Microsoft Office 365 Security: Ultimate Checklist for Administrators

Microsoft Office 365 Security FAQ
Microsoft Office 365 Security is pivotal to any business using MSO 365 to store and collaborate on their data. This article provides an ultimate Checklist of the Best Practices for Microsoft Office 365 Security. It identifies the security gaps that businesses can close with native and third-party tools.
Over six million data records get lost or stolen every single day. The Cost of a Data Breach Study concluded that businesses pay $148 per one lost or stolen data record. Usually, the cost of lost or stolen data items reaches hundreds or even thousands of dollars per company. You can do the math. How secure is Microsoft 365 in terms of data breaches and data losses? Not as secure as you think it is. Microsoft Office 365 security depends on whether a business owner can foresee potential risks and knows how to prevent them.
Microsoft Office 365 security best practices checklist
1. Set Up a Reliable Password Policy
One of the main O365 security concerns is password carelessness. According to the Verizon Data Breach Investigations Report, more than 70% of workers reuse passwords. And most of them have passwords a hacker with a mediocre password-cracking machine would crack in a few minutes. It’s widespread for people to use the same password for multiple websites. They may also make them too simple so they could remember them easily.
This approach puts your data at huge risk. Imagine for a moment that your employee uses one password to access their profile on Instagram and to sign in to their Microsoft 365 corporate account. What will happen, if someone cracks their password from Instagram? This someone will try this password to enter other systems as well, including your Microsoft 365. At this very moment, your company data gets endangered.
How to secure passwords
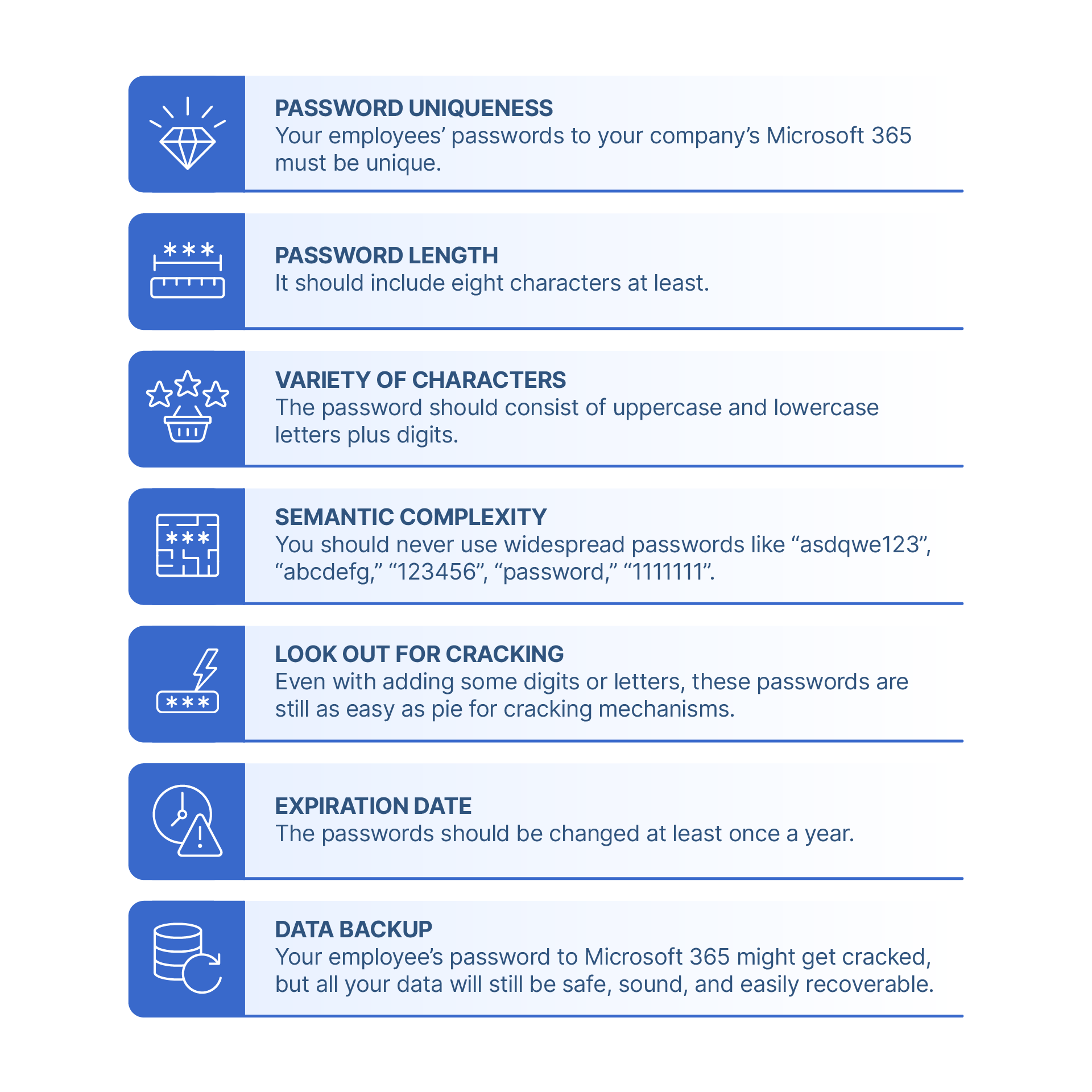
- The password uniqueness. Your employees’ passwords to your company’s Microsoft 365 must be unique.
- The password length. It should include eight characters at least.
- The variety of characters. The password should consist of uppercase and lowercase letters plus digits.
- The semantic complexity. You should never use widespread passwords like “asdqwe123”, “abcdefg,” “123456”, “password,” “1111111”.
- Even with adding some digits or letters, these passwords are still as easy as pie for cracking mechanisms.
- The expiration date. The passwords should be changed at least once a year.
