How to Implement Data Leak Prevention in Google Workspace

Data leaks in Google Workspace can have severe legal, financial, and reputational implications for the company. Unfortunately, native GW DLP features aren’t enough to protect your data from all the data theft instances. Learn how to implement Data Leak Prevention in Google Workspace to minimize data theft.
Data Leak Prevention (DLP) and its necessity in Google Workspace
Before discussing DLP in detail, we’d like to outline terminology for this post to avoid common confusion around DLP.
First, DLP itself is a tricky term because it encompasses both leak and loss cases. In this article, we’re exclusively discussing data leak prevention in Google Workspace. If you’re more interested in data loss prevention, please read this guide.
Second, many cybersecurity experts differentiate between a data leak and data extortion. The former occurs whenever any unauthorized person accesses and perceives the data. For example, an employee reads a job offer their company sent to their coworker. In another example, a hacker accesses audio recordings of sales calls.
Data extortion happens when an entity copies sensitive data to an external drive. When we say entity, we mean that it could be a human or an application that has access to the data.
Now, a data leak can be as damaging as data extortion. For example, a person might read and memorize the diagnosis and contact data of a patient. They can then use this information for stalking, blackmailing, or emotional abuse.
For the purposes of this article, we’ll be using the term “data leak” to identify both accessing and copying the data by a human or a software program.
What is data leak prevention (DLP)?
Google Workspace stores an immense amount of corporate data. Having it leaked can have severe consequences for a company from financial losses to legal fines to business bankruptcy. If the leaked data contains sensitive information of third parties (e.g., other businesses or individuals) it can also impact them in a damaging way. That’s why data leak prevention is essential.
Data leak prevention is a number of practices and tools that aim to minimize the chances of data leaks. Keep in mind that no tools have a 100% guarantee that a data leak will not happen. Most aim to minimize the probability of this happening.
Google Workspace has a number of DLP features. However, they are not available in all the plans. Furthermore, the existing DLP functionality doesn’t protect against the major sources of data leakage. Let’s take a closer look at this problems:
6 reasons why data is leaked in Google Workspace
Many businesses consider Google Workspace to be a secure solution, and rightfully so. However, there are several ways data can be leaked in Google Workspace:
1. Insider threats
When it comes to data leaks, insider threats can be divided into 2 main categories:
Human error
Human error is one of the most widespread reasons for cyber incidents. Here are some examples of how a data leak can happen within Google Workspace.
An employee can accidentally send sensitive information to the entire company. In July, we saw millions of US Army emails, along with diplomatic info, passwords, and tax information leaked due to a typo in an email address.
A manager shares a confidential document with anyone with a link. Google Workspace Administrator doesn’t take the necessary steps when an employee leaves. And the employee can still access their work account days or even weeks after employment termination.
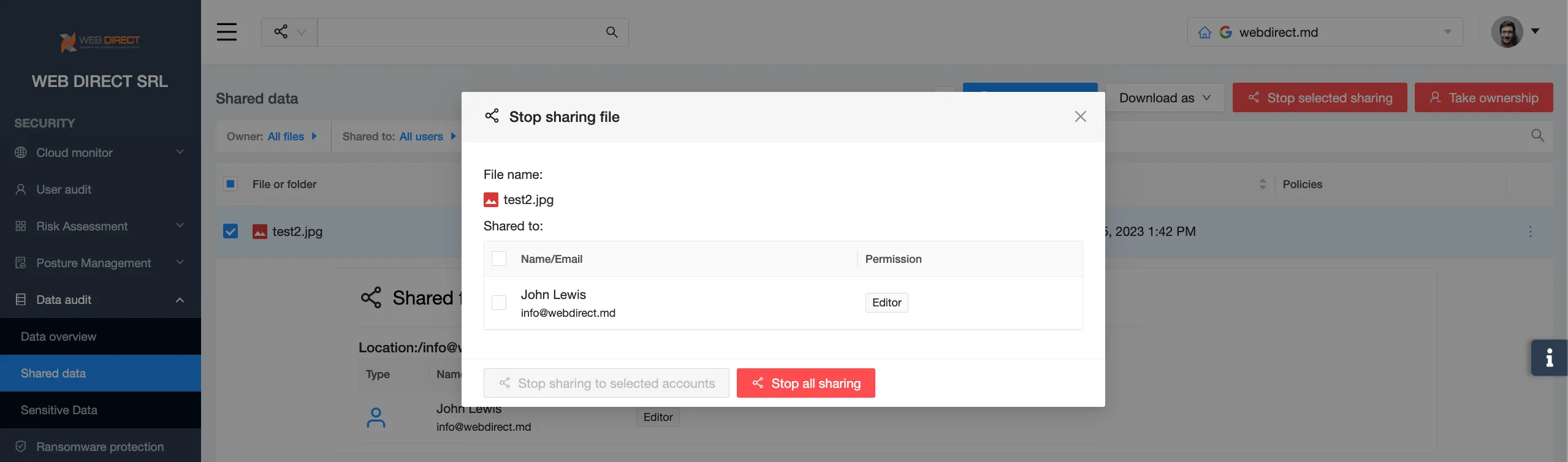
Malicious intent
Malicious intent attacks take place as a result of the conscious actions of users who have access to corporate data. They make a decision to exfiltrate information for various reasons, including illegal profit, revenge, or revealing an organization’s crimes to the public.
