it remains vulnerable to ransomware, accidental deletions, data corruption, and intentional removals. By backing up your Google Calendar data daily, SpinBackup mitigates these risks, ensuring you can quickly retrieve any lost information. Your data is securely stored in the cloud storage option of your preference, including Azure, GCP, AWS, or others. By capturing a daily snapshot of Google Calendar accounts, SpinBackup offers a straightforward solution for data restoration.
From SMBs to Fortune 500s, Here’s Why Businesses Choose SpinOne
Frequently Asked Questions
Have more questions about SpinOne and Google Workspace backup? Learn more from our FAQ section or contact our support.
Why should I backup my SaaS data?
Google Workspace applies a shared responsibility model for data protection. It prevents data loss due to technical malfunction or attacks. However, Google places responsibility for human error exclusively on its users.
I am looking for a solution to archive the Gmail accounts of former employees and retain their emails. Can you help?
SpinOne have a special offer for archived users. You can safely delete their Google Workspace account and store all the data in our storage. Please connect with one of our sales team members for more information and pricing: info@spintech.ai
What is the 3-2-1 rule?
It’s a backup practice recommended by security experts. You should have 3 copies of your data stored on 2 different media one being stored in a remote location.
Is SpinOne safe?
Yes. SpinOne stores your data on GCP, Azure, AWS, or other storage of your choice. It also encrypts data in use, in transit, and at rest.
What types of Google Workspace data does SpinOne back up?
We backup all types of data and files that are stored on your Google Drive, emails, contacts & calendar entries, as well as metadata (file hierarchy, email folders, permissions).
How to backup Google Workspace?
Backing up your Google Workspace is essential for ensuring the security of your critical SaaS data. While Google provides some native data protection measures, having an additional backup adds an extra layer of security against accidental deletion, data leak or loss, or cyber attacks. Click here for more on how to back up your Google Workspace data with SpinOne.
Streamlined Enterprise Security for SaaS Data
SaaS data security is our top priority. We’ve introduced several processes and regulations to protect your enterprise SaaS data and enhance compliance.






Your SaaS Security Starts with SpinBackup
It only takes a few steps to get started.
Jake Kilian
Technology Support ManagerTed Do
IT ManagerLouis Burdulis
Executive Vice PresidentVal Pashchenko
Information Technology ManagerGeorg Israel
General ManagerMichael Svedeman
Senior Manager, Project DevelopmentGeet Jacobs
Director, Digital OpsRoland Chan
Chief Information Security OfficerJoshua Goss
Senior Director of ITStephan Matter
Technical Operations Manager