- Data backup. Your employee’s password to Microsoft 365 might get cracked, but all your data will still be safe, sound, and easily
recoverable.
2. Use Up-to-Date Software
By “software” we mean using old versions of Office like Office 2007 / 2010 / 2013 and not checking for the system updates and patches in Microsoft 365. If you are guilty of it too, be ready for some security repercussions. All software has its “expiry date.” At some point, Microsoft stops releasing updates for a given product version, and it gets abandoned. Without regular security updates, the software is unable to resist malicious programs that become more and more sophisticated. Some types of ransomware can even spread across computer networks. In the cloud, you can get the whole system infected with ransomware or a virus. So make sure you don’t leave room for security loopholes
How to secure your data from malware
- One of the best practices for Microsoft 365 security monitoring is to get the latest security updates.
- Back up your data with professional backup services. Only those can guarantee you can recover your information quickly and easily.
3. Secure Information Privacy
Employees share links to documents all the time. Sometimes (intentionally or not) these links could be shared with outsiders who will gladly use the information in it for their benefit. If people outside your organization gain access to the links, they can watch, save, and edit internal company documents. Your internal company information is the most valuable asset, and there are many ways outsiders can benefit from it:
- Infect the document with ransomware or malware to ask for a ransom or just do harm;
- Profit from the data itself: sell the list of customers and suppliers, use sensitive information to steal money, exploit the ideas, and so on.
How to secure your data from malware
To avoid data breaches, you can limit or forbid external linking to some or all documents. To do so, go to Admin > Service Settings > sites and document sharing. Choose to Turn off external sharing.
4. Enabled Multifactor Authentication
Until recently, multi-factor authentication (MFA) was considered as an additional layer of security. Now, it is basic for most companies. With MFA enabled, when a user signs in, they have to enter their login and password and type a code that has been sent on their phone number, or answer a phone call. This way, a system ensures only veritable users can get access to the account. By using only username/password credential authentication, you put your data in danger.
