Microsoft Office 365 Ransomware: Cybersecurity Guide for SecOps

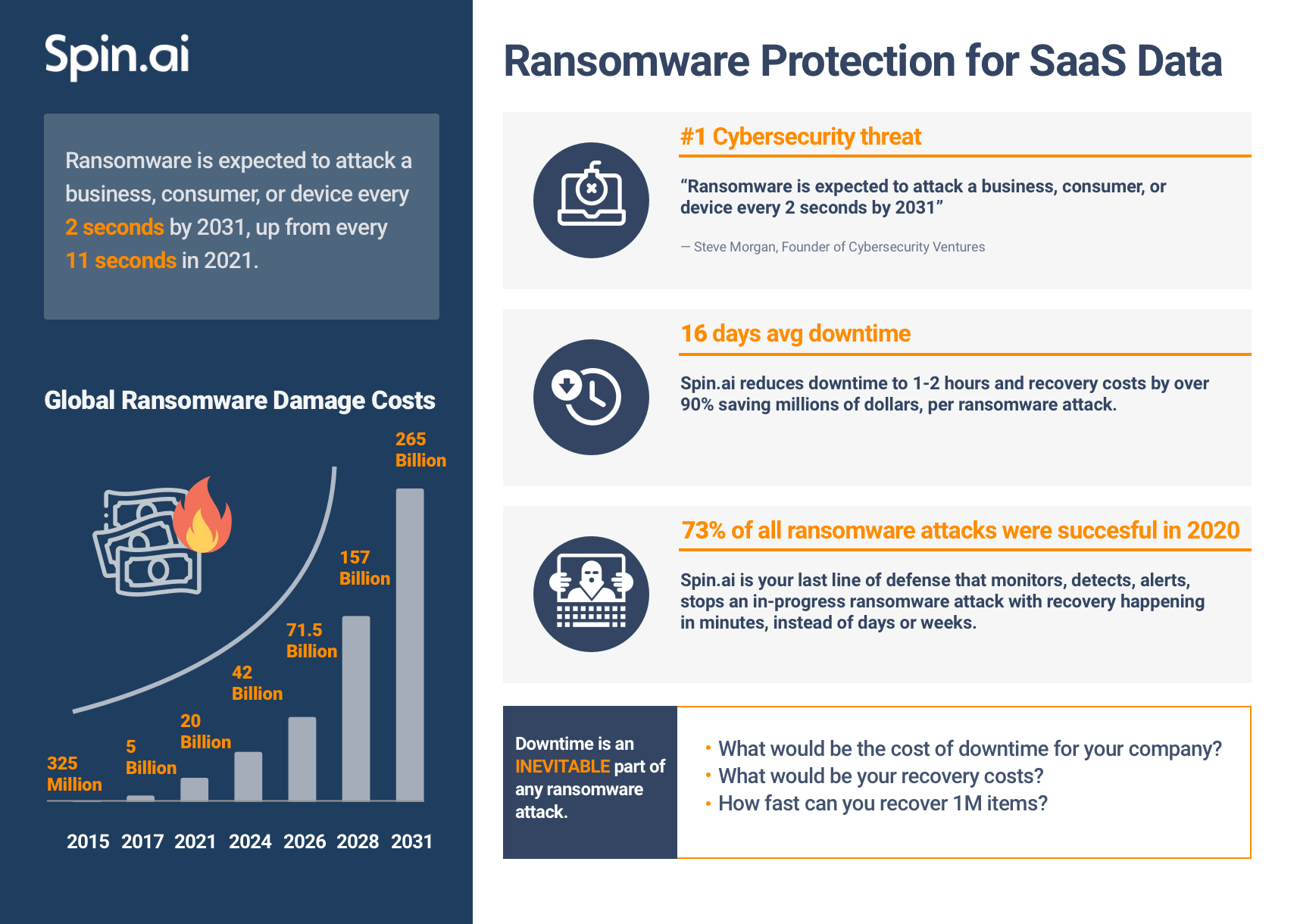
Global pandemics and the transition to WFH operations made businesses more vulnerable to cyber threats, especially ransomware. Global attacks increased by 28 in the third quarter of 2022 compared to the same period in 2021. Moreover, 73% of them are successful. Cloud office suites are one of the most popular targets. And, despite the common belief, Microsoft’s native security features lack sufficient Office 365 ransomware protection.
Meanwhile, the outcomes of the attack can be devastating. Businesses will have to pay ransom and non-compliance penalties. They might also face legal suits from clients. And most importantly, the company will have to deal with the downtime averaging 16.2 days.
In this article, you’ll learn how to recover from the attack and build an efficient anti-ransomware defense for Office 365 environment.
Microsoft Office 365 Ransomware in a Nutshell
Microsoft ransomware encrypts data stored in Microsoft Office 365 services like OneDrive, Outlook, Calendar, Sharepoint, and People. Infecting just one user spreads across all accounts in your tenant and hinders all your business operations. Learn how to defend your OneDrive from ransomware.