Google functionality that helps against leaks caused by insider threats:
- Disable sharing outside the organization.
2. Ransomware attack
Ransomware attacks are another widespread cause of data leaks. In recent years, a double extortion technique has become prevalent. As a result, a significant portion of ransomware attacks include data leaks. Furthermore, some hackers don’t even try to encrypt the data anymore. They chose to threaten the public exposure of the victim’s sensitive information to ensure ransom payment.
Google functionality that helps against leaks caused by ransomware:
- Spam and phishing filters in Gmail.
3. Zero-day attacks
When talking about zero-day attacks, people mean any kind of attack that is carried out via SaaS applications. These apps have access to the corporate data through OAuth. Some permissions include the ability to access and edit an organization’s data.
Hackers are constantly searching for vulnerabilities in applications in order to exploit them and gain access to sensitive data of the apps’ clients.
Google functionality that helps against leaks caused by zero-day attacks:
- App detection and risk assessment.
4. Account hijack
Account hijack is a widespread means to exfiltrate corporate data. Weak passwords and social engineering are two main causes of account hijacking.
Google functionality that helps against leaks caused by account hijacks:
- Strong passwords
- Mandatory monthly password change
- Multifactor authentication.
5. Misconfiguration
Misconfigurations are believed to be one of the primary causes of many cyber attacks. They create “holes” in cloud security that many hackers search for and use. In addition to that, they create a space for human errors.
For example, a company permitted all Google Workspace users to share files outside the organization instead of just client-facing accounts. It creates an “opportunity window” for users to share documents with sensitive data with anyone with the link.
6. Lack of data leak prevention functionality
Overall, Google Workspace has limited data leak prevention functionality. Unfortunately, a native DLP tool isn’t enough to secure all the incidents that cause information theft. For example, anti-spam and anti-phishing functionality doesn’t catch 100% of social engineering emails. Many of them get through and Google Workspace doesn’t have any protection against ransomware once the user has given it access to GW.
Similarly, if a hacker has infiltrated the victim’s system as a result of an account hijack, Google Workspace doesn’t have the functionality to detect them and stop them.
How to implement Data Leak Prevention in Google Workspace
Companies that want to minimize data leaks in Google Workspace need a third-party security solution.
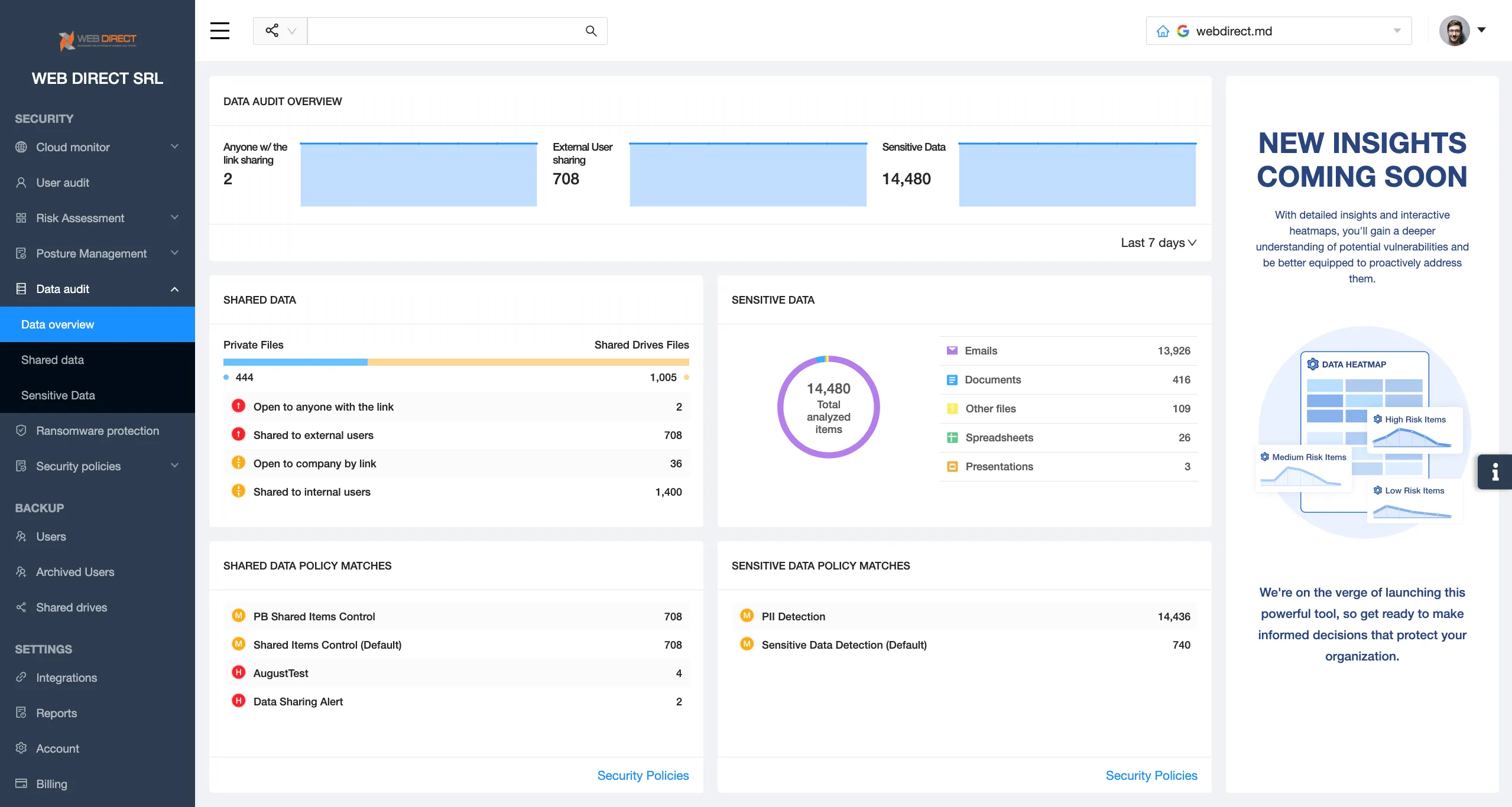
One such solution is SpinOne. This SaaS platform addresses the gaps in Google Workspace security and in many cases acts as the last layer of defense.
Let’s take a look at SpinOne features that minimize the chances of data leaks in GW:
1. Advanced sharing control with the ability to immediately change sharing settings and even take over ownership of the compromised document.
2. User behavior analysis & control. SpinOne uses APIs to detect risky user behaviors like abnormal logins (geography, time, IP), risky applications, and incorrect sharing.
3. Data behavior analysis & control. SpinOne can alert and stop activities with data that can signify data theft, for example, Drive download.
4. Application detection and risk assessment. SpinOne’s functionality has many more features than a similar functionality by Google Workspace. For example, SpinOne has 15 different criteria for risk assessment and it can automatically block apps that don’t meet certain requirements.
5. Ransomware protection. SpinOne uses AI to analyze data behavior in Google Workspace and detect one that matches a ransomware attack. It then detects the source of the attack, revokes its access to the company’s GW and restores the files that have already been encrypted. As a result, SpinOne minimizes downtime by 99% from several weeks to several hours.
Minimize data leaks in your Google Workspace. Try SpinDLP
FAQ
Does Google Workspace have DLP?
How do I implement DLP in Google Workspace?
It’s best to combine the native DLP functionality with third-party tools that cover the gaps in data leak prevention.
Yes, however, not all plans have it, and the existing DLP features do not address all the instances of DLP.
Why is DLP essential for businesses using Google Workspace?
DLP is essential for businesses using Google Workspace because without it your corporate data can be leaked in the following cyber incidents: human error, malicious attack by a user, ransomware attack, zero-day attack, hackers gaining access to your GW (by hijacking an account or due to cloud misconfiguration).
How does Google Workspace’s native DLP differ from third-party SaaS security solutions?
Google Workspace’s native DLP has fewer data leak prevention features than third-party SaaS security solutions.
What are the potential consequences for businesses that overlook DLP in their SaaS operations?
The potential consequences for businesses that overlook DLP in their SaaS operations include data theft, downtime, loss of clients, reputational losses, financial losses, non-compliance, and legal implications.
Was this helpful?
How Can You Maximize SaaS Security Benefits?
Let's get started with a live demo
Latest blog posts
Google Workspace Backup Solutions Comparison
April 26, 2024The number of Google Workspace (formerly GSuite) backup solutions is overwhelming, and choosing the right... Read more
What’s the Best Google Workspace Backup Solution?
April 26, 2024In today’s digital age, businesses rely heavily on cloud-based services like Google Workspace (G Suite)... Read more
Reducing Browser Extension Risk with Spin.AI Risk Assessment + Perc...
April 24, 2024Spin.AI is collaborating with Perception Point: integrating the Spin.AI Browser Extension Risk Assessment within the... Read more