How to enable Multi-Factor Authentication
MFA function is available in Microsoft 365. Just go to the Admin Center, select users and groups, and press Set Up near the Multi-factor Authentication. You can choose particular users or include everyone.
5. Block Sensitive Information from Being Shared
Some information should not be shared under any circumstances. It is sensitive information like credit card numbers and personally identifiable information. If this information is leaked, you can face huge legal implications and fees.
How to block sensitive information from being shared
Define the parameters by which the system can recognize sensitive information. This way the system won’t let this data out or save it to SharePoint/ One Drive. Using Microsoft Microsoft 365 security settings, you can trace and block this type of information from being shared.
6. Provide Security Training for Employees
One of the leading Microsoft Microsoft 365 security issues is not cyberattacks – it’s human error. Human mistakes let cybercriminals into the system, and this is what makes these mistakes so dangerous. Security education for employees is like preventive medicine: it works but is often delayed as a secondary concern. Businesses don’t care about potential risks until they become urgent problems with tremendous potential losses. At the same time, human error is on top of cybersecurity concerns. People’s carelessness and ignorance in security matters cause notorious losses for businesses. People are usually the ones who let the cybercriminals and hackers in the system in the first place. Here are just a few human mistakes that will harm your organization:
- Sharing sensitive and secret company information with third-parties
- Clicking on infected links and attachments
- How to educate your employees
- Accidentally deleting important information
- Being easily tricked by social engineering tactics.
How to Educate Your Employees
Provide your new-coming employees with security awareness training. You have two options: to instruct your security department to prepare it, or just buy one. And of course, take care of your information security with SpinOne. In most cases, having a backup is what makes all the difference!
Why Native Microsoft Office 365 Security Capabilities Aren’t Enough
Many businesses migrate to cloud environments with misconceived ideas regarding the cloud provider’s responsibility. While cloud service providers are responsible to a certain point, ultimately, you, as the customer, are responsible for your data and the security of that data. This dual responsibility is known as the shared responsibility model as defined by today’s cloud providers. What is the shared responsibility model, and how does it affect the security and protection of your data?
Shared responsibility essentially defines where the cloud service provider’s responsibility ends, and the customer’s responsibility begins. For example, in Microsoft’s “7 steps to a holistic security strategy” whitepaper, note the following graphic detailing the shared responsibility of Microsoft and customers. Learn more Why Microsoft Native Cloud Security Capabilities Aren’t Enough.
Open source software
Another popular category of Microsoft 365 Security solutions is open-source (e.g. open source DLP software). These tools are free-off charge, and businesses can easily acquire and deploy them. However, most users state that the available functionality doesn’t cover all the risks in cloud office suites like Google Workspace or Microsoft 365. The accountability is also an issue. We suggest using third-party solutions.
SpinOne – Resolving Microsoft native cloud security gaps
When we perform an overall look at gaps in the security features provided in the Microsoft cloud, it is apparent that organizations need a third-party solution to bolster their Microsoft cloud security. SpinOne provides a comprehensive, next-generation solution, leveraging artificial intelligence (AI) and machine learning (ML) to both protect and secure your business-critical data.