Ransomware is easy to code but hard to decrypt unless you have a key. Unfortunately, ransomware is constantly evolving, and new types emerge regularly. That’s why an infected business has a hard choice to make. They either pay the ransom and get the key immediately from criminals or wait weeks or months to crack the malware.
Ransomware can’t infect your Microsoft Office 365 environment unless one of your users gives it permission to access and change your data. There are three main ways to get access permission for the malware:
1. Infected application.
There are thousands of apps in Microsoft AppSource. They request access permissions when users launch an app for the first time. Cybercriminals either create apps or look for vulnerabilities in the existing ones and use them.
2. Phishing email.
The first method can be too hard for cybercriminals. That’s why many of them prefer phishing emails. They trick people into granting access to ransomware in a window that resembles the Microsoft website. See how it’s done in the video below:
3. Man-in-the-middle attack.
This attack works similarly to the previous one. Only the user knows the consequences of their actions precisely.
Microsoft Office 365 Ransomware Recovery
When it comes to ransomware, recovery is the number one underestimated issue for businesses. And to demonstrate that, we’d like to share with you the experience of our sales team.
SpinOne has an anti-ransomware solution for companies operating in Microsoft Office 365. On demo calls with potential clients, we usually ask three questions.
1. What’s your incident response plan for a ransomware attack?
Our team found that 1 in 6 companies relies on legacy antivirus solutions. We can say there’s a problem here. Most legacy antivirus solutions use historical data to detect and stop ransomware as well as to decrypt files. However, they are powerless against a new type of malware.
2. Do you know how to recover files from a ransomware attack?
One in 4 companies uses backup for that purpose. We can say it is a great way to recover encrypted data. Furthermore, our solution uses online backup for ransomware recovery. However, before doing that, your Administrator needs to revoke malware’s access to your Microsoft Office 365. And this is where you lose time, and your business loses money.
3. How long does it take to recover from ransomware for your business?
Most teams can’t answer this question, so we equip them with the known statistics. The ransomware recovery takes 16.2 days on average. And the average cost of downtime can range from $8K per hour for SMBs to $11K per minute for enterprises. The resulting losses can reach millions of dollars.
Microsoft Office 365 Protection against Ransomware
There are multiple solutions that protect against ransomware. We suggest using all of them to minimize the risk:
- Native Microsoft tools
- Educating your employees
- Third-party solutions like backups and anti-ransomware tools
Native ransomware protection in Microsoft Office 365
To defend your data from ransomware, Microsoft provides the next tools:
1. Exchange Online Protection
Since many attacks use email as an entry point, Microsoft has created multiple filters to detect phishing emails, suspicious links, or applications. This is a suitable sieve, but not a perfect one.
One of Spin’s products is a behavior-based ransomware protection tool for Office 365. To train SpinOne’s AI, our development team runs ransomware attacks on a test Microsoft account every month. They send malicious links via email that hit the inbox just well.
2. Cloud App Security
It is a paid service that can help you monitor and control shadow IT. Cloud appl security looks for risky apps that have access to your Office Suite and enable your Admins to revoke it. It helps you minimize the risk of a ransomware attack via applications.
3. Data Loss Policies
You can protect some of your files from editing and deleting. All you need is a proper Data Loss Prevention (DLP) strategy. Unfortunately, for obvious reasons, you can’t apply DLPs to all your files. Which makes this method only partially efficient.
