How Secure is Microsoft Office 365 Mobile Device Management?

Businesses actively use Microsoft Microsoft 365 mobile device management for their employees. In this article, we provide its overview and assess its security.
What is Mobile Device Management?
The extensive use of mobile devices in daily business operations has created a new gateway for cybercrimes. The opportunities to damage business are numerous from obtaining employees’ credentials to stealing (and selling) sensitive information to corrupting data and ransom requests.
The entry points for criminals include unsafe internet connections, applications (including those sold on seemingly safe marketplaces), emails, SMS with unsafe links, etc.
The size and the very nature of a touchscreen increase the chances of clicking the wrong link by mistake. The unintended unblocking of the phone (e.g., while carrying it in a pocket) can also wreak havoc.
Finally, because we carry mobile devices all the time, there’s always a risk of leaving them behind somewhere. As a result, a phone can get into the wrong hands with all the sensitive data on it.
Mobile Device Management (MDM for short) is a tool that enables businesses (i.e., IT Admins) to successfully control smartphones and tablets and prevent the security breaches listed above.
Microsoft MDM Solutions
Microsoft has created multiple tools that help businesses build a safe digital environment for essential business processes, such as communication, collaboration on content, project management, etc.
There are two solutions that provide mobile device management for Microsoft 365:
- Basic Mobility & Security
- Microsoft Intune
The former is the built-in functionality of most plans except for Microsoft Intune, Enterprise Mobility & Security E3, and E5. It includes fewer features and applies to fewer devices compared to Intune. The latter has more capabilities, however, it only comes with certain plans like Microsoft Business Premium, Enterprise E3, and E5, etc.
To start using this feature, a super administrator should enable MDM Microsoft 365 on the Setup page. Keep in mind though that it usually takes a few hours to complete. Afterward, you can add mobile devices and policies in the Admin Center.
Once you’ve set up mobile device management for Microsoft 365, you need to make sure that every person in your company adds their smartphone, tablet, or Windows 10 PC to the system.
Luckily, the system enables you to remind the users to do so and notify you of non-compliance. Otherwise, you can restrict access to those who have failed to abide by the rules.
The functionality of Basic Mobility & Security
In this article, we’ll take a short overview of Microsoft Microsoft 365 mobile device management, including Basic Mobility & Security and Intune mobile device management. Please keep in mind that not all the functions work on every declared device.
Availability
Microsoft 365 Apps, Microsoft 365 Business Basic, Microsoft 365 Business Standard, Office 365 E1, Office 365 E3, Office 365 E5, Microsoft 365 Business Premium, Microsoft 365 Firstline 3, Microsoft 365 Enterprise E3, Microsoft 365 Enterprise E5, Microsoft 365 Education A1, Microsoft 365 Education A3, Microsoft 365 Education A5
Device compatibility
iOS 11.0 and later versions; Windows 8.1 & 8.1 RT, 10 and 10 Mobile, Android 5.0 and later versions
Apps
Outlook, OneDrive, Word, Excel, PowerPoint; Microsoft 365 mobile
Policies
- Enforce encryption on devices
- Prevent jailbreak and rooting
- Manage email profile options
- Wipe the corporate data from a mobile remotely
- Configures password requirements
- Control the settings of the cloud, app, system, and device capabilities.
- Control additional settings like Voice dialing
- Control settings supported by Windows
Remote control of Windows 10 devices
You can add devices with installed Windows 10 to your system.
The functionality of Microsoft Intune
You can think of Intune as an “upgrade” of Basic Mobility and Security. It has all the features of the latter. And in addition to that, Intune MDM works on more devices and provides bigger functionality.
Availability
Microsoft 365 Business Premium, Microsoft 365 Firstline 3, Microsoft 365 Enterprise E3, Microsoft 365 Enterprise E5, Microsoft 365 Education A1, Microsoft 365 Education A3, Microsoft 365 Education A5, Microsoft Intune, Enterprise Mobility & Security E3, Enterprise Mobility & Security E5.