SpinOne provides key features that help organizations have automated security intelligence protecting their environment. These features include:
- Artificial Intelligence-powered ransomware detection
- 24x7x365 automated monitoring
- AI-based ransomware recognition
- Alerts and Analytics
- Stop the ransomware attack
- Automated ransomware restore
The automated ransomware response provided by SpinOne provides world-class ransomware protection. It transcends beyond the simple “reactive” stance cloud service providers take and allows your business to go after ransomware attacking your data proactively. Note the four-step automated ransomware protection approach:
- Detect a ransomware attack
- Stop the encryption process
- Identify encrypted files
- Recover files automatically
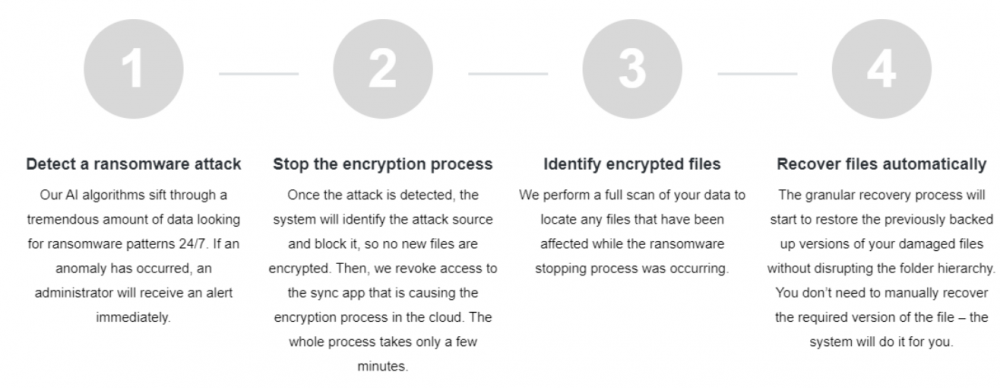
Overview of the SpinOne automated ransomware protection
With SpinOne, your business is not simply notified of a ransomware attack. Instead, the automated processes start to work immediately – automatically stopping the ransomware and recovering any affected data. The automated recovery of business-critical data is made possible by automated backups of your SaaS data that align with your retention policies, not Microsoft’s. In addition, Spin allows unlimited data retention to provide the restore points needed for your business.
Learn more about how SpinOne can bolster your Microsoft 365 security here.
Is Microsoft 365 secure?
It depends on the types of risks and the security features available under your plan. For example, it is more secure than most on-prem deployments when it comes to downtime due to hardware malfunction and some types of hacker attacks. This environment has strong (though not perfect) anti-spam filters and anti-malware protection. However, it is vulnerable to cyber incidents caused by human error.
What are the security risks in Microsoft Office 365?
The main security risks to Microsoft Office 365 include:
- ransomware,
- account hijacking,
- breaches due to security misconfigurations,
- human error,
- attacks that use social engineering,
- risky SaaS applications.
Does Microsoft 365 have security features?
Yes, it does. However, the scope of these features depends on your plan. For example, of all solutions for SMBs, Advanced threat protection is only available for Microsoft 365 Business Premium. It includes endpoint security, sophisticated threats in email links and attachments, restricting apps’ access, and limiting the possibility of employees to copy corporate data.
When it comes to Enterprise plans, Microsoft 365 E3 and F3 do not have all the capabilities of compliance management, Information protection, threat protection, and identity and access management.
How secure is Office 365 encryption?
According to Microsoft, it encrypts your information in transit and at rest. Overall, it is considered very powerful.
How to secure data privacy in Microsoft 365?
Microsoft 365 has powerful tools to secure your data privacy until the breach happens. We suggest using DLP tools that will detect and stop the major incidents related to the data privacy breach, e.g., sharing settings or sending PII via email.
Is Microsoft Office 365 vulnerable to ransomware?
Yes. Cloud ransomware operates as a SaaS application that requires OAuth access to your Microsoft 365 environment. It can only be given by one of your users. Microsoft 365 considers such access safe and allows ransomware to decrypt files.
Was this helpful?
How Can You Maximize SaaS Security Benefits?
Let's get started with a live demo
Latest blog posts
Reducing Browser Extension Risk with Spin.AI Risk Assessment + Perc...
April 24, 2024Spin.AI is collaborating with Perception Point: integrating the Spin.AI Browser Extension Risk Assessment within the... Read more
How to Restore A Backup From Google Drive: A Step-by-Step Guide
April 10, 2024Backing up your Google Drive is like making a safety net for the digital part... Read more
Protecting Partner Margins: An Inside Look at the New Spin.AI Partn...
April 2, 2024Google recently announced a 40% reduction in the partner margin for Google Workspace renewals –... Read more