Final thoughts on Microsoft native tools. It would be best if you remembered that using only them isn’t enough. Microsoft sticks to the shared responsibility model:
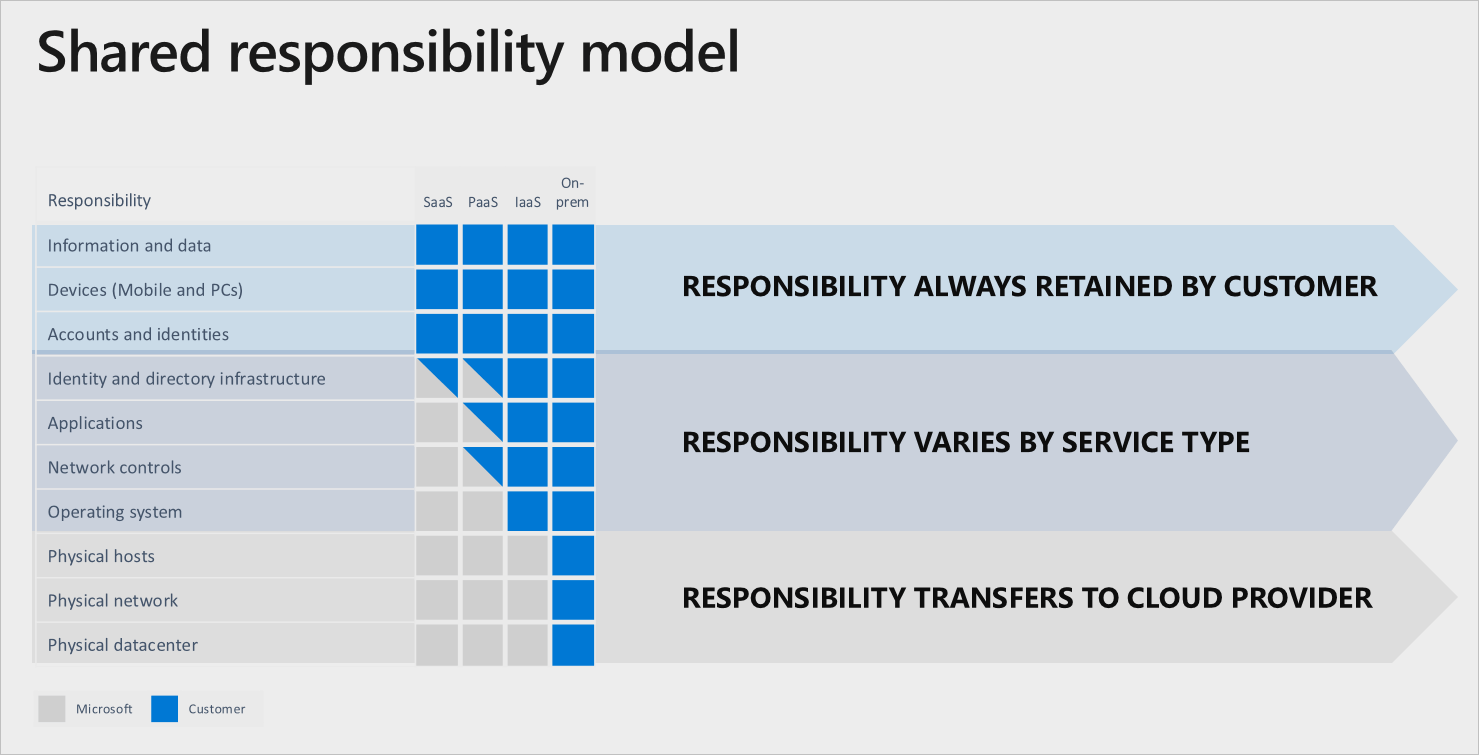
As you can see, information and data will remain your responsibilities as well as accounts and identities. This means that if your employees grant access to ransomware, it will be the responsibility of your business, not Microsoft. That’s why we suggest that you also purchase third-party ransomware protection and provide cybersecurity training to your employees.
Cybersecurity awareness training
Platforms like KnowBe4 provide both education and training. For example, after an employee completed a course on ransomware, they would occasionally send a fake phishing email. Once an employee falls for the scam, the platform sends a notification. In this way, it not only equips your team with knowledge but also keeps them alert.
Remember that training doesn’t give you 100% defense against ransomware. Phishing emails look very realistic. Meanwhile, an employee who is stressed due to family issues or working problems might forget to check regularly and click on a link by mistake.
Third-party tools
As mentioned above, companies use two types of tools: backups and ransomware protection. Let’s take a closer look at each of them.
1. Cloud-to-Cloud Backup
Microsoft Office 365 backup is essential for your business for multiple reasons like compliance or data loss prevention. They create a copy of your data stored in the cloud and keep it intact. Can ransomware infect backups? No. Can backups be used as protection against ransomware? No. They don’t stop ransomware or revoke access to your cloud office. Backups only recover your lost data.
2. Cloud ransomware protection
Most third-party anti-ransomware solutions for Microsoft Office 365 detect ransomware in the cloud-based data they collected from previous attacks. As we mentioned above, they are useless when the new ransomware strikes.
Unlike these tools, SpinSecurity analyzes data behavior in your cloud environment. It detects abnormalities that are characteristic of ransomware. Then it determines the source of an attack and revokes its access to your Office 365. Once the attack stops, SpinSecurity uses its inbuild backup to restore encrypted files.
Learn how SpinSecurity defends Office 365 from ransomware attacks.
Frequently Asked Questions
Can Office 365 be hit with ransomware?
Yes, Office 365 can be vulnerable to ransomware attacks, just like any other software or cloud-based service. While Microsoft takes security measures to protect Office 365 and its users from ransomware, no system can be completely immune to cyber threats.
Does Microsoft have ransomware protection?
Yes, Microsoft has built-in ransomware protection solutions. Microsoft offers Controlled Folder Access for Windows, which helps protect important folders from unauthorized programs, including ransomware.
Microsoft also offers Microsoft Defender for Endpoint – an in-built cloud-based service that helps prevent, detect, investigate, and respond to ransomware attacks and other advanced threats.
There is also a Microsoft 365 Advanced Threat Protection service that provides additional protection against advanced threats, including ransomware
Was this helpful?
How Can You Maximize SaaS Security Benefits?
Let's get started with a live demo
Latest blog posts
Google Workspace Backup Solutions Comparison
April 26, 2024The number of Google Workspace (formerly GSuite) backup solutions is overwhelming, and choosing the right... Read more
What’s the Best Google Workspace Backup Solution?
April 26, 2024In today’s digital age, businesses rely heavily on cloud-based services like Google Workspace (G Suite)... Read more
Reducing Browser Extension Risk with Spin.AI Risk Assessment + Perc...
April 24, 2024Spin.AI is collaborating with Perception Point: integrating the Spin.AI Browser Extension Risk Assessment within the... Read more


