Disaster Recovery Plan for Enterprise

Now we observe how businesses and non-profits are moving all of their valuable data to the cloud. Backup has become part of their culture. Savvy ones are introducing CASB systems to protect their data from the most popular and dangerous cyber security risks. Nobody knows what kind of new threat may arise. Therefore, the only response in the event of a disaster is to follow a Disaster Recovery Plan.
Disaster Recovery Plan – What Is It?
An IT disaster recovery plan is a set of actions. These actions are designed to restore the continuous operation of business processes. Additionally, they minimize the negative impact on organizational procedures in the event of a disaster for IT infrastructure.
This plan provides information on how to act in risky situations when a company’s data storage security is at risk. In terms of disasters caused by humans, a disaster recovery plan should contain all the procedures necessary to protect data from inappropriate human impacts like internet viruses, spyware, or hacker attack.
The first thing you should do before creating a disaster recovery plan is to assess the potential risks to your IT infrastructure. You should then determine the most vital IT infrastructure elements.
There is no universal disaster recovery plan for all companies as there is no universal approach to protect data and assets. Every company has its own strategy written in its plan. A disaster recovery plan can contain three kinds of measures:
- Preventive or data loss prevention (DLP) measures are aimed to prevent possible threats. For example: blocking dangerous applications from accessing corporate data to prevent malicious data leaks.
- Detective measures help detect a threat of data leak, for example, a virus and use reliable antivirus software to prevent it from penetration in the company’s network.
- Corrective measures are used to restore the company’s data, for example, recovering data from third-party backup storage.
What Does a Disaster Recovery Plan Look Like?
All important issues must be stated in a disaster recovery plan: basic strategy in case of a disaster, people responsible for fulfilling certain tasks, and actions that must be performed. For example, in the case of Google account data loss, it is clearly written in the plan who is responsible to take measures and provide Google account recovery. A well-written disaster recovery plan can save a lot of money, time, and effort and provide the best possible company’s strategy to protect its future.
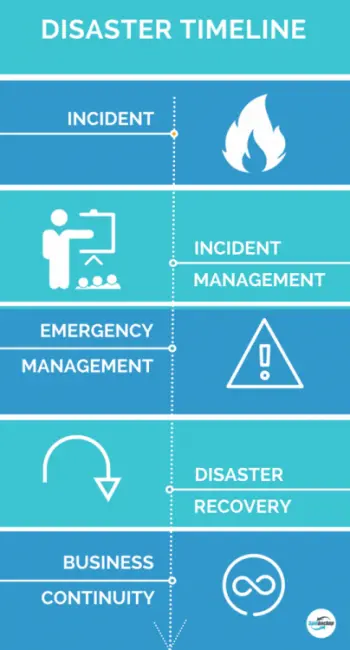
The steps on the timeline represent the main stages of responding to the process. All of them are described and explained in disaster recovery.
A disaster recovery plan usually has the following sections:
- An introduction gives the objective of a disaster recovery plan and indicates who has approved the plan and links to other important documents.
- The roles and responsibilities section shows the responsibilities of team members, their contacts, and their limits of authority in case of a disaster.
- An incident response plan is a step-by-step guide of recommended procedures that are required to recognize and respond to an incident and diminish the negative effects of possible disasters. It is one of the most important parts of a Disaster Recovery Plan.
- Plan activation identifies the cases when a disaster recovery plan should be launched and the procedures of informing disaster recovery members to start participating in the appropriate actions.
- Document history shows when was the document revised and who performed the approvement of revision.
- Procedures show what actions should be performed to bring work back to normal. The more detailed the description of the procedure is, the more successful the disaster recovery plan will be. This section is extremely important in terms of reliability and stable work and should be presented clearly.
- Appendixes show system inventories, application inventories, network asset inventories, contracts and service-level agreements, supplier contact data or any other documentation.
After a disaster recovery plan is written, staff members should be trained to follow the procedures described in the plan. However, it is said that the most successful Disaster Recovery Strategy is one that will never be implemented; therefore, risk avoidance and robust security policies are critical elements of the disaster recovery process and backup is the most reliable disaster recovery way.
Was this helpful?
How Can You Maximize SaaS Security Benefits?
Let's get started with a live demo
Latest blog posts
Securing Critical Infrastructure and Ensuring Economic Resilience 
April 18, 2024Critical infrastructure refers to the systems and assets that are essential for the functioning of... Read more
Protecting Partner Margins: An Inside Look at the New Spin.AI Partn...
April 2, 2024Google recently announced a 40% reduction in the partner margin for Google Workspace renewals –... Read more
Top 10 Salesforce Security Best Practices and Tips
February 28, 2024In the ever-evolving threat landscape, safeguarding sensitive data is paramount. Salesforce, a leading customer relationship... Read more


