Cloud Data Recovery Strategies for SMB

Losing your corporate data stored in cloud solutions can be damaging to your business. In this article, we will talk about cloud data recovery strategies that will help your organization prepare for data loss and avoid major pitfalls of data restoration.
Cloud data loss and recovery
To build your cloud data recovery strategy, you need to understand how data is lost as well as what pitfalls you might come across when attempting to recover data.
Reasons for data loss in cloud solutions:
Cloud SaaS tools like Google Workspace or Microsoft Office 365 are usually well protected from data loss due to brute force attacks or physical damage. So, why is data lost in these cloud tools?
1. Human error
Employees can delete information in documents or files by mistake and never notice it until it is too late. The estimated percentage for human error as the reason for data loss is between 11% and 30%.
2. Man-in-the-middle attack
The deliberate deletion of information in cloud solutions by employees is less frequent. However, its impact can be more severe on business.
3. Ransomware attack
Neither Google Workspace nor Microsoft Office 365 is protected from a ransomware attack. And this cyber event has the greatest effect on corporate data. Ransomware is capable of encrypting all the files stored on Drive, emails, contacts, and even calendar events of a business within a very short period of time.
4. Zero-day attacks
Employees use multiple OAuth applications to boost their productivity. However, these apps might have hidden vulnerabilities. Usually, cybercriminals exploit them to easily access and control your data through the permissions that users give to these applications.
5. Unauthorized access
Unauthorized access to cloud data can be done either through credentials theft or because your users set sharing permissions incorrectly. For example, a file containing sensitive data is available for public access and editing.
Key problems with cloud data recovery
There are several aspects of cloud data recovery that companies should consider before creating a strategy.
1. Limited time for restoration
If data has been soft-deleted, it will be still stored in the Recycle bin. However, the period of storage there is limited. It varies from 2 weeks to one month depending on the cloud solution.
2. Cloud tools don’t back up data
Some businesses perceive solutions like Google Workspace or Microsoft Office 365 as back up for their data stored on-prem. Unfortunately, these tools aren’t backups and they do not store copies of your data elsewhere for emergency recovery.
3. High prices for recovery
Some cloud services can restore your lost data at a price, for example, Salesforce. However, the price can start from $10,000. The catch is that they do not recover all the types of data. Furthermore, the process takes at least one week. Finally, the format of recovery is a CSV file, which isn’t very convenient for administrators.
4. API limits
More and more companies are now purchasing backup and recovery services for their cloud data. However, in case of a massive data loss (like due to a ransomware attack), the recovery can take days or even weeks. It’s because cloud tools connect with a third-party Google Workspace or Microsoft 365 backup via APIs. And every such tool has API limits. The more files you have the longer the process takes.
Summing up, a backup should the essential part of your recovery strategy but not the only one.
Cloud Data Recovery Strategy
In our opinion, a cloud data recovery strategy should be based on the prevention of multiple incidents that make data restoration impossible, extremely difficult, excessively expensive, or too long.
We suggest:
- backup your data,
- protect your cloud from ransomware,
- set up DLP policies,
- control data access,
- monitor OAuth apps.
Let’s take a closer look at each of them.
Backup your data
We strongly recommend using third-party tools to back up and recover your data. Here are some features you should pay attention to:
- Possibility of automated and manual backup
- Places of data storage – look for reliable data centers like AWS, GCP or Azure
- Services that are backed up
- Versioning
- Possibility to make a granular recovery (of one piece of data from a particular point in time)
- Storage limits (some tools provide unlimited storage).
- Possibility to recover data to a different location.
Acquire ransomware protection
As mentioned above, recovery from backups in case of a ransomware attack can take weeks. We suggest acquiring tools that proactively detect the attack and stop it immediately until it has encrypted your entire business data.
For example, SpinRDR ransomware protection doesn’t wait for the attack to finish. It defines the source of the attack, revokes its permissions to edit and access your data, and immediately begins recovery of damaged files. Usually, it takes minutes to detect, stop and recover.
