Microsoft 365 Ransomware Protection
Fully automated ransomware protection for Exchange Online, OneDrive and Sharepoint. 100% automated. No human involvement required.

Achieve Near-Zero Downtime with SpinOne
SpinOne helps quickly and safely restore your Microsoft 365 data in the event of a ransomware attack. You’ll get ultimate and instant visibility into the scope of the damage. SpinOne can automatically recover your SaaS data, reducing potential downtime from 21 day to just 2 hours.
Microsoft 365 Ransomware Protection for Business Continuity and Compliance
SpinOne can help your company avoid the pain and cost of a cloud ransomware attack. SpinOne provides 24/7 ransomware monitoring and immediately alerts Microsoft 365 admins of any incidents.
SpinOne can automatically identify encrypted files, initiate automated granular recovery of damaged assets without human intervention, ensuring business continuity and protecting you against compliance breaches.
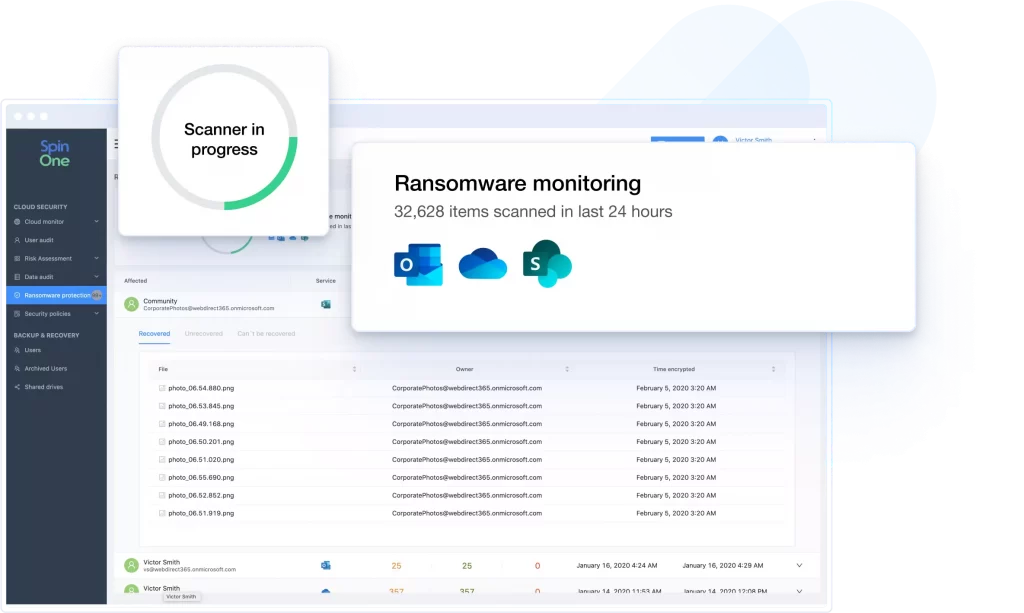
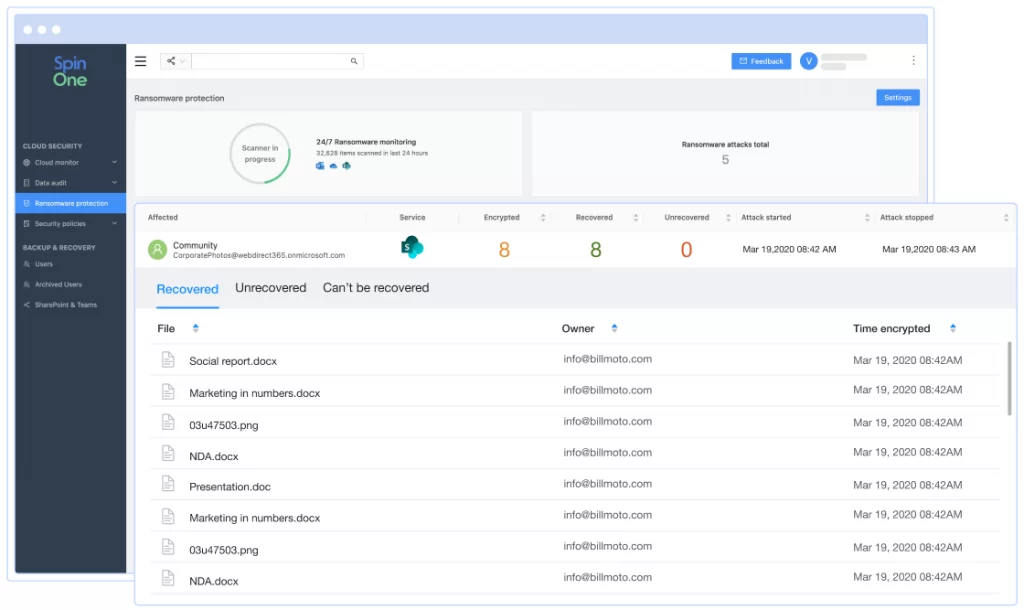
Ransomware Protection
SpinOne is the only solution to integrate pro-active ransomware protection with 24/7 domain monitoring, cloud backup, and flawless restore.
SpinOne combats ransomware, prevents data leak, and can restore your Microsoft 365 data to the most recent version in hours, ensuring that there’s no downtime or data loss.
From SMBs to Fortune 500s, Here’s Why Businesses Choose SpinOne
Related Resources
Frequently Asked Questions
Learn more from our FAQ section or
contact our support team
Why should I backup my SaaS data?
Google Workspace applies shared responsibility model for data protection. It prevents data loss due to technical malfunction or attacks. However, Google place responsibility for the human error exclusively on its users.
I am looking for a solution to archive the Gmail accounts of former employees and retain their emails. Can you help?
SpinOne have a special offer for archived users. You can safely delete their Google Workspace account and store all the data in our storage. Please connect with one of our sales team members for more information and pricing: info@spintech.ai
What is the 3-2-1 rule?
It’s a backup practice recommended by security experts. You should have 3 copies of your data stored on 2 different media one being stored in a remote location.
Is SpinOne safe?
Yes. Our solution takes necessary measures to protect your data, including secure storage on AWS, GCP or Azure, as well as encrypting your data in use, at transit, and at rest.
What types of Microsoft 365 data does SpinOne back up?
All types of files stored on your Google Drive, emails, contacts & calendar entries, as well as meta data (file hierarchy, email folders, permissions).
Streamlined Enterprise Security for SaaS Data
SaaS data security is our top priority. We’ve introduced several processes and regulations to protect your enterprise SaaS data and enhance compliance.






Request a Free Cloud Ransomware Assessment
Pressure test your Google Workspace or Microsoft 365


Jake Kilian
Technology Support ManagerTed Do
IT ManagerLouis Burdulis
Executive Vice PresidentVal Pashchenko
Information Technology ManagerGeorg Israel
General ManagerMichael Svedeman
Senior Manager, Project DevelopmentGeet Jacobs
Director, Digital OpsRoland Chan
Chief Information Security OfficerJoshua Goss
Senior Director of ITStephan Matter
Technical Operations Manager