Device compatibility
Windows, iOS, Android, Android Samsung KNOX, mac OS, iPad OS
Features
Check out some of the features that are unique to Intune
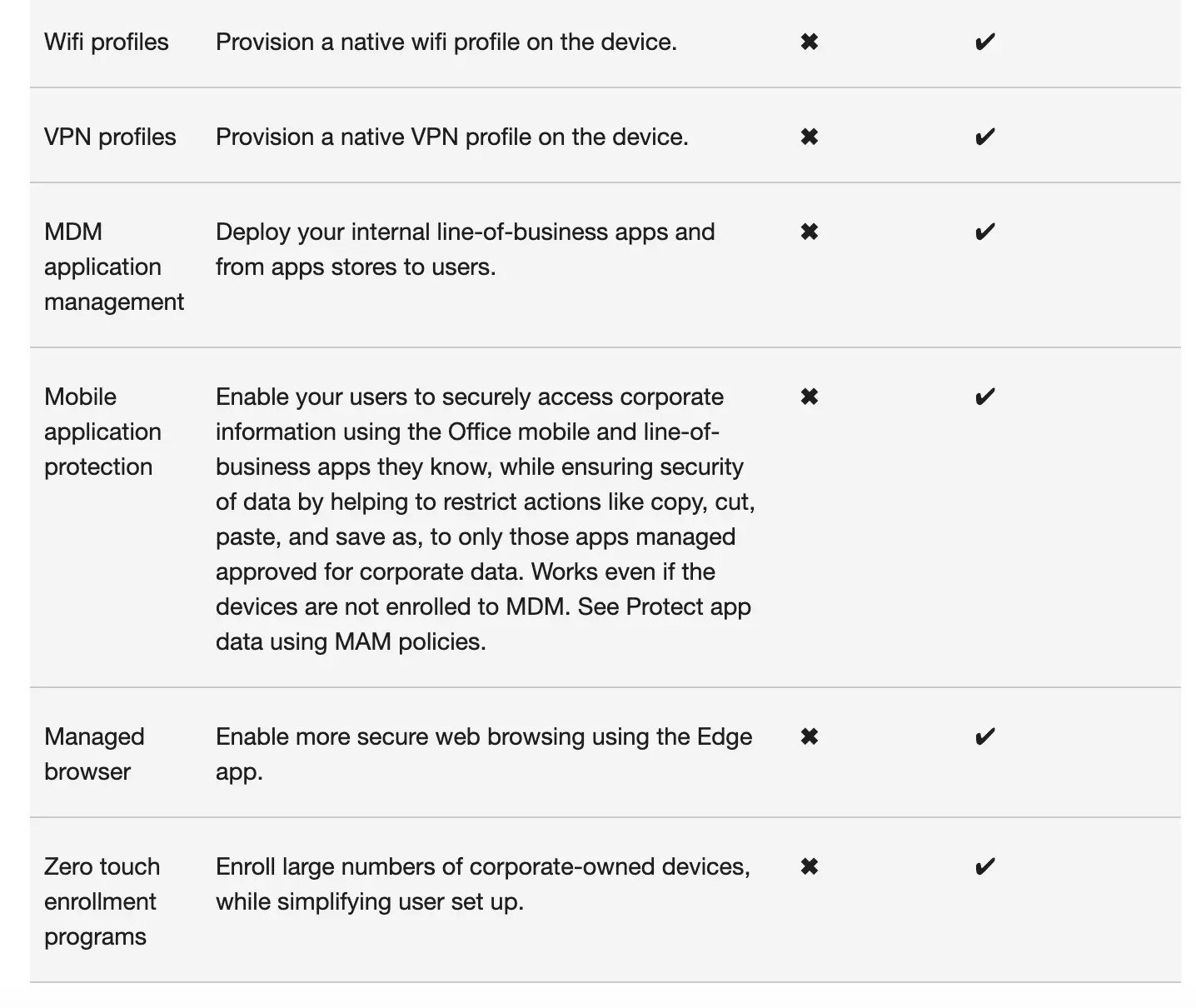
Screenshot from Microsoft Support Center

Data from Microsoft Support Center
Frequently Asked Questions
Ho do I turn off mobile device management in Microsoft 365?
To turn off Basic Mobility and Security, you can either (1) remove groups of people (devices) defined by security groups from the device management policies, or (2) remove the policies themselves.
1. To remove user security groups type https://compliance.microsoft.com/basicmobilityandsecurity in your browser > select a device policy, and select Edit policy > on the Deployment page, select Remove > under Groups, select a security group > select Remove, then Save.
2. To remove Basic Mobility and Security device policies type https://compliance.microsoft.com/basicmobilityandsecurity in your browser > select a device policy, and then select Delete policy > select Yes in the Warning dialog box.
How to remove my device from Microsoft Intune?
Do the following steps to remove your devices from Microsoft intune:
For Windows 10/11, open the Settings app > go to Accounts > Access work or school > Select the account > select Disconnect, then Yes.
For Windows 8.1 PC go to PC Settings > Network > Workplace > Under Workplace Join, select Leave > select Turn off > conform the turn off on the popup window.
Does Microsoft 365 have mobile device management?
Yes, Microsoft 365 offers two mobile device management solutions – Microsoft Intune and Microsoft Basic Mobility & Security. Microsoft Intune is a standalone product included with certain Microsoft 365 plans, while Microsoft Basic Mobility & Security is part of the Microsoft 365 plans.
Was this helpful?
How Can You Maximize SaaS Security Benefits?
Let's get started with a live demo
Latest blog posts
Reducing Browser Extension Risk with Spin.AI Risk Assessment + Perc...
April 24, 2024Spin.AI is collaborating with Perception Point: integrating the Spin.AI Browser Extension Risk Assessment within the... Read more
How to Restore A Backup From Google Drive: A Step-by-Step Guide
April 10, 2024Backing up your Google Drive is like making a safety net for the digital part... Read more
Protecting Partner Margins: An Inside Look at the New Spin.AI Partn...
April 2, 2024Google recently announced a 40% reduction in the partner margin for Google Workspace renewals –... Read more