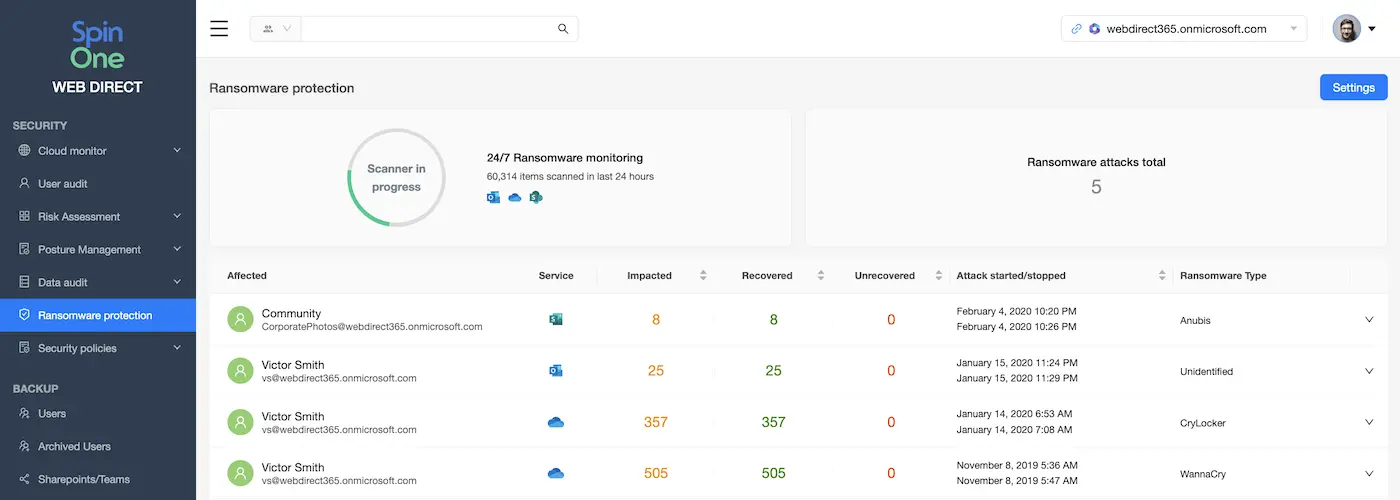
Example of ransomware protection tool – SpinOne
Monitor & control access to your cloud data
We suggest that businesses keep a close eye on unauthorized access to their data. It should be done by monitoring abnormal logins and detecting incorrect sharing settings. Obviously, assigning such tasks to humans in situations of limited resources can be overwhelming. You need to ‘read’ the logs of all user activities throughout the day.
Luckily tools like SpinOne are ‘trained’ to detect such events in the log flow and notify Admins immediately.
Set up DLP policies
Data loss prevention policies can prevent certain adverse cyber events. For example, you can create a policy that notifies users every time they try to publicly share a file. Or disable sharing outside the company at all for everyone except certain people or organizational units.
Unfortunately, some cloud tools have very limited DLPs, for example, Google. However, solutions like SpinOne enable Admins to create more types of policies and set up them more precisely.
Assess OAuth application risks
Detecting and assessing applications can save your business from a nasty cyber incident. However, similar to access monitoring it is a very time-consuming task. Again, there are tools that automate these processes. For example, SpinOne detects applications that have access to your Google Workspace or Microsoft Office 365. Furthermore, it assesses these apps based on 15+ criteria and notifies your Administrators.
Was this helpful?
How Can You Maximize SaaS Security Benefits?
Let's get started with a live demo
Latest blog posts
Expert Insights: How to Select a SaaS Backup Solution (Part 2)
April 26, 2024Welcome back to our blog series on SaaS data protection. Part 1 focused on data... Read more
Google Workspace Backup Solutions Comparison
April 26, 2024The number of Google Workspace (formerly GSuite) backup solutions is overwhelming, and choosing the right... Read more
What’s the Best G Suite Backup Solution?
April 26, 2024In today’s digital age, businesses rely heavily on cloud-based services like Google Suite (G Suite)... Read more


